Pegasystems PEGACPLSA88V1 Certified Pega Lead System Architecture Exam 8.8 Exam Practice Test
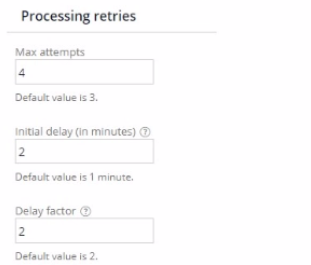
A queue processor is configured with the value of the Max attempts field is 4, the value of the Initial delay field is 2 minutes and the the value of the Delay factor field is 2 for processing retries.
What is the delay between the second and third attempt, assuming each previous attempt fails?
Answer : A, B
Max Attempts: The maximum number of retry attempts set is 4.
Initial Delay: The initial delay before the first retry attempt is 2 minutes.
Delay Factor: The delay factor is set to 2, which means the delay doubles with each retry.
Calculating Delays:
First attempt fails, delay before second attempt = Initial delay = 2 minutes.
Second attempt fails, delay before third attempt = Initial delay * Delay factor = 2 minutes * 2 = 4 minutes.
Third attempt fails, delay before fourth attempt = 4 minutes * Delay factor = 4 minutes * 2 = 8 minutes.
Delay Between Attempts: The question specifically asks for the delay between the second and third attempt, which is calculated as 8 minutes.
Pega documentation on queue processor configuration.
Pega Platform 8.x help files related to processing retries and delay factors.
You oversee a medium-sized development team, and some of the team members are new to using Pega Platform. What are the two most efficient ways to ensure that the rules the team creates adhere to best practices? (Choose Two)
Answer : A, C
Automated Pega Unit Tests:
Having new team members create and run automated Pega unit tests against their rules ensures that they adhere to best practices and catch errors early.
Rule Check-In Approval Process:
Using the rule check-in approval process allows for a review of changes made by new team members, ensuring that all rules meet the required standards and best practices.
Reference:
Pega best practices for rule management and team collaboration recommend these approaches to maintain code quality and adherence to standards.
Therefore, the correct answers are:
A . Have new team members create and run automated Pega unit tests against their rules.
C . Use the rule check-in approval process to review the changes that the new team members make.
Case Type A and Case Type B capture information about multiple line items. Each line item is an Instance erf the same Line Item data type. Separate work pool classes are used for Case Types A and B.
What is the optimal data model design to meet these requirements?
Answer : D
Embedded List with Declare Index:
Both Case Types A and B possess an embedded list of line items. Using a Declare Index against each embedded list ensures efficient data retrieval and indexing.
Changing the direct inheritance class for each Declare Index class to the Line Item data type allows for proper data management and querying.
Reference:
Pega best practices for data modeling and indexing recommend using Declare Index for embedded lists to enhance performance and data organization.
Therefore, the correct answer is:
D . Case Types A and B both possess an embedded list of line items. Define a Declare Index against each embedded list. Change the direct inheritance class for each Declare Index class to the Line Item data type.
A Lead System Architect (LSA) plays a significant role at every level of data modeling by collaborating with other stakeholders.
Which two of the following statements about data model design are true? (Choose Two)
Answer : C, D
Data Analysts and Data Architects:
They perform data collection and design, choose the correct layer for elements, and create a logical group of elements using inheritance or composition.
This aligns with best practices in data model design where specialized roles handle the technical aspects of data modeling.
Subject Matter Experts (SMEs):
SMEs identify data sources, understand the flow of data, and determine the proper data type for data elements.
Their expertise in the business domain ensures that the data model accurately reflects business requirements and processes.
Reference:
Pega Lead System Architect documentation on roles in data modeling emphasizes collaboration between various stakeholders, including Data Analysts, Data Architects, and SMEs.
Therefore, the correct answers are:
C . Data Analysts and Data Architects perform data collection, data design, choose the correct layer for elements, and create a logical group of elements by using inheritance or composition.
D . Subject Matter Experts identify the data source, understand the flow of data, and identify the proper data type for the data elements.
A healthcare company decides to use Pega Foundation for Healthcare (PFH) for all of their new Pega Platform"" applications, because the data model that PFH provides can accommodate all of their needs. However, some new fields and new data classes need to be created to suit the company's specific processes.
What is the recommended approach to extending the foundation data model?
Answer : D
To extend the Pega Foundation for Healthcare (PFH) data model:
Direct Inheritance for Extension (B):
Use direct inheritance to extend the foundation data model provided by PFH. This ensures that the core data model remains intact while allowing for the addition of new fields and data classes specific to the company's needs.
Pattern Inheritance for Behavior (B):
Utilize pattern inheritance to extend application-specific behavior. This allows for customization and the addition of application-specific logic while maintaining a clear separation from the core data model.
Pega Foundation for Healthcare Implementation Guide
Pega Inheritance Models Documentation
An application contains cases that transition through different statuses throughout their life cycle, which typically lasts three months.
Design a reporting strategy to display the number of cases by status at the end of each month for a 12-month period.
Answer : A
Job Scheduler:
Configuring a job scheduler to record monthly case status in a separate table ensures that the data is consistently updated and available for reporting.
Reference:
Pega best practices for reporting strategies recommend using job schedulers to handle periodic data collection and reporting tasks.
Therefore, the correct answer is:
A . Configure a job scheduler to record monthly case status in a separate table and report on that table.
Which two approaches can you take to facilitating Mashup interface development in App Studio? (Choose Two)
Answer : B, C
Setting pxThread.isWebMashup:
In the pyDefault Data Transform for a case, setting pxThread.isWebMashup to True ensures that App Studio users see the same views displayed by a Mashup interface.
Associated Privilege Visibility Conditions:
Using associated privilege visibility conditions allows App Studio users to view and configure sections only shown to external personas at design time.
Reference:
Pega documentation on Mashup interface development in App Studio outlines these practices to ensure seamless integration and development.
Therefore, the correct answers are:
B . In the pyDefault Data Transform for a case, set pxThread.isWebMashup to True by using an Application Setting. App Studio users then see the same views that are displayed by a Mashup interface when it is configured to use the Create a case option.
C . Use associated privilege visibility conditions. At design time, an App Studio user is able to view and configure sections that are only shown to external personas.