Netskope Certified Cloud Security Integrator NSK200 NCCSI Exam Practice Test
You want to provision users and groups to a Netskope tenant. You have Microsoft Active Directory servers hosted in two different forests. Which statement is true about this scenario?
Review the exhibit.
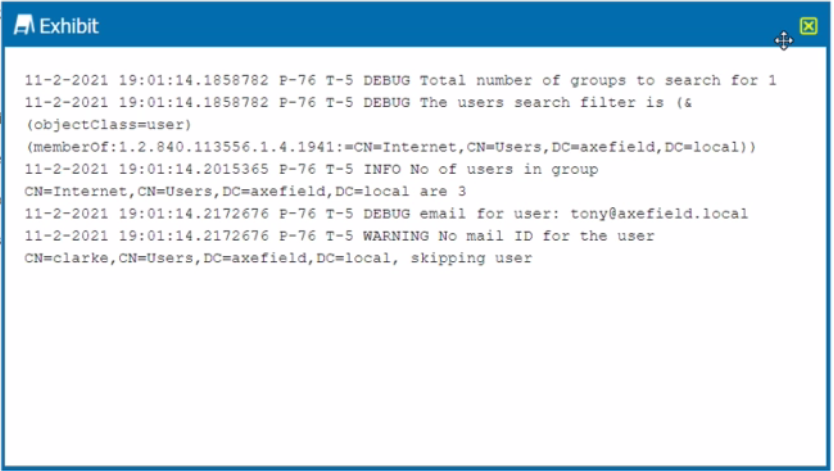
You are troubleshooting a Netskope client for user Clarke which remains in a disabled state after being installed. After looking at various logs, you notice something which might explain the problem. The exhibit is an excerpt from the nsADImporterLog.log.
Referring to the exhibit, what is the problem?
Answer : B
The problem is B. The Active Directory user is not synchronized to the Netskope tenant. This is evident from the log message ''WARNING No mail ID for the user: Clarke, Daxmeifield, DC=local, skipping use''. This means that the user Clarke does not have a valid email address in the Active Directory, which is required for the Netskope client to work. The Netskope client uses the email address of the user to authenticate and enable the client. Therefore, option B is correct and the other options are incorrect.
Review the exhibit.
add log-upload syslogng parserconfig set log-upload syslogng parserconfig 0
logsource
You are asked to deploy a virtual appliance OPLP to accept syslog messages directly from the enterprise Palo Alto Networks firewall. You believe that you have configured the OPLP to accept the firewall logs, yet they are not appearing in Risk Insights. Referring to the exhibit, which parser name would be required to complete the new configuration?
Answer : A
The correct parser name to process syslog messages from Palo Alto Networks firewalls is 'panw-syslog.' Using the appropriate parser ensures that the logs are correctly interpreted and ingested by Netskope, making them available in Risk Insights.
Your customer currently only allows users to access the corporate instance of OneDrive using SSO with the Netskope client. The users are not permitted to take their laptops when vacationing, but sometimes they must have access to documents on OneDrive when there is an urgent request. The customer wants to allow employees to remotely access OneDrive from unmanaged devices while enforcing DLP controls to prohibit downloading sensitive files to unmanaged devices.
Which steering method would satisfy the requirements for this scenario?
Answer : A
A reverse proxy integrated with their SSO would satisfy the requirements for this scenario. A reverse proxy intercepts requests from users to cloud apps and applies policies based on user identity, device posture, app, and data context. It can enforce DLP controls to prohibit downloading sensitive files to unmanaged devices. It can also integrate with the customer's SSO provider to authenticate users and allow access only to the corporate instance of OneDrive. The other steering methods are not suitable for this scenario because they either require the Netskope client or do not provide granular control over cloud app activities.
You use Netskope to provide a default Malware Scan profile for use with your malware policies. Also, you want to create a custom malware detection profile.
In this scenario, what are two additional requirements to complete this task? (Choose two.)
Answer : B, D
To create a custom malware detection profile, adding a quarantine profile ensures that detected threats are appropriately isolated. Additionally, a custom hash list as a blocklist allows you to block specific known malware hashes, further enhancing the customization of the malware detection profile.
The risk team at your company has determined that traffic from the sales team to a custom Web application should not be inspected by Netskope. All other traffic to the Web application should continue to be inspected. In this scenario, how would you accomplish this task?