Palo Alto Networks SSE-Engineer Palo Alto Networks Security Service Edge Engineer Exam Practice Test
An intern is tasked with changing the Anti-Spyware Profile used for security rules defined in the GlobalProtect folder. All security rules are using the Default Prisma Profile. The intern reports that the options are greyed out and cannot be modified when selecting the Default Prisma Profile.
Based on the image below, which action will allow the intern to make the required modifications?
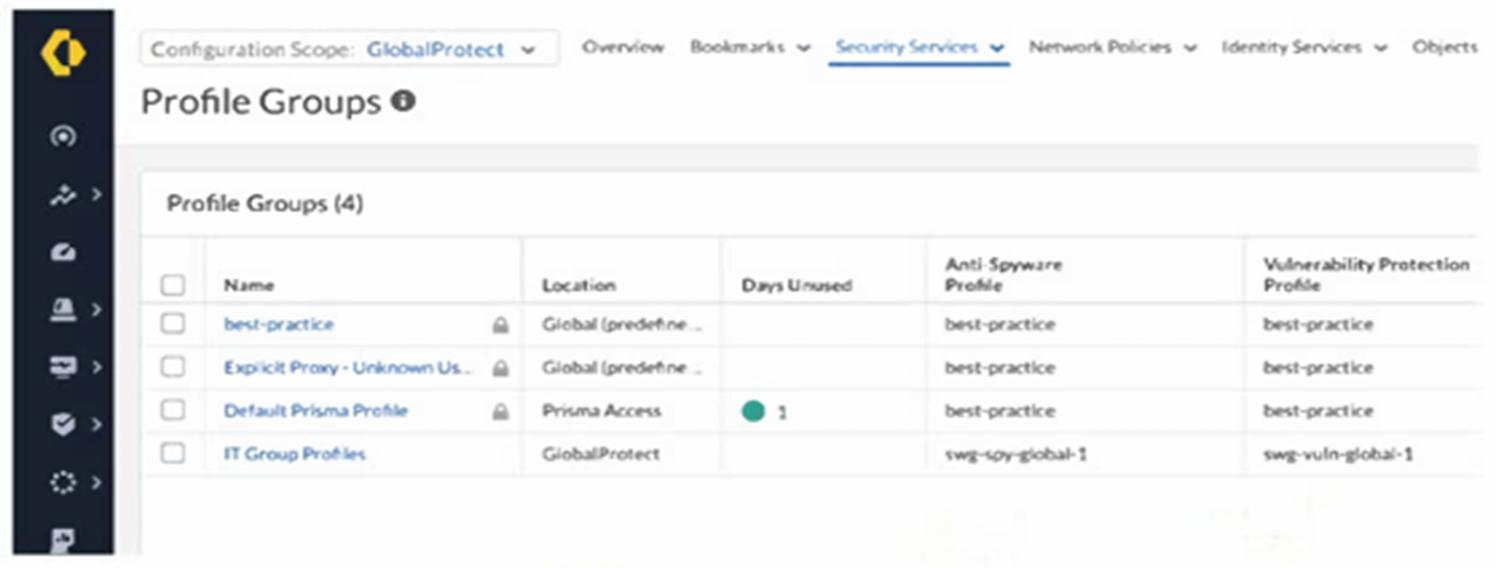
Answer : C
Palo Alto Networks best practices and the behavior of Strata Cloud Manager (SCM) dictate that predefined or default objects, including profile groups like 'Default Prisma Profile,' cannot be directly modified. These default objects serve as baseline configurations and are often locked to prevent accidental or unintended changes that could impact the overall security posture.
The intern's experience of the options being greyed out when selecting 'Default Prisma Profile' is a direct indication of this immutability of default objects.
Therefore, the correct action is to:
Create a new Profile Group: The intern should create a new profile group within the appropriate configuration scope (likely GlobalProtect, given the task).
Configure the new Profile Group: In this new profile group, the intern can select the desired Anti-Spyware Profile (which might be an existing custom profile or a new one they create).
Modify Security Rules: The security rules currently using the 'Default Prisma Profile' in the GlobalProtect folder need to be modified to use this newly created profile group.
Let's analyze why the other options are incorrect based on official documentation:
A . Request edit access for the GlobalProtect scope. While having the correct scope permissions is necessary for making any changes within GlobalProtect, it will not override the inherent immutability of default objects like 'Default Prisma Profile.' Edit access will allow the intern to create new objects and modify rules, but not directly edit the default profile group.
B . Change the configuration scope to Prisma Access and modify the profile group. The image shows that 'Default Prisma Profile' has a 'Location' of 'Prisma Access.' However, even within the Prisma Access scope, default profile groups are generally not directly editable. The issue is not the scope but the fact that it's a default object.
