Fortinet NSE6_FWF-6.4 Fortinet NSE 6 - Secure Wireless LAN 6.4 Exam Practice Test
What type of design model does FortiPlanner use in wireless design project?
How are wireless clients assigned to a dynamic VLAN configured for hash mode?
Answer : C
VLAN from the VLAN pool based on a hash of the current number of SSID clients and the number of entries in the VLAN pool.
Six APs are located in a remotely based branch office and are managed by a centrally hosted FortiGate. Multiple wireless users frequently connect and roam between the APs in the remote office.
The network they connect to, is secured with WPA2-PSK. As currently configured, the WAN connection between the branch office and the centrally hosted FortiGate is unreliable.
Which configuration would enable the most reliable wireless connectivity for the remote clients?
Answer : B
Look for ''Continued FortiAP operation when WiFi controller connection is down'' im the link here: https://docs.fortinet.com/document/fortiap/7.0.4/fortiwifi-and-fortiap-configuration-guide/442078/how-to-configure-a-fortiap-local-bridge-private-cloud-managed-ap
Refer to the exhibits.
Exhibit A
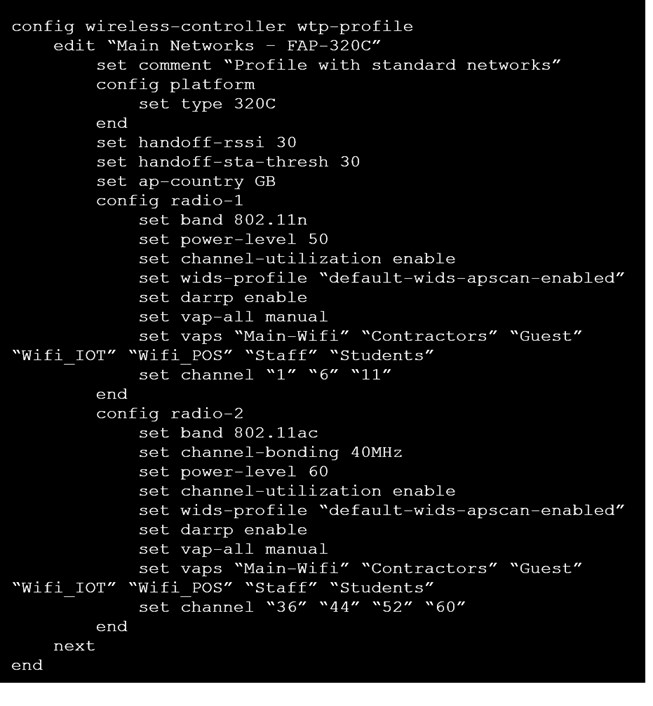
Exhibit B
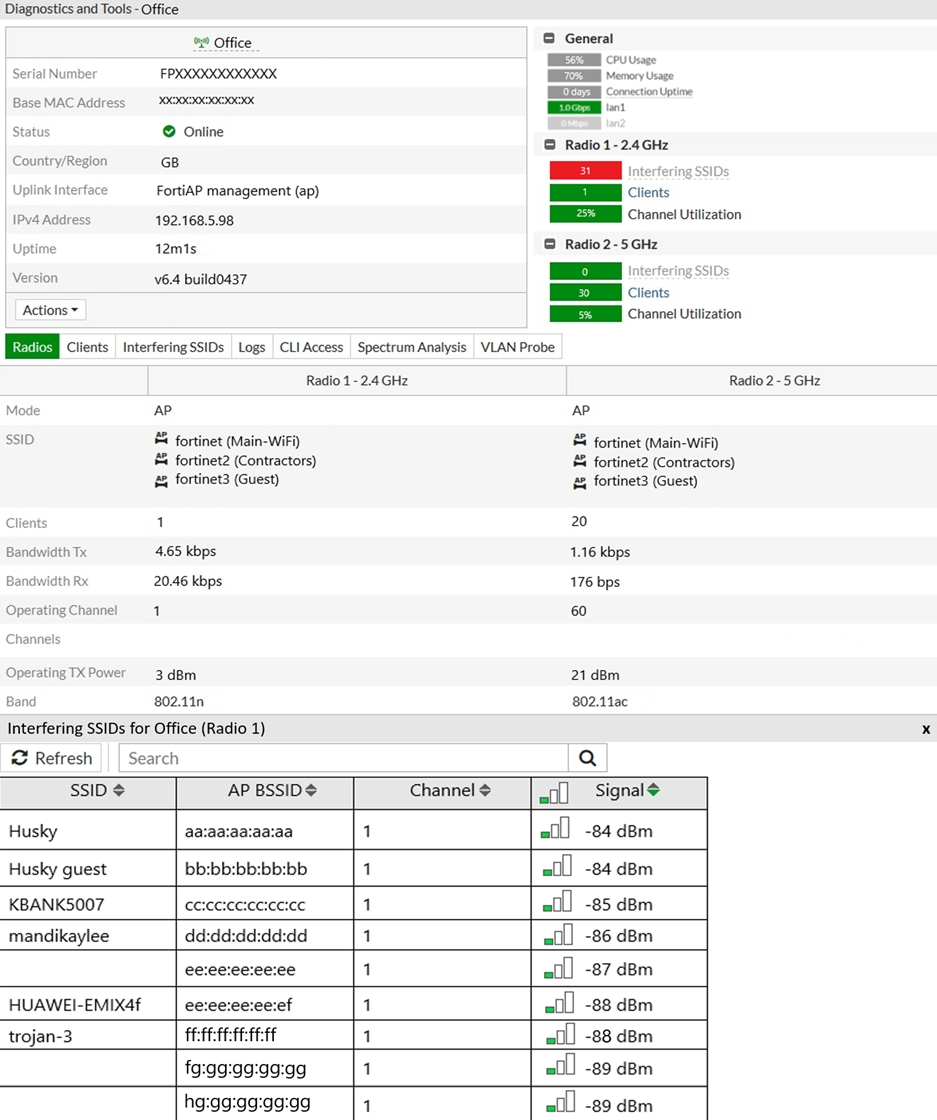
Exhibit C
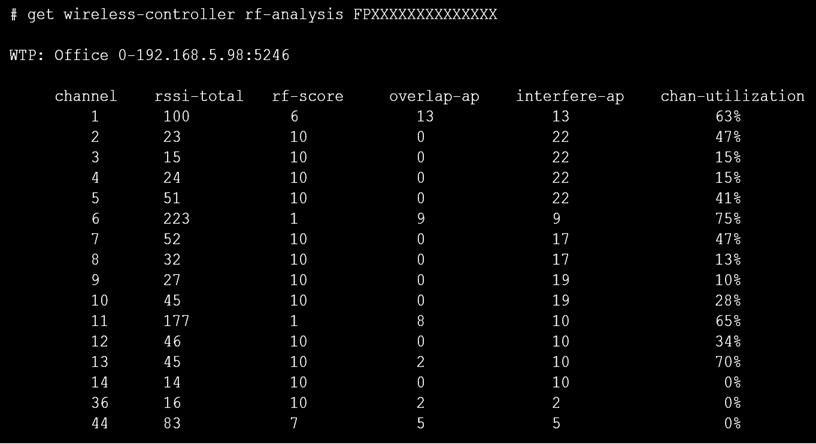
A wireless network has been installed in a small office building and is being used by a business to connect its wireless clients. The network is used for multiple purposes, including corporate access, guest access, and connecting point-of-sale and Io devices.
Users connecting to the guest network located in the reception area are reporting slow performance. The network administrator is reviewing the information shown in the exhibits as part of the ongoing investigation of the problem. They show the profile used for the AP and the controller RF analysis output together with a screenshot of the GUI showing a summary of the AP and its neighboring APs.
