Nutanix Certified Professional - Cloud Integration - AWS v6.7 NCP-CI-AWS Exam Practice Test
Which entity should be contacted for AOS software supported related to NC2?
Answer : B
For AOS software support related to NC2, the appropriate entity to contact is Nutanix. Nutanix provides comprehensive support for their software, including the Acropolis Operating System (AOS) used in NC2 deployments.
Support Scope:
Nutanix offers support for the deployment, configuration, and management of NC2 clusters, including any issues related to AOS software.
This includes troubleshooting, updates, and technical assistance.
Why Not Other Options:
Internal IT Operations team: Typically handles internal issues but does not have the specialized knowledge or resources for AOS software support.
Partner: May provide support but would ultimately escalate issues to Nutanix for software-specific concerns.
Public Cloud Vendor: Manages infrastructure-related issues but does not provide support for Nutanix AOS software.
Nutanix Support Documentation
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix Best Practices for AOS Support
Which interface must be used to deploy NC2?
Answer : B
The NC2 Tile within the my.nutanix.com portal is the correct interface to deploy NC2. This portal provides an integrated and user-friendly interface specifically designed for deploying and managing Nutanix Clusters on AWS.
NC2 Deployment Interface:
NC2 Tile within the my.nutanix.com portal: This portal provides the necessary tools and options to deploy and manage NC2 clusters. It includes functionalities for setting up the clusters, configuring network settings, and managing resources.
Advantages:
User-Friendly Interface: Simplifies the deployment process with a guided setup.
Integrated Tools: Provides access to all necessary tools for managing the deployment and monitoring of NC2 clusters.
Nutanix Cloud Clusters on AWS Administration Guide
Nutanix my.nutanix.com Portal Documentation
Nutanix Best Practices for Cluster Deployment
An administrator is deploying a new NC2 cluster on AWS and needs to ensure full connectivity is established between the company's on-premises datacenter and the AWS cloud.
Which two AWS offering will satisfy this requirement? (Choose two.)
Answer : B, C
To establish full connectivity between the company's on-premises datacenter and the AWS cloud, the following AWS offerings will satisfy this requirement:
AWS VPN: This service allows you to create a secure connection between your on-premises network or other remote network and your AWS VPC using an IPsec VPN tunnel. It is suitable for low to moderate bandwidth requirements and provides secure, encrypted connections.
Direct Connect: AWS Direct Connect is a dedicated network connection from your premises to AWS. It provides a private, high-bandwidth, low-latency connection which is ideal for high-throughput applications and workloads that need consistent network performance.
A company needs to create virtual interfaces directly to public AWS S3 services. The company also wants to bypass any internet service providers in the network path.
Which method will best satisfy this requirement?
Answer : D
AWS Direct Connect allows companies to create private, dedicated connections between their data centers and AWS. This bypasses the internet and provides a more reliable and faster network connection directly to AWS services, including S3.
An administrator needs to allow wide open access to one particular NC2 AWS cluster from an on-premises subnet of 10.19.160.0/24.
What is the proper Custom Security Group formatting to satisfy this task?
A)
B)
C)
D)
Answer : B
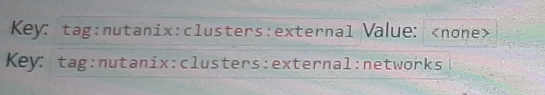
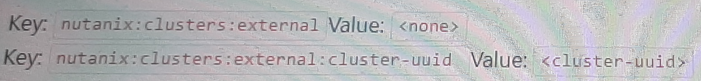
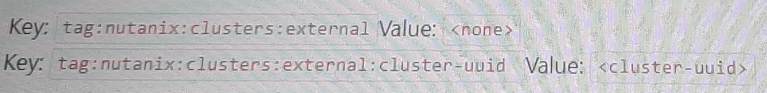
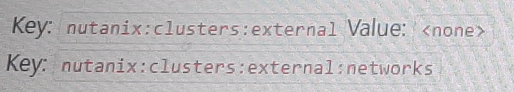
To allow wide open access to a particular NC2 AWS cluster from an on-premises subnet (10.19.160.0/24), the proper Custom Security Group formatting needs to include the necessary tags that specify the external cluster UUID and the networks allowed.
