Juniper JN0-335 Security, Specialist Exam Practice Test
You are asked to determine how much traffic a popular gaming application is generating on your network.
Which action will you perform to accomplish this task?
Answer : D
AppTrack is a feature of Juniper Networks firewall solutions that allows administrators to track applications, users, and the amount of traffic generated by those applications on the network. AppTrack can be enabled on specific security zones of the network to monitor traffic on those zones. This feature can be used to determine how much traffic a popular gaming application is generating on the network. For more information, please refer to the Juniper Networks JNCIS-SEC Study Guide.
AppTrack is a feature of the Junos OS that provides visibility into the applications and users on your network. It tracks the usage of applications and provides detailed reports on the amount of traffic generated by each application. By enabling AppTrack on the proper security zones, you can determine how much traffic a popular gaming application is generating on your network.
Which three statements about SRX Series device chassis clusters are true? (Choose three.)
Answer : B, C, E
B) Chassis cluster member devices synchronize configuration using the control link: This statement iscorrectbecause the control link is used for configuration synchronization among other functions.
C) A control link failure causes the secondary cluster node to be disabled: This statement iscorrectbecause a control link failure causes the secondary node to become ineligible for primary role and remain in secondary role until the control link is restored.
E) Heartbeat messages verify that the chassis cluster control link is working: This statement iscorrectbecause heartbeat messages are sent periodically over the control link to monitor its status.
You are asked to create an IPS-exempt rule base to eliminate false positives from happening.
Which two configuration parameters are available to exclude traffic from being examined? (Choose two.)
Answer : B
To exclude traffic from being examined by IPS, you can use the source IP address and/or destination port as criteria for the exemption. This is achieved by configuring an IPS-exempt rule base that includes specific exemption rules based on these criteria.
Which two statements are correct about chassis clustering? (Choose two.)
Answer : A, B
The node ID value ranges from 1 to 255 and is used to identify each device in the chassis cluster. The cluster ID is also used to identify each device, but it is not part of the node ID configuration. A system reboot is not required to activate changes to the cluster, but it is recommended to ensure that all changes are applied properly.
After JSA receives external events and flows, which two steps occur? (Choose two.)
Answer : B, C
Before formatting the data, the data is analyzed for relevant information. This is done to filter out any irrelevant data and to extract any useful information from the data. After the information is filtered, it is then formatted so that it can be stored in an asset database. After the data has been formatted, JSA will then respond with active measures.
Exhibit
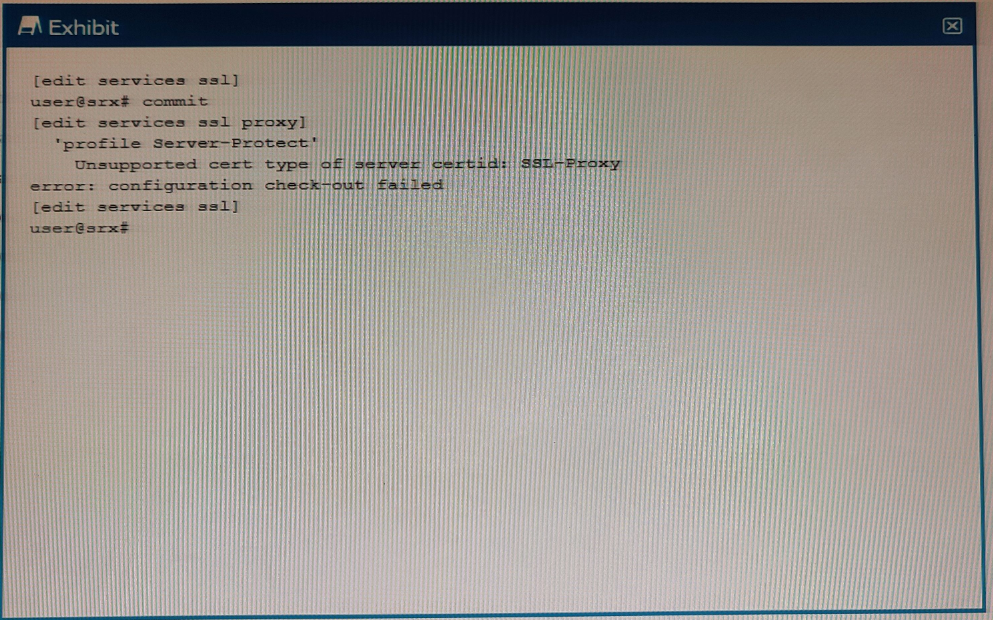
When trying to set up a server protection SSL proxy, you receive the error shown. What are two reasons for this error? (Choose two.)
You are asked to block malicious applications regardless of the port number being used.
In this scenario, which two application security features should be used? (Choose two.)