The SecOps Group CNSP Certified Network Security Practitioner Exam Practice Test
Which of the following is a valid DNS record type?
Answer : D
DNS (Domain Name System) records define how domain names are mapped to various types of data, each serving a specific purpose in network operations. The question asks for valid DNS record types, and all listed options are recognized.
Why D is correct:
A . NAPTR record: The Naming Authority Pointer (NAPTR) record is used for service discovery and mapping domain names to services, protocols, and ports (e.g., in SIP or ENUM systems).
B . SRV record: The Service (SRV) record specifies the hostname and port for specific services (e.g., LDAP, XMPP), aiding in service location.
C . TXT record: The Text (TXT) record stores arbitrary text data, often for SPF, DKIM, or domain verification.
All are valid DNS record types per RFC standards and CNSP documentation, making 'All of the above' the correct answer.
Why other options are incomplete: A, B, or C alone exclude other valid types listed, so D is the most comprehensive response.
In the context of a Unix-based system, where does a daemon process execute in the memory?
Answer : B
In Unix-based systems, memory is divided into two primary regions: kernel space and user space, each serving distinct purposes for process execution and system stability.
Why B is correct: Daemon processes are background services (e.g., sshd, cron) that run with elevated privileges but operate in user space. User space is the memory area allocated for user applications and processes, isolated from kernel space to prevent direct hardware access or system crashes. CNSP highlights that daemons run in user space to maintain system integrity, interacting with the kernel via system calls.
Why other option is incorrect:
A . Kernel space: Kernel space is reserved for the operating system kernel and device drivers, which have unrestricted access to hardware. Running daemons in kernel space would pose significant security and stability risks, and it is not the standard practice in Unix systems.
Where are the password hashes stored in the Linux file system?
Answer : C
In Linux, password hashes are stored in a secure file to protect user authentication data. The evolution of Linux security practices moved password storage from plaintext or weakly protected files to a more secure location.
Why C is correct: The /etc/shadow file is the standard location for storing password hashes in modern Linux systems. This file is readable only by the root user, enhancing security by restricting access. It contains encrypted password hashes (typically using algorithms like SHA-512), along with user details such as password expiration policies. CNSP documentation on Linux security emphasizes /etc/shadow as the authoritative source for password hashes, replacing older methods.
Why other options are incorrect:
A . /etc/passwd: Historically, /etc/passwd stored passwords in plaintext or weakly hashed forms (e.g., using DES), but modern systems use it only for user account information (e.g., UID, GID, home directory) and reference /etc/shadow for hashes.
B . /etc/password: This is not a valid file in the Linux file system; it appears to be a typographical error or misunderstanding, with no recognized role in password storage.
D . /usr/bin/shadow: /usr/bin contains executable binaries, not configuration or data files like password hashes. /etc/shadow is the correct path.
Which one of the following is a phishing email?
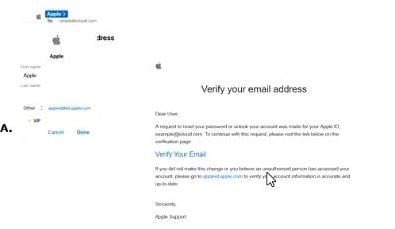
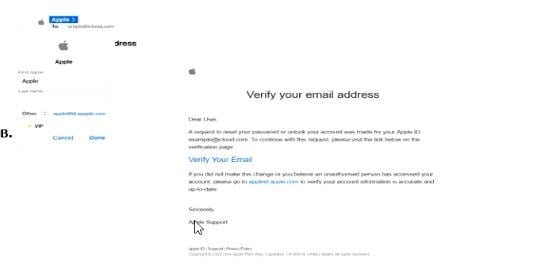
Answer : B
According to the screenshot below, which of the following statements are correct?