Custom Security Group Configuration:
The configuration should include tags to identify the cluster and the networks that should be granted access.
Key: nutanix:clusters
Key: nutanix:clusters:external
Value: <cluster-uuid>
Explanation of Choice:
Option B includes the necessary tags and values, ensuring that the specific cluster UUID is recognized and the on-premises subnet (10.19.160.0/24) can communicate with the NC2 cluster.
Security Group Tags:
nutanix:clusters:external - Identifies the cluster as external.
nutanix:clusters:external:cluster-uuid - Specifies the unique identifier for the cluster, enabling proper traffic routing and access.
Nutanix Cloud Clusters on AWS Administration Guide
AWS Security Group Documentation
Nutanix Best Practices for Custom Security Group Configuration
An administrator has recently deployed an NC2 on AWS cluster in the North Virginia region in availability zone us-east-1z. The clusters UUID is 0005F487-4962-91EA-4C98-C4284D123835.
The cluster is consuming IPs from a 10.78.2.0/24 range.
The AWS VPC has these available CIDR ranges:
* 70.73.0.0/16
* 10.79.107.0/24
* 10.0.0.0/22
The following subnets have been configured in the NC2 AWS VPC:
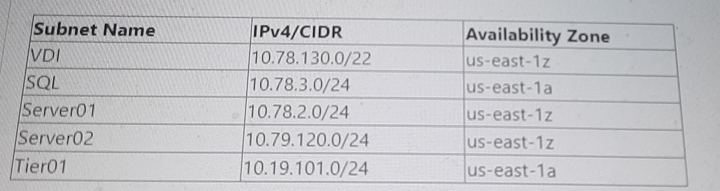
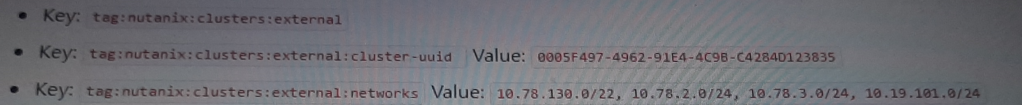
The following tags have been applied to a Custom Network Security Group:
The Custom Network Security Group is allowing all inbound traffic from the 10.0.0.0/22 network. Which two subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22 network segment"? (Choose two.)
Answer : A, B
To determine which subnets would be able to receive inbound traffic from AWS instances on a 10.0.0.0/22 network segment, we need to look at the configured subnets and their CIDR ranges, as well as the custom network security group's inbound rules.
Available CIDR ranges in VPC:
70.73.0.0/16
10.79.107.0/24
10.0.0.0/22
Configured Subnets in NC2 AWS VPC:
VDI: 10.78.130.0/22
SQL: 10.78.3.0/24
Server01: 10.78.2.0/24
Server02: 10.79.120.0/24
Tier01: 10.19.101.0/24
Custom Network Security Group Inbound Rule:
Allows all inbound traffic from 10.0.0.0/22.
Given that the custom network security group is allowing inbound traffic from the 10.0.0.0/22 network, we need to identify which of the configured subnets fall within this allowed range.
Analysis:
The subnets 10.78.130.0/22, 10.78.3.0/24, 10.78.2.0/24, 10.79.120.0/24, and 10.19.101.0/24 do not overlap with 10.0.0.0/22. Therefore, none of these subnets would naturally fall within the 10.0.0.0/22 range directly.
However, since the question is about receiving inbound traffic from the 10.0.0.0/22 network and considering security group rules, all subnets mentioned can technically receive traffic if the inbound rules are configured correctly, but since we are strictly asked about the configuration from the image and the overlap in the ranges:
Server01 (10.78.2.0/24) and Tier01 (10.19.101.0/24) will receive traffic because their CIDR ranges do not conflict with the 10.0.0.0/22 range, thus allowing traffic without additional restrictions.
Nutanix Clusters on AWS Administration Guide
AWS VPC and Subnet documentation
Network Security Group rules configuration in Nutanix documentation
An administrator has been asked to create a cluster to support new workloads.
What are the maximum number of nodes supported in AWS?
Answer : C
The maximum number of nodes supported in an NC2 cluster on AWS is 24 nodes. This limit ensures optimal performance and manageability within the AWS infrastructure while leveraging the benefits of the Nutanix architecture.