Salesforce B2C Commerce Architect Salesforce Certified B2C Commerce Architect Exam Practice Test
Given a website launched to production, the Architect can rely on several SFCC Business Manager tools that provide an automatic notification feature.
Which three tools have such a feature and do not require to be monitored manually?
Choose 3 answers
Answer : A, D, E
The Salesforce B2C Commerce Business Manager tools that feature automatic notifications are:
Option A (Job Schedules): Business Manager can send notifications based on job schedules, alerting users when a scheduled job has completed, failed, or met specific conditions. This feature helps in monitoring automated processes without manual oversight.
Option D (Pipeline Profiler): This tool provides automatic notifications regarding the performance of different pipelines, allowing architects and developers to monitor site performance and troubleshoot issues proactively.
Option E (Quota Status): Automatically notifies administrators when certain quotas are reached or exceeded, such as API call limits or data storage limits, which is crucial for maintaining site stability and performance.
These tools are essential for proactive site management, ensuring that administrators can address potential issues before they affect the site's operation.
The following promotions are configured with no exclusivity (can be combined with any other promotion) in a -1month campaign:
* Free correct- in -store shipping
* 20% accessories products discount, applies for all customers
* $5 off coupon based discount, sent to a selected group of customers
The combination of above promotions allows customers to get 16 socks for free in store. This was unintended, and the Client If considering disabling the coupon. The Client is concerned about a potential spike in the number of Call Center calls from customers who had the coupon code added to their baskets before it was disabled. As basket lifetime is set to 30 days for all customers, this can continue for the full length of the campaign.
What solutionshould the Architect suggest to keep the Call Center calls to a minimum?
Answer : D
Reducing the basket lifetime is a strategic approach to minimizing the impact of disabling a promotional coupon. This action will cause baskets that may still contain the now-disabled coupon to expire sooner, thereby reducing the potential volume of calls to the Call Center from customers inquiring about the coupon. This method also avoids the drastic measure of clearing all existing baskets or restarting the production instance, which could disrupt user experience and lead to further customer dissatisfaction.
A client receives multiple feeds from third parties on the same SFTP location:
* Product prices (sftp: prod/prices)
* Stores information (sftp: prod/stores;
* Product information (sftp: prod/catalog)
* Categories information (sftp: prod/marketing)
* Content (sftp: prod/marketing)
Some of the feeds are placed on sftp multiple times a day, as the information is updated in the source system.
The Architect decides to have only two jobs:
* One that checks and downloads available feeds every hour
* One that imports the files from Webdav once a day before the data replication, using the standards steps available in the Job Framework
Which design is correctfor the import Job, taking the steps scope in consideration?
Answer : B
This design maximizes efficiency and concurrency. By having the jobs that import products, stores, prices, and content run in parallel, the system can handle multiple data streams simultaneously, reducing total processing time. The sequential execution of importing categories followed by reindexing ensures that all new and updated information is properly indexed and available for site use, following the completion of the import of more frequently updated data. This order respects dependencies between steps and aligns with best practices for handling complex data workflows in B2C Commerce environments.
A B2C Commerce developer has recently completed a tax service link cartridge integration into a new SHU site. During review, the Architect notices the basket calculation hook is being run multiple times during a single tax call.
What is the reason for the duplicate calculations being run?
Answer : C
If multiple hook.js files are referring to the same basket calculation hook within a LINK cartridge integration, it could lead to the hook being executed multiple times during a single tax call. This often occurs due to redundancy in the integration, where multiple scripts are set to trigger the same function, inadvertently causing duplicate calculations. It's essential to ensure that only one script is responsible for invoking specific hooks to prevent this kind of redundancy and inefficiency in the system.
During a load test the storefront shows steady but slow performance on all the paces being tested. The Architect opens Pipeline Profiler and sorts the data by *total time" column. The following come as the top Ave items:
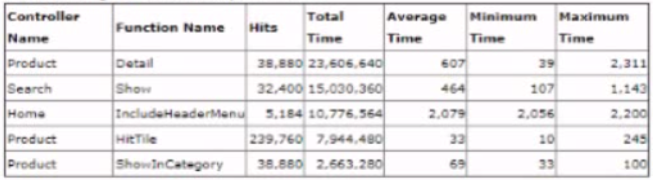
Which controller should the Architect focus on to further investigate the performance issue?
Answer : C
Focusing on the 'Product-Detail' controller is prudent given that it has the highest total time and the highest maximum time (Answer C), suggesting that it significantly contributes to the overall load and potential slowdowns on the site. By analyzing and optimizing this controller, the architect can potentially achieve the most substantial improvement in performance. Efforts might include optimizing database queries, caching frequently requested data, or simplifying complex logic in the Product-Detail page's processing.
An Architect is configuring a data replication schedule.
Which task(s) can be removed In order to reduce replication times?
Answer : B
Reducing the replication times in data synchronization can be effectively achieved by removing or reducing frequency of tasks that are less critical or that do not change frequently. Static content, such as images and static texts that do not change often, can be safely removed from frequent replication schedules (Answer B). This adjustment will reduce the data load and frequency of updates, thereby speeding up the overall replication process. Unlike dynamic content like campaigns, search indexes, or URLs that might change frequently and impact user experience or site functionality if not updated, static content does not typically necessitate immediate replication, making it a suitable candidate for removal to enhance replication efficiency.
The Client has just acquired a new brand and wants toIntegrate the new brand s current ecommerce site into a current realm as a new site. The acquisition has its own Enterprise Resource Planning (ERP) system for product data and inventory. The new site will use the existing realm's Order Management System (OHS) and Customer Relationship Management (CRM) system.
What two requirements does the Architect need to keep in mind when creating the technical specification document?
Choose 2 answers
Answer : B, C
When integrating a new brand's ecommerce site into an existing realm, the architect needs to ensure that product data and inventory from the new brand's Enterprise Resource Planning (ERP) system are correctly managed within the realm. Therefore, creating new import jobs for products (Answer B) and inventory (Answer C) is essential. These import jobs will facilitate the synchronization of the new brand's product catalog and inventory levels with the existing Order Management System (OMS) and Customer Relationship Management (CRM) systems of the realm. Such integration is crucial for maintaining up-to-date product and inventory information across the systems, ensuring seamless operations and data consistency.