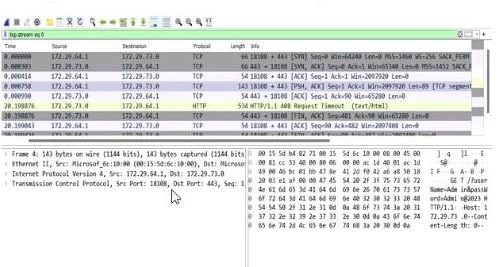
Answer : A
The screenshot is from Wireshark, a network protocol analyzer, displaying captured network traffic. The relevant columns include the source and destination IP addresses, ports, protocol, and additional information about the packets. Let's break down the details:
Destination Port Analysis: The screenshot shows multiple packets with a destination port of 443 (e.g., in the 'Destination' column, entries like '172.72.61.9:443'). Port 443 is the default port for HTTPS (HTTP Secure), which is HTTP traffic encrypted using SSL/TLS. This indicates that the application is communicating over HTTPS.
Protocol Analysis: The 'Protocol' column lists 'TLSv1.2' for most packets (e.g., frame numbers 2000084, 2000086). TLS (Transport Layer Security) is the cryptographic protocol used by HTTPS to secure HTTP communications. This confirms that the traffic is HTTPS, not plain HTTP.
Packet Details: The 'Info' column provides additional context, such as 'Application Data' for TLS packets, indicating encrypted application-layer data (typical of HTTPS). There are also HTTP packets (e.g., frame 2000088), but these are likely part of the HTTPS session (e.g., HTTP/2 over TLS, as noted by 'HTTP2').
Now, let's evaluate the options:
Option A: 'The application is running on port 443 and the HTTPS protocol.'
This is correct. The destination port 443 and the use of TLSv1.2 confirm that the application is using HTTPS. HTTPS is the standard protocol for secure web communication, and port 443 is its designated port. CNSP documentation emphasizes that HTTPS traffic on port 443 indicates a secure application-layer protocol, often used for web applications handling sensitive data.
Option B: 'The credentials have been submitted over the HTTP protocol.'
This is incorrect. HTTP typically uses port 80, but the screenshot shows traffic on port 443 with TLS, indicating HTTPS. Credentials submitted over this connection would be encrypted via HTTPS, not sent in plaintext over HTTP. CNSP highlights the security risks of HTTP for credential submission due to lack of encryption, which isn't the case here.
Option C: 'The credentials have been submitted over the HTTPS protocol.'
While this statement could be true (since HTTPS is in use, any credentials would likely be submitted securely), the question asks for the 'correct' statement based on the screenshot. The screenshot doesn't explicitly show credential submission (e.g., a POST request with form data); it only shows the protocol and port. Option A is more directly supported by the screenshot as it focuses on the application's protocol and port, not the specific action of credential submission. CNSP notes that HTTPS ensures confidentiality, but this option requires more specific evidence of credentials.
Option D: 'The application is running on port 80 and the HTTP protocol.'
This is incorrect. Port 80 is the default for HTTP, but the screenshot clearly shows port 443 and TLS, indicating HTTPS. CNSP documentation contrasts HTTP (port 80, unencrypted) with HTTPS (port 443, encrypted), making this option invalid.
Conclusion: Option A is the most accurate and comprehensive statement directly supported by the screenshot, confirming the application's use of port 443 and HTTPS. While Option C might be true in a broader context, it's less definitive without explicit evidence of credential submission in the captured packets.
Which command will perform a DNS zone transfer of the domain "victim.com" from the nameserver at 10.0.0.1?
Answer : D
A DNS zone transfer replicates an entire DNS zone (a collection of DNS records for a domain) from a primary nameserver to a secondary one, typically for redundancy or load balancing. The AXFR (Authoritative Full Zone Transfer) query type, defined in RFC 1035, facilitates this process. The dig (Domain Information Groper) tool, a staple in Linux/Unix environments, is used to query DNS servers. The correct syntax is:
dig @<nameserver> <domain> axfr
Here, dig @10.0.0.1 victim.com axfr instructs dig to request a zone transfer for 'victim.com' from the nameserver at 10.0.0.1. The @ symbol specifies the target server, overriding the system's default resolver.
