IIBA Certified Business Analysis Professional CBAP Exam Practice Test
Refer to the exhibit.
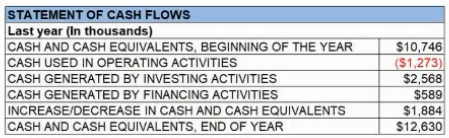
The table illustrate the statement of cash flower for a courier company for the last fiscal year:
Due to aggressive market competition the management of the company performed a strategy review and based on their0-findings and the current market conditions, they came up with strategic and tactical changes in order to keep a competitive market position.
In order to strength customer retention strategies through a new competitive advantage, the company is considering implementing a live parcel tracking system. The added value will be that the customers may determine the exact location on of the parcel whether it is in a warehouse, crossing the ocean through an overseas the exact location of th parcel whether it is in a warehouse, crossing the ocean through an overseas the ship, or travelling in a delivery truck at any time. The system tracks the location of the parcel by tracking the vehicle in which it is contained. However, for a group of old delivery trucks, it was noticed that the engine sound and vibration disturbed the tracking signal and caused of management would like to sell these vehicles and replace them with newer ones, the Chief Financial Officer (CFO) was strongly against that approach. The CFO argoad that instead of hanging tracking devices on the trucks body they can have the truck drivers manually send the truck send the truck location from a hand held mobile device every 20 minutes.
The CFO's resistance to replacing the older vehicles represents which type of cost?
Answer : C
The CFO's resistance to replacing the older vehicles and suggesting that the truck drivers manually send the truck location from a handheld mobile device every 20 minutes is an opportunity cost. An opportunity cost is the value of the next best alternative that is foregone as a result of making a decision. In this case, the opportunity cost of not replacing the older vehicles is the potential loss of customer satisfaction, retention, and loyalty due to the less accurate and less convenient tracking system. The CFO is choosing to save money on the upfront cost of buying new trucks, but at the expense of losing the competitive advantage and long-term benefits of having a live parcel tracking system.Reference:
IIBA BABOK Guide, Section 10.23, Decision Analysis
Opportunity Cost: Definition, Real-World Examples, How to Calculate, The Balance
What is Opportunity Cost and How to Calculate It, Investopedia
What type of requirements elicitation technique is the Delphi Technique?
Answer : A
The Delphi technique is a type of requirements elicitation technique that is based on a survey method. The Delphi technique involves sending a series of questionnaires to a group of experts who have knowledge or experience in the domain of the project or the solution. The questionnaires are designed to elicit opinions, ideas, or feedback on the requirements or the issues related to the project or the solution. The responses from the experts are collected and analyzed by a facilitator, who then provides a summary of the results and the areas of agreement or disagreement to the experts. The facilitator also prepares a new questionnaire based on the feedback and sends it back to the experts for another round of responses. This process is repeated until a consensus is reached or a sufficient level of information is obtained. The Delphi technique is useful for gathering requirements from a large and diverse group of stakeholders who are geographically dispersed or have conflicting views. The Delphi technique also helps to reduce the influence of dominant or biased individuals and to encourage honest and independent opinions. The Delphi technique is different from a workshop, which is a type of requirements elicitation technique that involves bringing together a group of stakeholders in a face-to-face or virtual setting to collaborate and exchange information on the requirements or the issues related to the project or the solution. The workshop is facilitated by a moderator, who guides the discussion and ensures the participation and contribution of all the attendees. The workshop is useful for generating a large number of ideas and finding solutions for a specific problem in a short time. The workshop also helps to build rapport and trust among the stakeholders and to resolve conflicts or misunderstandings. The Delphi technique is also different from a round table, which is a type of requirements elicitation technique that involves inviting a group of stakeholders to a formal or informal meeting to share their perspectives and insights on the requirements or the issues related to the project or the solution. The round table is moderated by a leader, who introduces the topic and encourages the dialogue and debate among the participants. The round table is useful for exploring different viewpoints and opinions and for gaining a deeper understanding of the problem and the context. The round table also helps to foster a sense of involvement and ownership among the stakeholders and to identify the areas of agreement or disagreement. The Delphi technique is not a prototyping, which is a type of requirements elicitation technique that involves creating a simplified or partial version of the solution or a component of the solution and presenting it to the stakeholders for feedback. The prototype can be either low-fidelity or high-fidelity, depending on the level of detail and functionality. The prototype is useful for validating and verifying the requirements and for demonstrating the feasibility and usability of the solution. The prototype also helps to reduce the ambiguity and uncertainty of the requirements and to increase the satisfaction and acceptance of the solution.Reference:
Top 10 Most Common Requirements Elicitation Techniques, paragraph 9
Software Engineering | Requirements Elicitation - GeeksforGeeks, paragraph 6
Delphi Method Forecasting Definition and How It's Used - Investopedia, paragraph 1
The Delphi Technique - Students 4 Best Evidence, paragraph 1
You are the business analyst for a large project in your organization. While your company prefers face-to-face communications there are many stakeholders located in different geographical locations.
How can you still effectively serve as a business analyst when the stakeholders are not collocated?
Which of the following establishes organizational checks and balances with a proper segregation of front, back, and middle office functions for effective risk management?
