SAP C_ABAPD_2309 SAP Certified Associate - Back-End Developer - ABAP Cloud Exam Practice Test
Which of the following are ABAP Cloud Development Model rules?
Note: There are 2 correct answers to this question.
Answer : A, C
Build ABAP RESTful application programming model-based services. This rule ensures that the ABAP Cloud code follows the state-of-the-art development paradigm for building cloud-ready business services. The ABAP RESTful application programming model (RAP) is a framework that provides a consistent end-to-end programming model for creating, reading, updating, and deleting (CRUD) business dat
Given the following Core Data Service View Entity Data Definition:
1 @AccessControl.authorizationCheck: #NOT_REQUIRED
2 DEFINE VIEW ENTITY demo_flight_info_join
3 AS SELECT
4 FROM scarr AS a
5 LEFT OUTER JOIN scounter AS c
6 LEFT OUTER JOIN sairport AS p
7 ON p.id = c.airport
8 ON a.carrid = c.carrid
9 {
10 a.carrid AS carrier_id,
11 p.id AS airport_id,
12 c.countnum AS counter_number
13 }
In what order will the join statements be executed?
Answer : A
The order in which the join statements will be executed is:
scarr will be joined with scounter first and the result will be joined with sairport.
Therefore, the join statements will be executed as follows:
First, scarr AS a will be joined with scounter AS c using the join condition a.carrid = c.carrid. This means that all the rows from scarr will be included in the result, and only the rows from scounter that have the same value for the carrid field will be included. If there is no matching row from scounter, the countnum field will be filled with an initial value.
Second, the result of the first join will be joined with sairport AS p using the join condition p.id = c.airport. This means that all the rows from the first join will be included in the result, and only the rows from sairport that have the same value for the id field as the airport field from the first join will be included. If there is no matching row from sairport, the id field will be filled with an initial value.
In RESTful Application Programming, a business object contains which parts? Note: There are 2 correct answers to this question.
Answer : A, B
The following are not parts of a business object in RESTful Application Programming, because:
What are the effects of this annotation? Note: There are 2 correct answers to this question.
Answer : A, B
The following code snippet defines a CDS view ZI_FLIGHT_TEXTS with an input parameter p_langu that is annotated with @Environment.systemField: #LANGUAGE:
define view ZI_FLIGHT_TEXTS with parameters p_langu : syst_langu @<Environment.systemField: #LANGUAGE as select from sflight left outer join scarr on sflight.carrid = scarr.carrid left outer join stext on scarr.carrid = stext.carrid { sflight.carrid, sflight.connid, sflight.fldate, scarr.carrname, stext.text as carrtext } where stext.langu = :p_langu
The following code snippet shows how to use the CDS view ZI_FLIGHT_TEXTS in ABAP without specifying the value of p_langu in the WHERE clause. The value of sy-langu will be automatically passed to the CDS view:
SELECT carrid, connid, fldate, carrname, carrtext FROM zi_flight_texts INTO TABLE @DATA(lt_flights).
The following code snippet shows how to use the CDS view ZI_FLIGHT_TEXTS in another CDS view ZI_FLIGHT_REPORT. The value of sy-langu will be automatically passed to the nested CDS view ZI_FLIGHT_TEXTS:
define view ZI_FLIGHT_REPORT with parameters p_langu : syst_langu @<Environment.systemField: #LANGUAGE as select from zi_flight_texts(p_langu) { carrid, connid, fldate, carrname, carrtext, count(*) as flight_count } group by carrid, connid, fldate, carrname, carrtext
The following code snippet shows how to use the CDS view ZI_FLIGHT_TEXTS in ABAP with a specified value of p_langu in the WHERE clause. The value 'E' will be passed to the CDS view instead of the value of sy-langu:
SELECT carrid, connid, fldate, carrname, carrtext FROM zi_flight_texts WHERE p_langu = 'E' INTO TABLE @DATA(lt_flights).