Technical Details:
The AXFR query is sent over TCP (port 53), not UDP, due to the potentially large size of zone data, which exceeds UDP's typical 512-byte limit (pre-EDNS0).
Successful execution requires the nameserver to permit zone transfers from the querying IP, often restricted to trusted secondaries via Access Control Lists (ACLs) for security. If restricted, the server responds with a 'REFUSED' error.
Security Implications: Zone transfers expose all DNS records (e.g., A, MX, NS), making them a reconnaissance goldmine for attackers if misconfigured. CNSP likely emphasizes securing DNS servers against unauthorized AXFR requests, using tools like dig to test vulnerabilities.
Why other options are incorrect:
A . dig @10.0.0.1 victim.com axrfr: 'axrfr' is a typographical error. The correct query type is 'axfr.' Executing this would result in a syntax error or an unrecognized query type response from dig.
B . dig @10.0.0.1 victim.com afxr: 'afxr' is another typo, not a valid DNS query type per RFC 1035. dig would fail to interpret this, likely outputting an error like 'unknown query type.'
C . dig @10.0.0.1 victim.com arfxr: 'arfxr' is also invalid, a jumbled version of 'axfr.' It holds no meaning in DNS protocol standards and would fail similarly.
Real-World Context: Penetration testers use dig ... axfr to identify misconfigured DNS servers. For example, dig @ns1.example.com example.com axfr might reveal subdomains or internal IPs if not locked down.
How many usable TCP/UDP ports are there?
Answer : B
TCP (Transmission Control Protocol) and UDP (User Datagram Protocol) port numbers are defined by a 16-bit field in their packet headers, as specified in RFC 793 (TCP) and RFC 768 (UDP). A 16-bit integer ranges from 0 to 65,535, yielding a total of 65,536 possible ports (2^16). However, port 0 is universally reserved across both protocols and is not considered 'usable' for standard network communication. According to the Internet Assigned Numbers Authority (IANA), port 0 is designated for special purposes, such as indicating an invalid or dynamic port assignment in some systems (e.g., when a client requests an ephemeral port). In practice, operating systems and applications avoid binding to port 0 for listening services, and it's often used in error conditions or as a placeholder in protocol implementations (e.g., socket programming).
Thus, the usable port range spans from 1 to 65,535, totaling 65,535 ports. These ports are categorized by IANA into:
Well-Known Ports (0--1023): Reserved for system services (e.g., HTTP on 80/TCP). Note that 0 is still reserved within this range.
Registered Ports (1024--49151): Assigned to user applications.
Dynamic/Ephemeral Ports (49152--65535): Used temporarily by clients.
From a security perspective, understanding the usable port count is critical for firewall configuration, port scanning (e.g., with Nmap), and detecting anomalies (e.g., services binding to unexpected ports). Misconfiguring a system to use port 0 could lead to protocol errors or expose vulnerabilities, though it's rare. The CNSP curriculum likely emphasizes this distinction to ensure practitioners can accurately scope network security assessments.
Why other options are incorrect:
A . 65536: This reflects the total number of possible ports (0--65535), but it includes the reserved port 0, which isn't usable for typical TCP/UDP communication. In security contexts, including port 0 in a count could lead to misconfigured rules or scanning errors.
C . 63535: This is an arbitrary number with no basis in the 16-bit port structure. It might stem from a typo or misunderstanding (e.g., subtracting 2000 from 65535 incorrectly), but it's invalid.
D . 65335: Similarly, this lacks grounding in protocol standards. It could be a miscalculation (e.g., subtracting 200 from 65535), but it doesn't align with TCP/UDP specifications.
Real-World Context: In penetration testing, tools like Nmap scan ports 1--65535 by default, excluding 0 unless explicitly specified (e.g., -p0-65535), reinforcing that 65,535 is the practical usable count.