NetApp NS0-403 NetApp Certified Hybrid Cloud Implementation Engineer Exam Practice Test
You have a hybrid storage environment with on-premises ONTAP 9.8 clusters and Cloud Volumes ONTAP for AWS 9.8 clusters. You require anomaly detection to automatically analyze data access patterns to identify risks from ransomware attacks.
In this scenario, which NetApp service satisfies this requirement?
Answer : A
Click the Exhibit button.
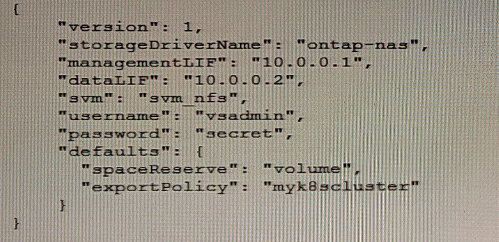
Referring to the exhibit, you are certain that the backend configuration information is correct, but you still cannot get the created PVCs to connect.
What are three reasons for this problem? (Choose three.)
Answer : A, D, E
You are using REST APIs to deploy and manage storage that is provided by NetApp Cloud Volumes ONTAP in Microsoft Azure. You have written a Python script that contains a POST request to the following URL: http://localhost/occm/api/azure/vsa/working-environments. However, you receive a 401 response failure message that indicates that the user is not authenticated.
In this scenario, which two steps must you perform to communicate with an endpoint? (Choose two.)
Answer : C
A team Is Implementing automated builds of Dev/Test environments. The team must ensure consistent and repeatable environments.
In this scenario, which two actions will satisfy this requirement? (Choose two.)
Answer : A, C
You are working with your development team to automate the deployment of Cloud Volumes ONTAP instances across various hyperscalers. The developers are asking you for specific RESTful API calls and other details to facilitate the automation.
In this scenario, which two links would you provide to them? (Choose two.)
Answer : B, C
You are using REST APIs to deploy and manage storage that is provided by NetApp Cloud Volumes ONTAP in Microsoft Azure. You are a federated user, and you want to communicate with an authenticated endpoint.
In this scenario, how should you acquire the JWT access token?
Answer : A
Using Astra Control, which three steps must be completed to protect your Kubernetes-based applications? (Choose three.)
Answer : A, D, E