A business analyst (BA) is working on a payment system (PS) implementation. A set of systems which should interact with a new system has been identified. The business analyst defined that a user with role of "Supervisor" in the PS must pass a two-factor authentication before an execution of the functions: "Change system parameters" and "Set up new supervisor." A user must have the role of "Supervisor" to use the standard functions "Send mail notification" or "Send SMS notification".
The BA defined the following use cases:
* "Change system parameters"
* "Setup new supervisor"
* "Send mail notification"
* "Send SMS notification"
* "Send notification"
* "Pass a two-factor authentication"
The BA wants to create a Use Case diagram.
What standard relationship should be defined between "Change system parameters", "Setup new supervisor" and "Pass a two-factor authentication"?
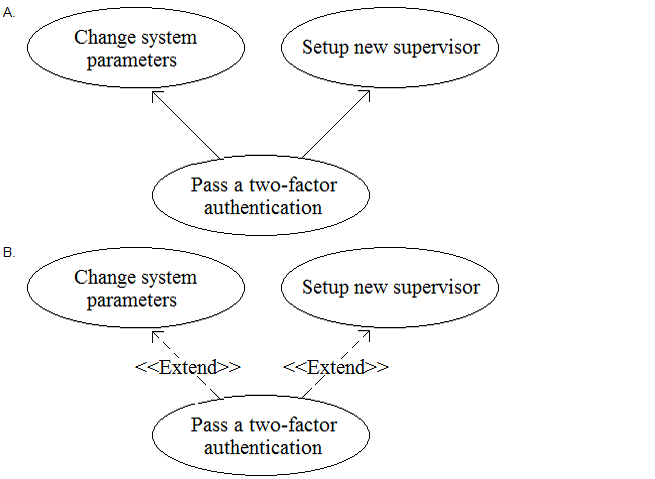
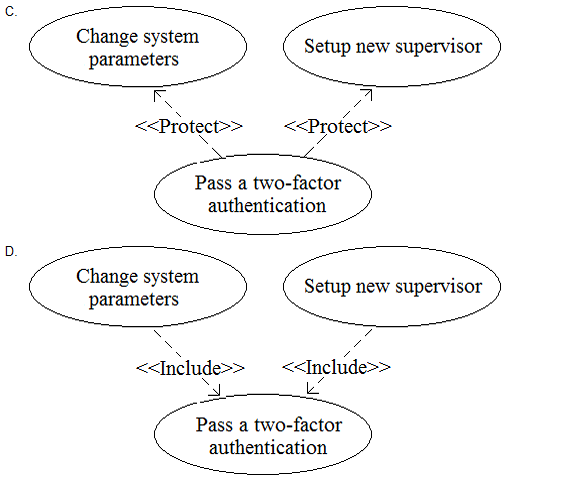
Answer : D
Option D shows the correct use of theincluderelationship between the three use cases. This means that the ''Pass a two-factor authentication'' use case is a mandatory part of both the ''Change system parameters'' and the ''Setup new supervisor'' use cases, and it always occurs whenever either of them is executed. The arrow points from the base use case to the included use case, as per the UML notation. Option C is incorrect because it uses theprotectrelationship, which is a non-standard extension of the UML notation. It indicates that the ''Pass a two-factor authentication'' use case is a security requirement for the other two use cases, but it does not specify how or when it is executed. Options A and B are incorrect because they use theextendrelationship, which means that the ''Pass a two-factor authentication'' use case is an optional extension of the other two use cases, and it only occurs under certain conditions. This does not reflect the requirement that the two-factor authentication is mandatory for both functions.Reference:
[A Guide to the Business Analysis Body of Knowledge (BABOK Guide), Version 3], Chapter 10: Techniques, pp. 424-425.
[UML 2.5 Specification], Chapter 18: Use Cases, pp. 637-638.
Which of the following process groups occurs at the beginning of the project?
Answer : C
The initiating process group is the one that occurs at the beginning of the project. It involves defining the project scope, objectives, and deliverables, obtaining the project authorization, identifying the key stakeholders, and establishing the project manager's authority. The initiating process group helps to set the vision and direction of the project, and aligns it with the strategic goals of the organization. The initiating process group also ensures that the project is feasible, viable, and desirable, and that it has the necessary support and resources to proceed.Reference:
CBAP / CCBA Certified Business Analysis Study Guide, 2nd Edition, page 47
Project Management Process Groups - Villanova University, under Initiating Process Group
The Five Traditional Process Groups Explained - Project Management Academy, under Initiating Phase
You are the business analyst for your organization. Management wants you to prioritize the identified requirements by the requirements that have the highest likelihood of success.
Why would management want you to prioritize the requirements with this factor even though some of the requirements may be difficult to implement?
Answer : B
Prioritizing requirements by the likelihood of success is a technique that can help build confidence and trust among the project stakeholders, especially if the project is complex, risky, or has a long duration. By delivering some of the requirements that have a high chance of success early in the project, the business analyst can demonstrate the value of the project and the effectiveness of the business analysis process. This can also help reduce resistance to change and increase user satisfaction and adoption. Some of the other factors that can be used to prioritize requirements are business value, urgency, dependency, risk, cost, and effort.Reference:
BABOK Guide v3, page 34, section 4.2.3. Prioritize Requirements.