SCP SC0-451 Tactical Perimeter Defense Exam Practice Test
Network Monitor was run on the Windows Server 2003 during a network session. The exhibit shows the actual contents of the Network Monitor capture file. The Hexadecimal value for the IP protocol and source ports have been circled in the exhibit. The contents of
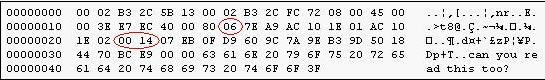
Answer : D
You have been given the task of implementing the wireless solution for your organization's campus. Which two antenna types are best suited for bridge applications connecting two buildings?
Answer : A, B
To verify that your PPTP implementation is working as you intended, you sniff the network after the implementation has been completed. You are looking for specific values in the captures that will indicate to you the type of packets received. You analyze the packets, including headers and payload. PPTP works at which layer of the OSI model?
Answer : B
You have just installed a new Intrusion Detection System in your network. You are concerned that there are functions this system will not be able to perform. What is a reason an IDS cannot manage hardware failures?
Answer : E
If you are configuring your WLAN for security, and you configure the access points with a security feature that the clients do not support, what can you add to the clients to have them participate in the WLAN?
Answer : E
After you implemented your IPSec solution, you wish to run some tests to verify functionality. Which of the following provides confidentiality and authentication when implementing IPSec?
Answer : B
You have just installed ISA Server 2006 on a Windows Server in your network, and you are familiarizing yourself with the new firewall. What are the three basic areas of a newly installed ISA Server 2006 firewall?
Answer : A, D, E