D . Modify the existing anti-spyware profile, because best-practice profiles cannot be removed from a group. The question is about changing the profile group, not the individual Anti-Spyware Profile. While 'best-practice' profiles might be part of default groups, the core issue is the inability to modify the default group itself. Creating a new group allows the intern to choose which Anti-Spyware Profile to include.
In summary, the fundamental principle in Palo Alto Networks management is that default objects are typically read-only to ensure a consistent and predictable baseline. To make changes, you need to create custom objects.
In an Explicit Proxy deployment where no agent can be used on the endpoint, which authentication method is supported with mobile users?
Answer : C
In an Explicit Proxy deployment where no agent can be used on the endpoint, SAML (Security Assertion Markup Language) is the supported authentication method for mobile users. SAML allows authentication via an Identity Provider (IdP) without requiring an agent on the endpoint, making it ideal for web-based authentication in cloud and remote access environments. It enables Single Sign-On (SSO) and secure authentication without direct integration with LDAP or Kerberos, which typically require an agent or local network presence.
Strata Logging Service is configured to forward logs to an external syslog server; however, a month later, there is a disruption on the syslog server.
Which action will send the missing logs to the external syslog server?
Answer : A
The Strata Logging Service allows log replay, which enables resending logs that were not successfully forwarded to an external syslog server due to disruptions. By configuring a replay profile with the affected time range and associating it with the syslog server profile, Prisma Access will resend the missing logs, ensuring that all relevant data is restored in the external logging system. This approach is the most efficient and automated way to recover missing logs.
In addition to creating a Security policy, how can an AI Access Security be used to prevent users from uploading financial information to ChatGPT?
Answer : B
Palo Alto Networks AI Access Security integrates with Enterprise Data Loss Prevention (DLP) capabilities to control sensitive data within AI applications like ChatGPT. The most effective way to prevent users from uploading financial information is to:
Define an Enterprise DLP rule: This rule would be configured to identify content that matches patterns or keywords associated with financial information (e.g., credit card numbers, bank account details, tax identifiers, financial statements).
Apply the DLP rule to the AI Access Security policy: This policy would be specifically configured to inspect traffic to and from ChatGPT. When the DLP rule detects a user attempting to upload content containing financial information, it can take a defined action, such as blocking the upload.
Let's analyze why the other options are incorrect based on official documentation:
A . Apply File Blocking to stop file uploads containing financial information. While File Blocking can prevent the upload of certain file types, it is not content-aware. It cannot inspect the content of a file to determine if it contains financial information. Therefore, it's not a granular or effective solution for this specific requirement.
C . Add the ChatGPT domains using URL Filtering to block uploads containing financial information. URL Filtering controls access to specific websites or categories of websites. While you could potentially block access to ChatGPT entirely, it does not provide the capability to inspect the content being uploaded to a permitted domain and prevent the transfer of sensitive financial data.
D . Apply a vulnerability profile to stop attempts to exploit system flaws or gain unauthorized access to financial systems. Vulnerability profiles are designed to detect and prevent attempts to exploit known security vulnerabilities in systems. They are not designed to inspect the content of user uploads for sensitive data like financial information. While important for overall security, they do not directly address the requirement of preventing financial data uploads to ChatGPT.
Therefore, configuring an Enterprise DLP rule within AI Access Security is the correct and most effective method to prevent users from uploading financial information to ChatGPT by inspecting the content of the uploads.
How can a senior engineer use Strata Cloud Manager (SCM) to ensure that junior engineers are able to create compliant policies while preventing the creation of policies that may result in security gaps?
Answer : A
By using security checks under posture settings in Strata Cloud Manager (SCM), the senior engineer can enforce policy compliance standards by automatically denying any security policy that does not align with best practices. This ensures that junior engineers can create policies while preventing configurations that might introduce security gaps. This proactive approach eliminates manual oversight and enforces compliance at the time of policy creation, reducing risk and ensuring consistent security enforcement.
What is the flow impact of updating the Cloud Services plugin on existing traffic flows in Prisma Access?
Answer : C
Updating the Cloud Services plugin in Prisma Access does not disrupt existing traffic flows because the upgrade process is designed to be seamless and transparent. Prisma Access ensures high availability by maintaining active sessions and policies while applying the update in the background. This allows ongoing connections to continue without interruptions, minimizing impact on user experience.
A company has four branch offices between Canada Central and Canada East which use the same IPSec termination node and have QoS configured with customized bandwidth per site. An engineer wants to onboard a new branch office on the same IPSec termination node.
What is the QoS behavior for the new branch office?
Answer : B
When onboarding a new branch office to an existing IPSec termination node in Prisma Access, the QoS bandwidth is not automatically assigned. Instead, the newly added branch remains unallocated until the administrator manually assigns bandwidth within the QoS configuration settings. This ensures that customized bandwidth per site remains intact and allows for fine-tuned traffic management based on business needs.