To improve performance for the users connecting to the guest network in this area, which configuration change is most likely to improve performance?
Answer : B
When configuring Auto TX Power control on an AP radio, which two statements best describe how the radio responds? (Choose two.)
Which administrative access method must be enabled on a FortiGate interface to allow APs to connect and function?
Answer : A
Refer to the exhibit.
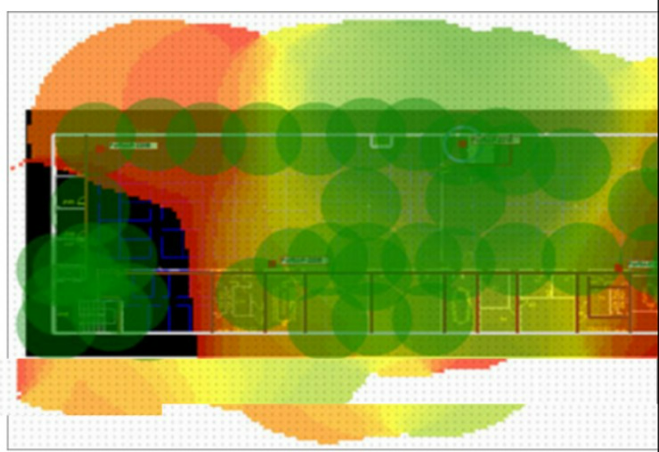
If the signal is set to -68 dB on the FortiPlanner site survey reading, which statement is correct regarding the coverage area?
A. Areas with the signal strength weaker than -68 dB are shown with black background.
B. Areas with the signal strength equal to -68 dB are zoomed in to provide better visibility.
C. Areas with the signal strength weaker than -68 dB are highlighted in orange and red to indicate that no signal was propagated by the APS.
Answer : D
The FortiPlanner site survey reading is a tool that shows the predicted signal strength of the wireless network based on the floor plan, the placement of the APs, and the propagation model. The signal strength is measured in decibels (dB), which is a logarithmic scale that indicates how much power the signal has. The higher the dB value, the stronger the signal.
The site survey reading allows the user to set a threshold value for the signal strength, which is -68 dB by default. This means that any area with a signal strength equal or stronger than -68 dB is considered to have adequate coverage for most wireless applications. These areas are highlighted in green circles on the floor plan. Any area with a signal strength weaker than -68 dB is considered to have poor coverage or no coverage at all. These areas are shown with different colors, such as yellow, orange, red, or black, depending on how weak the signal is.
Therefore, the correct answer is D. Areas with the signal strength equal or stronger than -68 dB are highlighted in green circles.
FortiPlanner 2.0 User Guide, page 28