Fortinet NSE7_ZTA-7.2 Fortinet NSE 7 - Zero Trust Access 7.2 Exam Practice Test
Which three statements are true about zero-trust telemetry compliance1? (Choose three.)
Answer : A, B, D
In the context of zero-trust telemetry compliance, the three true statements are:
A) FortiClient EMS creates dynamic policies using ZTNA tags: FortiClient EMS utilizes ZTNA (Zero Trust Network Access) tags to create dynamic policies based on the telemetry it receives from endpoints.
B) FortiClient checks the endpoint using the ZTNA tags provided by FortiClient EMS: FortiClient on the endpoint uses the ZTNA tags from FortiClient EMS to determine compliance with the specified security policies.
D) FortiOS provides network access to the endpoint based on the zero-trust tagging rules: FortiOS, the operating system running on FortiGate devices, uses the zero-trust tagging rules to make decisions on network access for endpoints.
The other options are not accurate in this context:
C) ZTNA tags are configured in FortiClient, based on criteria such as certificates and the logged-in domain: ZTNA tags are typically configured and managed in FortiClient EMS, not directly in FortiClient.
E) FortiClient EMS sends the endpoint information received through FortiClient Telemetry to FortiOS: While FortiClient EMS does process telemetry data, the direct sending of endpoint information to FortiOS is not typically described in this manner.
Zero Trust Telemetry in Fortinet Solutions.
FortiClient EMS and FortiOS Integration for ZTNA.
Which three statements are true about a persistent agent? (Choose three.)
Answer : B, C, E
A persistent agent is an application that works on Windows, macOS, or Linux hosts to identify them to FortiNAC Manager and scan them for compliance with an endpoint compliance policy. A persistent agent can support advanced custom scans and software inventory, apply supplicant configuration to a host, and be used for automatic registration and authentication.Reference:=
In which FortiNAC configuration stage do you define endpoint compliance?
Answer : C
exhibit.
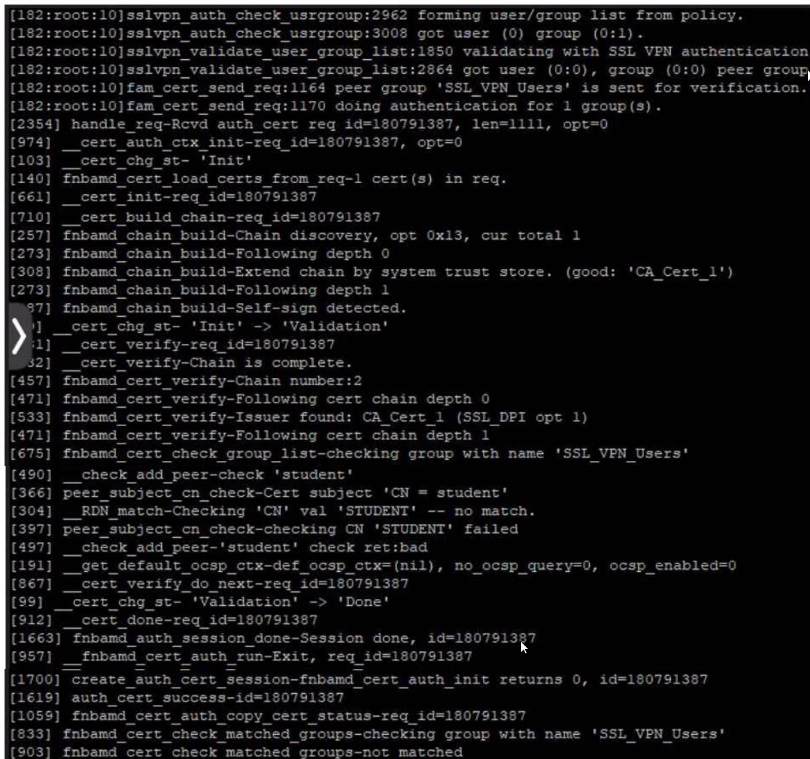
User student is not able to log in to SSL VPN
Given the output showing a real-time debug: which statement describes the login failure?
Answer : C
Given the output showing a real-time debug, the statement that describes the login failure is:
C) student is not part of the usergroup SSL_VPN_Users: The debug log contains a line that says 'fnbam_cert_check_group_list-checking group with name 'SSL_VPN_Users'' followed by 'peer_check_add_peer_check_student' and later 'RDN_match-Checking 'CN' val 'STUDENT' -- no match.' This suggests that the certificate presented has a common name (CN) of 'student', which does not match or is not authorized under the 'SSL_VPN_Users' group expected for successful authentication.
With the increase in loT devices, which two challenges do enterprises face? (Choose two.)
Answer : C, D
With the increase in IoT devices, enterprises face many challenges in securing and managing their network and data. Two of the most significant challenges are:
Exhibit.
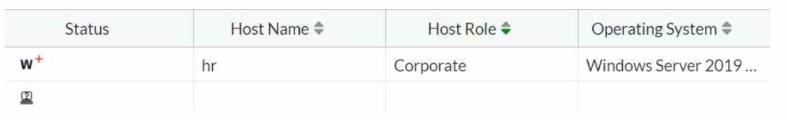
Which two statements are true about the hr endpoint? (Choose two.)
Answer : B, C
Based on the exhibit, the true statements about the hr endpoint are:
B) The endpoint is marked as a rogue device: The 'w' symbol typically indicates a warning or an at-risk status, which can be associated with an endpoint being marked as rogue due to failing to meet the security compliance requirements or other reasons.
C) The endpoint has failed the compliance scan: The 'w' symbol can also signify that the endpoint has failed a compliance scan, which is a common reason for an endpoint to be marked as at risk.
Which statement is true about FortiClient EMS in a ZTNA deployment?
Answer : A
In a ZTNA (Zero Trust Network Access) deployment, FortiClient EMS:
A) Uses endpoint information to grant or deny access to the network: FortiClient EMS plays a critical role in ZTNA by using information about the endpoint, such as its security posture and compliance status, to determine whether to grant or deny network access.
The other options do not accurately represent the role of FortiClient EMS in ZTNA:
B) Provides network and user identity authentication services: While it contributes to the overall ZTNA strategy, FortiClient EMS itself does not directly provide authentication services.
C) Generates and installs client certificates on managed endpoints: Certificate management is typically handled by other components in the ZTNA framework.
D) Acts as ZTNA access proxy for managed endpoints: FortiClient EMS does not function as an access proxy; its role is more aligned with endpoint management and policy enforcement.
FortiClient EMS in Zero Trust Network Access Deployment.
Role of FortiClient EMS in ZTNA.