Microsoft SC-300 Microsoft Identity and Access Administrator Exam Practice Test
You have an Azure Active Directory (Azure AD) tenant that contains a user named User1.
You need to ensure that User1 can create new catalogs and add resources to the catalogs they own.
What should you do?
Answer : B
You use Azure Monitor to analyze Azure Active Directory (Azure AD) activity logs.
Yon receive more than 100 email alerts each day for tailed Azure Al) user sign-in attempts.
You need to ensure that a new security administrator receives the alerts instead of you.
Solution: From Azure monitor, you modify the action group.
Does this meet the goal?
Answer : B
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains an Azure AD
enterprise application named App1.
A contractor uses the credentials of user1@outlook.com.
You need to ensure that you can provide the contractor with access to App1. The contractor must be able to
authenticate as user1@outlook.com.
What should you do?
Answer : D
https://docs.microsoft.com/en-us/azure/active-directory/external-identities/b2b-quickstart-add-guest-usersportal
You have a Microsoft Exchange organization that uses an SMTP' address space of contoso.com.
Several users use their contoso.com email address for self-service sign up to Azure Active Directory (Azure AD).
You gain global administrator privileges to the Azure AD tenant that contains the self-signed users.
You need to prevent the users from creating user accounts in the contoso.com Azure AD tenant for self-service sign-up to Microsoft 365 services.
Which PowerShell cmdlet should you run?
Answer : C
https://docs.microsoft.com/en-us/azure/active-directory/enterprise-users/directory-self-service-signup
You have a Microsoft 365 tenant.
You have an Active Directory domain that syncs to the Azure Active Directory {Azure AD) tenant.
Users connect to the internet by using a hardware firewall at your company. The users authenticate to the firewall by using their Active Directory credentials.
You plan to manage access to external applications by using Azure AD.
You need to use the firewall logs to create a list of unmanaged external applications and the users who access them.
What should you use to gather the information?
Answer : A
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have an Azure Active Directory (Azure AD) tenant that syncs to an Active Directory forest.
You discover that when a user account is disabled in Active Directory, the disabled user can still authenticate to Azure AD for up to 30 minutes.
You need to ensure that when a user account is disabled in Active Directory, the user account is immediately prevented from authenticating to Azure AD.
Solution: You configure conditional access policies.
Does this meet the goal?
Answer : B
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/choose-ad-authn
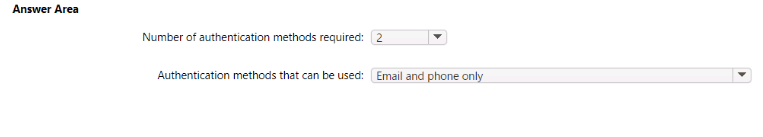
SIMULATION
You implement the planned changes for SSPR.
What occurs when User3 attempts to use SSPR? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Answer : A
Answer is