Microsoft MS-500 Microsoft 365 Security Administration Exam Practice Test
You have a Microsoft 365 E5 subscription that contains a user named User1.
User1 needs to be able to create Data Subject Requests (DSRs) in the Microsoft 365 compliance center.
To which role or role group should you add User1?
Answer : C
You have a Microsoft 365 E5 subscription.
You create a sensitivity label named Label 1 and publish Label1 to all users and groups.
You have the following files on a computer:
* File1.doc
* File2.docx
* File3.xlsx
* File4.txt
You need to identify which files can have Label1 applied. Which files should you identify?
Answer : C
You have a Microsoft 365 tenant that has modern authentication enabled.
You have Windows 10, MacOS. Android, and iOS devices that are managed by using Microsoft Endpoint Manager. Some users have older email client applications that use Basic authentication to connect to Microsoft Exchange Online. You need to implement a solution to meet the following security requirements-
* Allow users to connect to Exchange Online only by using email client applications that support modern authentication protocols based on OAuth 2.0.
* Block connections to Exchange Online by any email client applications that do NOT support modern authentication.
What should you implement?
Answer : C
You have a Microsoft 365 E5 subscription that uses Azure Active Directory (Azure AD) Privileged identity Management (PIM). A user named User! is eligible for the User Account Administrator role. You need User! to request to activate the User Account Administrator role. From where should User1 request to activate the role?
Answer : B
You have a Microsoft 365 E5 subscription that uses insider risk management and contains the users shown in the following table.
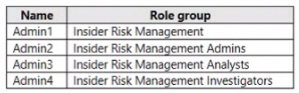
Which users can use Content explorer?
Answer : D
You create an Azure Sentinel workspace.
You configure Azure Sentinel to ingest data from Azure Active Directory (Azure AD).
In the Azure Active Directory admin center, you discover Azure AD Identity Protection alerts. The Azure Sentinel workspace shows the status as shown in the following exhibit.
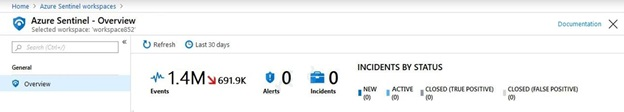
In Azure Log Analytics, you can see Azure AD data in the Azure Sentinel workspace.
What should you configure in Azure Sentinel to ensure that incidents are created for detected threats?
You have an Azure Active Directory (Azure AD) tenant that contains the users shown in the following table.
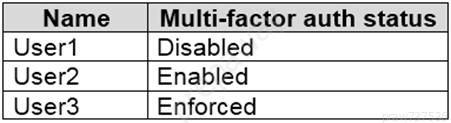
You configure the Security Operator role in Azure AD Privileged Identity Management (PIM) as shown in the following exhibit.
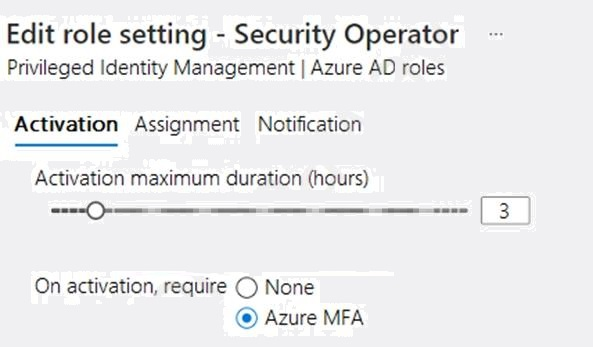
You add assignments to the Security Operator role as shown in the following table.
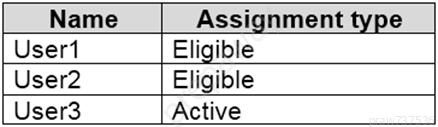
Which users can activate the Security Operator role?
Answer : D