HashiCorp Vault-Associate HashiCorp Certified: Vault Associate (002) Exam Practice Test
A developer mistakenly committed code that contained AWS S3 credentials into a public repository. You have been tasked with revoking the AWS S3 credential that was in the code. This credential was created using Vault's AWS secrets engine and the developer received the following output when requesting a credential from Vault.
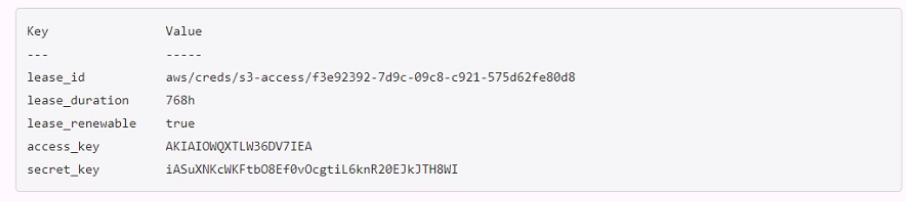
Which Vault command will revoke the lease and remove the credential from AWS?
Answer : A
You are performing a high number of authentications in a short amount of time. You're experiencing slow throughput for token generation. How would you solve this problem?
Which of the following describes usage of an identity group?
Answer : D
An identity group is a collection of entities that share some common attributes. An identity group can have one or more policies attached to it, which are inherited by all the members of the group. An identity group can also have subgroups, which can further refine the policies and attributes for a subset of entities.
What command creates a secret with the key "my-password" and the value "53cr3t" at path "my-secrets" within the KV secrets engine mounted at "secret"?
Answer : A
The vault kv put command writes the data to the given path in the K/V secrets engine. The command requires the mount path of the K/V secrets engine, the secret path, and the key-value pair to store. The mount path can be specified with the -mount flag or as part of the secret path. The key-value pair can be given as an argument or read from a file or stdin. The correct syntax for the command is:
vault kv put -mount=secret my-secrets/my-password 53cr3t
or
vault kv put secret/my-secrets my-password=53cr3t