The following code snippet shows how to use the CDS view ZI_FLIGHT_TEXTS in another CDS view ZI_FLIGHT_REPORT with a specified value of p_langu in the WHERE clause. The value 'E' will be passed to the nested CDS view ZI_FLIGHT_TEXTS instead of the value of sy-langu:
define view ZI_FLIGHT_REPORT with parameters p_langu : syst_langu @<Environment.systemField: #LANGUAGE as select from zi_flight_texts(p_langu) { carrid, connid, fldate, carrname, carrtext, count(*) as flight_count } where p_langu = 'E' group by carrid, connid, fldate, carrname, carrtext
What are some characteristics of secondary keys for internal tables? Note: There are 3 correct answers to this question.
Answer : A, B, D
A . Secondary keys must be chosen explicitly when you actually read from an internal table. This means that when you use a READ TABLE or a LOOP AT statement to access an internal table, you have to specify the secondary key that you want to use with the USING KEY addition. For example, the following statement reads an internal table itab using a secondary key sec_key:
READ TABLE itab USING KEY sec_key INTO DATA(wa).
If you do not specify the secondary key, the system will use the primary key by default2.
B . Multiple secondary keys are allowed for any kind of internal table. This means that you can define more than one secondary key for an internal table, regardless of the table type. For example, the following statement defines an internal table itab with two secondary keys sec_key_1 and sec_key_2:
DATA itab TYPE SORTED TABLE OF ty_itab WITH NON-UNIQUE KEY sec_key_1 COMPONENTS field1 field2 sec_key_2 COMPONENTS field3 field4.
You can then choose which secondary key to use when you access the internal table1.
D . Sorted secondary keys do NOT have to be unique. This means that you can define a sorted secondary key for an internal table that allows duplicate values for the key fields. A sorted secondary key maintains a predefined sorting order for the internal table, which is defined by the key fields in the order in which they are specified. For example, the following statement defines a sorted secondary key sec_key for an internal table itab that sorts the table by field1 in ascending order and field2 in descending order:
DATA itab TYPE STANDARD TABLE OF ty_itab WITH NON-UNIQUE SORTED KEY sec_key COMPONENTS field1 ASCENDING field2 DESCENDING.
The following are not characteristics of secondary keys for internal tables, because:
C . Hashed secondary keys do NOT have to be unique. This is false because hashed secondary keys must be unique. This means that you can only define a hashed secondary key for an internal table that does not allow duplicate values for the key fields. A hashed secondary key does not have a predefined sorting order for the internal table, but uses a hash algorithm to store and access the table rows. For example, the following statement defines a hashed secondary key sec_key for an internal table itab that hashes the table by field1 and field2:
DATA itab TYPE STANDARD TABLE OF ty_itab WITH UNIQUE HASHED KEY sec_key COMPONENTS field1 field2.
You can then access the internal table using the hashed secondary key with a direct access algorithm, which is very fast.
Which of the following actions cause an indirect change to a database table requiring a table conversion? Note: There are 2 correct answers to this question.
Answer : A, C
The following are the explanations for each action:
A: Renaming a field in a structure that is included in the table definition causes an indirect change to the database table, as the field name in the table is derived from the structure. This change requires a table conversion, as the existing data in the table must be copied to a new table with the new field name, and the old table must be deleted.
B: Changing the field labels of a data element that is used in the table definition does not cause an indirect change to the database table, as the field labels are only used for documentation and display purposes. This change does not require a table conversion, as the existing data in the table is not affected by the change.
C: Deleting a field from a structure that is included in the table definition causes an indirect change to the database table, as the field is removed from the table as well. This change requires a table conversion, as the existing data in the table must be copied to a new table without the deleted field, and the old table must be deleted.
D: Shortening the length of a domain used in a data element that is used in the table definition causes an indirect change to the database table, as the field length in the table is derived from the domain. This change requires a table conversion, as the existing data in the table must be checked for compatibility with the new field length, and any data that exceeds the new length must be truncated or rejected.
You are given the following information:
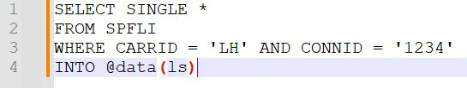
1.
The data source "spfli" on line #2 is an SAP HANA
database table
2.
"spfli" will be a large table with over one million rows.
3.
This program is the only one in the system that accesses
the table.
4.
This program will run rarely.
Based on this information, which of the following general
settings should you set for the spfli database table? Note:
There are 2 correct answers to this question.
Answer : C, D
Based on the given information, the spfli database table should have the following general settings: