Microsoft Azure Security Technologies AZ-500 Exam Questions
You are troubleshooting a security issue for an Azure Storage account You enable Azure Storage Analytics logs and archive It to a storage account. What should you use to retrieve the diagnostics logs?
Answer : A
SIMULATION
Lab Task
use the following login credentials as needed:
To enter your username, place your cursor in the Sign in box and click on the username below.
To enter your password. place your cursor in the Enter password box and click on the password below.
Azure Username: Userl -28681041@ExamUsers.com
Azure Password: GpOAe4@lDg
If the Azure portal does not load successfully in the browser, press CTRL-K to reload the portal in a new browser tab.
The following information is for technical support purposes only:
Lab Instance: 28681041
Task 10
You need to create a new Azure AD directory named 28681041.onmicrosoft.com. The new directory must contain a new user named user1@28681041.onmicrosoft.com.
Answer : A
To create a new Azure AD directory named 28681041.onmicrosoft.com that contains a new user named user1@28681041.onmicrosoft.com, you can follow these steps:
In the Azure portal, search for and selectAzure Active Directory.
In the left pane, selectDomains.
SelectAdd domain.
In the Add a custom domain pane, enter the following information:
Domain name: Enter the domain name you want to use. For example, 28681041.onmicrosoft.com.
Add domain: SelectAdd domain.
In the left pane, selectUsers.
SelectNew user.
In the New user pane, enter the following information:
User name: Enter the user name you want to use. For example, user1@28681041.onmicrosoft.com.
Name: Enter the name of the user.
Password: Enter a password for the user.
Groups: Select the groups you want the user to be a member of.
SelectCreate.
You can find more information on these topics in the following Microsoft documentation:
Add a custom domain name to Azure Active Directory
Create a new user in your organization - Azure Active Directory
You have an Azure Sentinel deployment.
You need to create a scheduled query rule named Rule1.
What should you use to define the query rule logic for Rule1?
Answer : C
https://docs.microsoft.com/en-us/azure/sentinel/tutorial-detect-threats-custom
You have 10 on-premises servers that run Windows Server 2019.
You plan to implement Azure Security Center vulnerability scanning for the servers.
What should you install on the servers first?
Answer : C
https://docs.microsoft.com/en-us/azure/azure-arc/servers/agent-overview
https://docs.microsoft.com/en-us/azure/security-center/deploy-vulnerability-assessment-vm
You have an Azure subscription that contains the resources shown in the following Table.
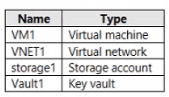
You plan to enable Microsoft Defender for Cloud for the subscription. Which resources can be protected by using Microsoft Defender for Cloud?
Answer : C
You have an Azure subscription named Subscription1.
You deploy a Linux virtual machine named VM1 to Subscription1.
You need to monitor the metrics and the logs of VM1.
D18912E1457D5D1DDCBD40AB3BF70D5D
What should you use?
Answer : A
You have an Azure environment.
You need to identify any Azure configurations and workloads that are non-compliant with ISO 27001
standards. What should you use?
Answer : C
https://docs.microsoft.com/en-us/azure/security-center/security-center-compliance-dashboard