Microsoft SC-200 Microsoft Security Operations Analyst Exam Practice Test
You have a Microsoft 365 E5 subscription.
You have 1,000 Windows devices that have a third-party antivirus product installed and Microsoft Defender Antivirus in passive mode.
All Windows devices are on boarded to Microsoft Defender for Endpoint.
You need to ensure that the devices are protected from malicious artifacts that were undetected by the third-party antivirus product.
Solution: You enable Live Response.
Does this meet the goal?
Answer : A
You have a Microsoft 365 B5 subscription that contains two groups named Group! and Group2 and uses Microsoft Copilot for Security. You need to configure Copilot for Security role assignments to meet the following requirements:
* Ensure that members of Group1 can run prompts and respond to Microsoft Defender XDR security incidents.
* Ensure that members of Group2 can run prompts.
* Follow the principle of least privilege.
You remove Everyone from the Copilot Contributor role.
Which two actions should you perform next? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
Answer : A, B
You have a Microsoft 365 E5 subscription that uses Microsoft Copilot for Security. You plan to run the following code to create a custom Copilot for Security plugin.
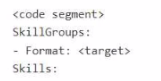
You need to specify a format and complete the code segment. Which format should you use for the
Answer : A
You have a Microsoft 365 B5 subscription that uses Microsoft Defender XDR. You are investigating an incident
You need to review the incident tasks that were performed. What can you use on the Incident page?
Answer : D
You have a Microsoft 365 B5 subscription that contains a user named User1. The subscription uses Microsoft 365 Copilot for Security. Copilot for Security uses the Sentinel plugin. User1 is assigned the Copilot Contributor role.
During an investigation, User1 submits a prompt and receives a notification that Copilot for Security cannot respond to requests because the security compute unit (SCU) usage is nearing the provisioned capacity limit.
You need to ensure that User1 can use Copilot for Security to generate a successful response.
What should User1 do?
Answer : D
You have a Microsoft 365 subscription that uses Microsoft Defender XDR.
You are investigating an attacker that is known to use the Microsoft Graph API as an attack vector. The attacker performs the tactics shown the following table.
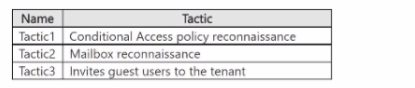
You need to search for malicious activities in your organization.
Which tactics can you analyze by using the MicrosoftGraphActivityLogs table?
Answer : B
You have 500 on-premises Windows 11 devices that use Microsoft Defender for Endpoint
You enable Network device discovery.
You need to create a hunting query that will identify discovered network devices and return the identity of the onboarded device that discovered each network device.
Which built-in function should you use?
Answer : B