NetApp NS0-516 NetApp Certified Implementation Engineer - SAN Specialist, E-Series Exam Practice Test
You are setting up asynchronous mirroring between two E2860 systems.
In this scenario, which two prerequisites are required to complete the setup? (Choose two.)
Answer : B, C
Licensing Requirements: Both the primary and secondary systems must have the same premium features licensed to ensure compatibility and functionality for asynchronous mirroring.
System Discovery: Both systems need to be discovered by an Enterprise Management Window (EMW) or SANtricity Unified Manager to facilitate the setup and management of asynchronous mirroring.
Importance of Matching Features: Ensuring that both systems have the same features licensed avoids issues with mirroring operations that depend on specific functionalities being available on both ends.
Management Tools: Using EMW or SANtricity Unified Manager helps in configuring, monitoring, and managing the mirroring process effectively.
NetApp E-Series SANtricity System Manager documentation on mirroring setup
NetApp Implementation Engineer - SAN Specialist - E-Series manuals
A customer wants to manage an E-Series system over a secure connection between the system and a server. During implementation, you are asked to fulfill this installation requirement.
In this scenario, which three actions are required to complete this task? (Choose three.)
Answer : A, C, E
Secure Connection Requirement: To manage the E-Series system over a secure connection, certain steps need to be taken to ensure encrypted communications.
Disabling Legacy Management Interface: This step ensures that only secure management interfaces are used, preventing the use of less secure legacy protocols.
Certificate Signing Request (CSR): Completing the CSR on the system is necessary to generate a public/private key pair. This CSR can then be submitted to a certificate authority (CA) to obtain a signed certificate.
Importing CA Signed Certificates: Once the CA has signed the certificate, it must be imported into the E-Series system. This signed certificate ensures that the communication between the server and the system is encrypted and trusted.
NetApp E-Series SANtricity System Manager documentation on secure management
NetApp Implementation Engineer - SAN Specialist - E-Series manuals
A company has a duplex E-Series system that is operating in a highly tuned environment. Load distribution between the controllers has been manually set up to achieve a specific distribution based on unique workload characteristics.
In this scenario, to maintain this load distribution over time, which E-Series feature should be disabled?
Answer : D
Understanding Load Distribution: In a duplex E-Series system, load distribution between controllers can be manually set up to optimize performance based on specific workload characteristics.
Automatic Load Balancing: This feature automatically redistributes workloads between controllers to balance the load. However, in a highly tuned environment with manually configured load distribution, this automatic feature can disrupt the optimized settings.
Disabling Automatic Load Balancing: To maintain the manual load distribution over time, the Automatic Load Balancing feature should be disabled. This ensures that the workload remains distributed according to the specific manual configuration without interference from automatic adjustments.
NetApp E-Series SANtricity System Manager documentation
NetApp Implementation Engineer - SAN Specialist - E-Series manuals
A company is using the Federal Information Processing Standard (FIPS) on all volume groups. However, one volume group failed a security audit.
In this scenario what would cause a volume group to fail the security audit?
Answer : A
FIPS Compliance: The Federal Information Processing Standard (FIPS) requires all components within a system to adhere to specific security standards.
FDE Drives: Full Disk Encryption (FDE) drives are used to ensure data security.
Audit Failure: Adding an FDE drive as a spare to a volume group without proper encryption settings could cause a security audit to fail.
Solution: Ensure all spare drives in a volume group meet the FIPS encryption requirements.
You help a customer diagnose a performance issue on an E-Series storage system. You decide to measure the amount of data that is being handled over the span of an hour.
In this scenario, what are you measuring?
Answer : C
Definition of Throughput: Throughput refers to the amount of data transferred from or to the storage system over a specific period. It is measured in units such as MB/s or GB/s.
Relevance to Performance Diagnosis: When diagnosing performance issues on an E-Series storage system, measuring throughput over an hour helps determine the data handling capacity of the system. This metric can reveal whether the system is processing data efficiently or if there are bottlenecks.
Methodology: Tools within the SANtricity System Manager can be used to monitor and log throughput, providing insights into the performance characteristics and potential areas needing optimization.
NetApp E-Series SANtricity System Manager documentation on performance monitoring
NetApp Implementation Engineer - SAN Specialist - E-Series manuals
An administrator is asked to create a Dynamic Disk Pools (DDP) pool from eleven 12 TB disks with the requirement that there is adequate space available for a reconstruction if a drive in the pool fails.
In this scenario, what should the administrator do to satisfy this requirement?
Answer : C
Create the Disk Pool:
Step: Use the SANtricity System Manager to create a DDP with the eleven 12 TB disks.
Reason: The DDP automatically reserves space for reconstruction purposes.
Automatic Space Reservation:
Functionality: The system automatically reserves adequate space for reconstruction when a disk fails.
Confirmation:
Verify: Check the pool's configuration to ensure the space is reserved for reconstruction.
Result: The system will show the reserved space within the DDP configuration.
NetApp SANtricity System Manager User Guide
NetApp E-Series DDP configuration and best practices
Click the Exhibit button.
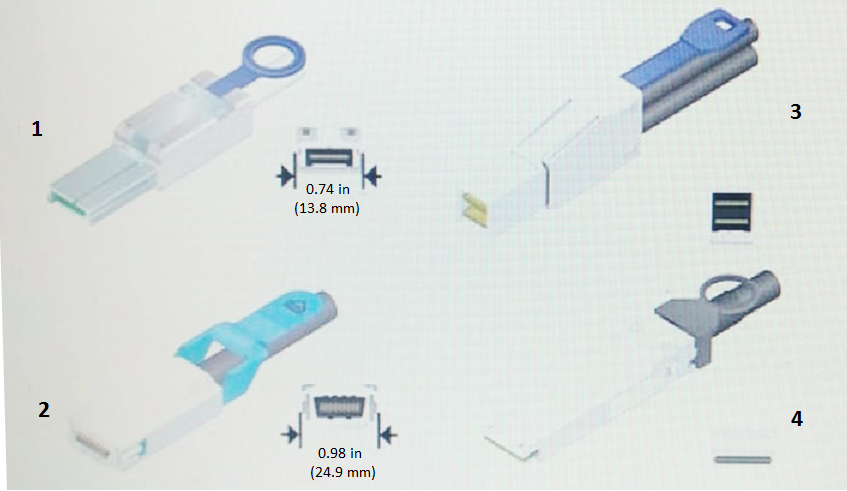
Referring to the exhibit, which cable is an InfiniBand 4X connector?
Answer : B
Identify Connector Types:
Step: Examine the connectors in the exhibit to identify the InfiniBand 4X connector.
Reason: InfiniBand 4X connectors have a distinct appearance and size.
Connector Characteristics:
Observation: Connector 1 in the exhibit is labeled as 0.74 in (13.8 mm), which matches the size and appearance of an InfiniBand 4X connector.
Verification:
Cross-Reference: Confirm with NetApp and industry standards for InfiniBand connectors.
Result: Connector 1 is the InfiniBand 4X connector based on size and design.
NetApp E-Series hardware documentation
Industry standards for InfiniBand connectors