GAQM CPEH-001 Certified Professional Ethical Hacker (CPEH) Exam Practice Test
You have performed the traceroute below and notice that hops 19 and 20 both show the same IP address. What can be inferred from this output?
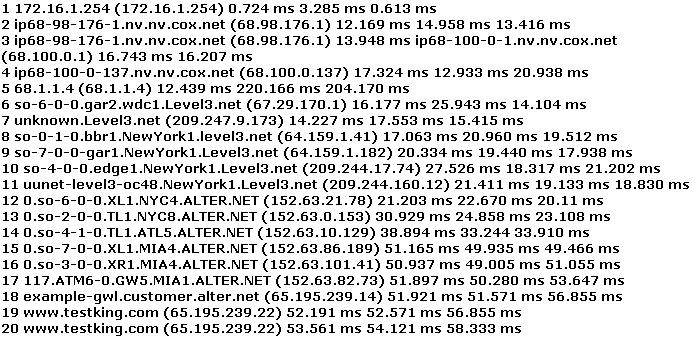
Answer : B
What is the tool Firewalk used for?
Answer : C
Firewalk is an active reconnaissance network security tool that attempts to determine what layer 4 protocols a given IP forwarding device 'firewall' will pass. Firewalk works by sending out TCP or UDP packets with a TTL one greater than the targeted gateway. If the gateway allows the traffic, it will forward the packets to the next hop where they will expire and elicit an ICMP_TIME_EXCEEDED message. If the gateway host does not allow the traffic, it will likely drop the packets and no response will be returned.
What is a primary advantage a hacker gains by using encryption or programs such as Loki?
Answer : D
Because the traffic is encrypted, an IDS cannot understand it or evaluate the payload.
Which of the following are potential attacks on cryptography? (Select 3)
Answer : B, C, E
A chosen-ciphertext attack (CCA) is an attack model for cryptanalysis in which the cryptanalyst chooses a ciphertext and causes it to be decrypted with an unknown key. Specific forms of this attack are sometimes termed 'lunchtime' or 'midnight' attacks, referring to a scenario in which an attacker gains access to an unattended decryption machine. In cryptography, a man-in-the-middle attack (MITM) is an attack in which an attacker is able to read, insert and modify at will, messages between two parties without either party knowing that the link between them has been compromised. The attacker must be able to observe and intercept messages going between the two victims. A replay attack is a form of network attack in which a valid data transmission is maliciously or fraudulently repeated or delayed. This is carried out either by the originator or by an adversary who intercepts the data and retransmits it, possibly as part of a masquerade attack by IP packet substitution (such as stream cipher attack).
You perform the above traceroute and notice that hops 19 and 20 both show the same IP address.

This probably indicates what?
Answer : C
Statistics from cert.org and other leading security organizations has clearly showed a steady rise in the number of hacking incidents perpetrated against companies. What do you think is the main reason behind the significant increase in hacking attempts over the past years?
Answer : D
Today you don't need to be a good hacker in order to break in to various systems, all you need is the knowledge to use search engines on the internet.
When referring to the Domain Name Service, what is denoted by a 'zone'?
Answer : B
A reasonable definition of a zone would be a portion of the DNS namespace where responsibility has been delegated.