Netskope Certified Cloud Security Architect NSK300 Exam Practice Test
Review the exhibit.
You work for a medical insurance provider. You have Netskope Next Gen Secure Web Gateway deployed to all managed user devices with limited block policies. Your manager asks that you begin blocking Cloud Storage applications that are not HIPAA compliant Prior to implementing this policy, you want to verity that no business or departmental applications would be blocked by this policy.
Referring to the exhibit, which query would you use in the Edit Widget window to narrow down the results?
You want to verify that Google Drive is being tunneled to Netskope by looking in the nsdebuglog file. You are using Chrome and the Netskope Client to steer traffic. In this scenario, what would you expect to see in the log file?
A)
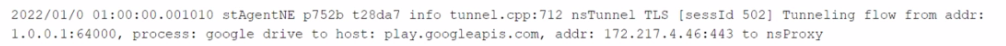
B)
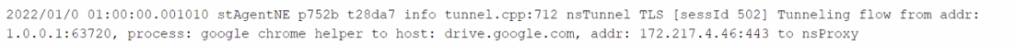
C)

D)

You want customers to configure Real-time Protection policies. In which order should the policies be placed in this scenario?
Answer : B
When configuring Real-time Protection policies in Netskope, the recommended order is as follows:
RBI (Risk-Based Index) Policies: These policies focus on risk assessment and prioritize actions based on risk scores. They help identify high-risk activities and users.
CASB (Cloud Access Security Broker) Policies: These policies address cloud-specific security requirements, such as controlling access to cloud applications, enforcing data loss prevention (DLP) rules, and managing shadow IT.
Web Policies: These policies deal with web traffic, including URL filtering, web categories, and threat prevention.
Threat Policies: These policies focus on detecting and preventing threats, such as malware, phishing, and malicious URLs.
Placing the policies in this order ensures that risk assessment and cloud-specific controls are applied before addressing web and threat-related issues.Reference:
Netskope Security Cloud Introductory Online Technical Training
Netskope Security Cloud Operation & Administration (NSCO&A) - Classroom Training
Netskope Certification Description
Netskope Architectural Advantage Features
You are asked to create a customized restricted administrator role in your Netskope tenant for a newly hired employee. Which two statements are correct in this scenario? (Choose two.)
Answer : A, C
Admin Role and File Content Viewing: By default, an admin role doesnotprevent admins from downloading and viewing file content. Admins have access to view and download file content unless specific restrictions are applied.
Role Privileges Default to Read Only: All role privileges in Netskope default toRead Onlyfor all functional areas. This means that admins can view information but cannot make changes unless explicitly granted additional permissions.
Obfuscation: Obfuscation can be applied to specific functional areas, but it is not a default behavior for all areas.Reference:
Netskope Security Cloud Introductory Online Technical Training
Netskope Security Cloud Operation & Administration (NSCO&A) - Classroom Training
You have multiple networking clients running on an endpoint and client connectivity is a concern. You are configuring co-existence with a VPN solution in this scenario, what is recommended to prevent potential routing issues?
Answer : B
To prevent potential routing issues and ensure that the Netskope agent consistently sees the traffic first, it is recommended tomodify the VPN to operate in full tunnel mode at Layer 3.
In full tunnel mode, all traffic from the endpoint is routed through the VPN, including traffic destined for Netskope. This ensures that the Netskope agent can inspect and apply policies to all traffic, regardless of the destination.
Layer 3 full tunnel mode provides better visibility and control over the traffic flow, reducing the risk of routing conflicts or bypassing the Netskope inspection.Reference:
The answer is based on general knowledge of VPN configurations and their impact on traffic routing.
Review the exhibit.
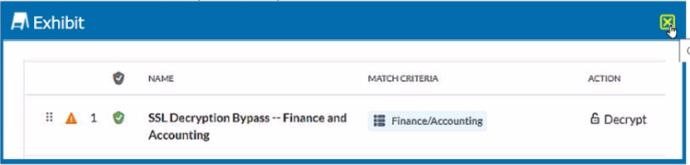
You created an SSL decryption policy to bypass the inspection of financial and accounting Web categories. However, you still see banking websites being inspected.
Referring to the exhibit, what are two possible causes of this behavior? (Choose two.)
Answer : B, D
The issue described in the exhibit is that banking websites are still being inspected despite creating an SSL decryption policy to bypass the inspection of financial and accounting web categories.
Possible Causes:
An incorrect category has been selected (Option B):
If the SSL decryption policy is configured to bypass the wrong category (e.g., not the actual financial and accounting category), it won't effectively exclude banking websites from inspection.
An incorrect action has been specified (Option D):
If the action specified in the policy is not set to ''Bypass,'' it won't achieve the desired behavior. The policy should explicitly bypass SSL inspection for the selected category.
Solution:
Verify that the correct category (financial and accounting) is selected in the policy, and ensure that the action is set to ''Bypass.''
You need to extract events and alerts from the Netskope Security Cloud platform and push it to a SIEM solution. What are two supported methods to accomplish this task? (Choose two.)
Answer : B, D
To extract events and alerts from the Netskope Security Cloud platform and integrate them with a SIEM (Security Information and Event Management) solution, you can utilize the following supported methods:
Cloud Log Shipper (CLS):
The Cloud Log Shipper is designed to forward Netskope logs to external systems, including SIEMs.
It allows you to export logs in real-time or batch mode to a destination of your choice.
By configuring CLS, you can ensure that Netskope events and alerts are sent to your SIEM for further analysis and correlation.
REST API:
The Netskope Security Cloud provides a comprehensive REST API that allows you to programmatically retrieve data, including events and alerts.
You can use the REST API to query specific logs, incidents, or other relevant information from Netskope.
By integrating with the REST API, you can extract data and push it to your SIEM solution.
Netskope Cloud Security
Netskope Resources
Netskope Documentation
These methods ensure seamless data flow between Netskope and your SIEM, enabling effective security monitoring and incident response.