Microsoft 70-411 Administering Windows Server Exam Practice Test
Your network contains an Active Directory domain named contoso.com. The domain contains a Web server named www.contoso.com. The Web server is available on the Internet.
You implement DirectAccess by using the default configuration.
Which settings should you configure in a Group Policy object (GPO)?
Answer : C
For DirectAccess, the NRPT must be configured with the namespaces of your intranet with a leading dot (for example, internal.contoso.com or . corp.contoso.com). For a DirectAccess client, any name request that matches one of these namespaces will be sent to the specified intranet Domain Name System (DNS) servers.
Include all intranet DNS namespaces that you want DirectAccess client computers to access.
There are no command line methods for configuring NRPT rules. You must use Group Policy settings. To configure the NRPT through Group Policy, use the Group Policy add-in at Computer Configuration \Policies\Windows Settings\Name Resolution Policy in the Group Policy object for DirectAccess clients. You can create a new NRPT rule and edit or delete existing rules. For more information, see Configure the NRPT with Group Policy.
Your network contains an Active Directory domain named contoso.com.
You create a new user account named Admin5.
You need to ensure that Admin5 can create Group Policy objects (GPOs) and link the GPOs to all of the organizational units (OUs) in the domain. Admin5 must be prevented from modifying GPOs created by other administrators.
Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.)
Answer : C, D
Your network contains one Active Directory domain named contoso.com. The forest functional level is Windows Server 2012. All servers run Windows Server 2012 R2. All client computers run Windows 8.1.
The domain contains 10 domain controllers and a read-only domain controller (RODC) named RODC01. All domain controllers and RODCs are hosted on a Hyper-V host that runs Windows Server 2012 R2.
You need to identify which domain controller must be online when cloning a domain controller.
Which cmdlet should you use?
Answer : D
One requirement for cloning a domain controller is an existing Windows Server 2012 DC that hosts the PDC emulator role. You can run the Get-ADDomain and retrieve which server has the PDC emulator role.
Example: Command Prompt: C:\PS>
Get-ADDomain
Output wouldinclude a line such as: PDCEmulator : Fabrikam-DC1.Fabrikam.com
Incorrect:
Not A: The Get-ADGroupMember cmdlet gets the members of an Active Directory group. Members can be users, groups, and computers.
Not E: The Get-ADOptionalFeature cmdlet gets an optional feature or performs a search to retrieve multiple optional features from an Active Directory.
Not F: The Get-ADAuthorizationGroup cmdlet gets the security groups from the specified user, computer or service accounts token.
http://blogs.technet.com/b/canitpro/archive/2013/06/12/step-by-step-domain-controller-cloning.aspx
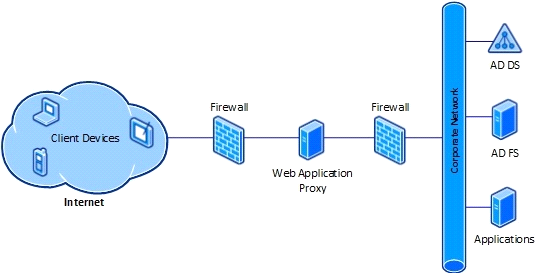
Your network contains an Active Directory domain named contoso.com.
You need to install and configure the Web Application Proxy role service.
What should you do?
Answer : A
Web Application Proxy is a new Remote Access role service in Windows Server 2012 R2.
Your network contains a Network Policy Server (NPS) server named Server1. The network contains a server named SQL1 that has Microsoft SQL Server 2008 R2 installed. All servers run Windows Server 2012 R2.
You configure NPS on Server1 to log accounting data to a database on SQL1.
You need to ensure that the accounting data is captured if SQL1 fails. The solution must minimize cost.
What should you do?
Answer : C
In Windows Server 2008 R2, an accounting configuration wizard is added to the Accounting node in the NPS console. By using the Accounting Configuration wizard, you can configure the following four accounting settings:
SQL logging only. By using this setting, you can configure a data link to a SQL Server that allows NPS to connect to and send accounting data to the SQL server. In addition, the wizard can configure the database on the SQL Server to ensure that the database is compatible with NPS SQL server logging.
Text logging only. By using this setting, you can configure NPS to log accounting data to a text file.
Parallel logging. By using this setting, you can configure the SQL Server data link and database. You can also configure text file logging so that NPS logs simultaneously to the text file and the SQL Server database.
SQL logging with backup. By using this setting, you can configure the SQL Server data link and database. In addition, you can configure text file logging that NPS uses if SQL Server logging fails.
Your network contains an Active Directory domain named contoso.com. All client computers run Windows 8.1.
The network contains a shared folder named FinancialData that contains five files.
You need to ensure that the FinancialData folder and its contents are copied to all of the client computers.
Which two Group Policy preferences should you configure? (Each correct answer presents part of the solution. Choose two.)
Answer : D, E
Folder preference items allow you to create, update, replace, and delete folders and their contents. (To configure individual files rather than folders, see Files Extension.) Before you create a Folder preference item, you should review the behavior of each type of action possible with this extension.
File preference items allow you to copy, modify the attributes of, replace, and delete files. (To configure folders rather than individual files, see Folders Extension.) Before you create a File preference item, you should review the behavior of each type of action possible with this extension.
You have a server named Server1 that runs Windows Server 2012 R2. Server1 has the File Server Resource Manager role service installed.
Each time a user receives an access-denied message after attempting to access a folder on Server1, an email notification is sent to a distribution list named DL1.
You create a folder named Folder1 on Server1, and then you configure custom NTFS permissions for Folder 1.
You need to ensure that when a user receives an access-denied message while attempting to access Folder1, an email notification is sent to a distribution list named DL2. The solution must not prevent DL1 from receiving notifications about other access-denied messages.
What should you do?
Answer : C
When using the email model each of the file shares, you can determine whether access requests to each file share will be received by the administrator, a distribution list that represents the file share owners, or both.
You can use the File Server Resource Manager console to configure the owner distribution list by editing the management properties of the classification properties.