Fortinet NSE4_FGT-7.2 Fortinet NSE 4 - FortiOS 7.2 Exam Practice Test
What is a reason for triggering IPS fail open?
Answer : A
Which statement about the deployment of the Security Fabric in a multi-VDOM environment is true?
Answer : A
FortiGate Security 7.2 Study Guide (p.436): 'When you configure FortiGate devices in multi-vdom mode and add them to the Security Fabric, each VDOM with its assigned ports is displayed when one or more devices are detected. Only the ports with discovered and connected devices appear in the Security Fabric view and, because of this, you must enable Device Detection on ports you want to have displayed in the Security Fabric. VDOMs without ports with connected devices are not displayed. All VDOMs configured must be part of a single Security Fabric.'
Refer to the exhibits.
Exhibit A shows a network diagram. Exhibit B shows the firewall policy configuration and a VIP object configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
The administrator disabled the WebServer firewall policy.
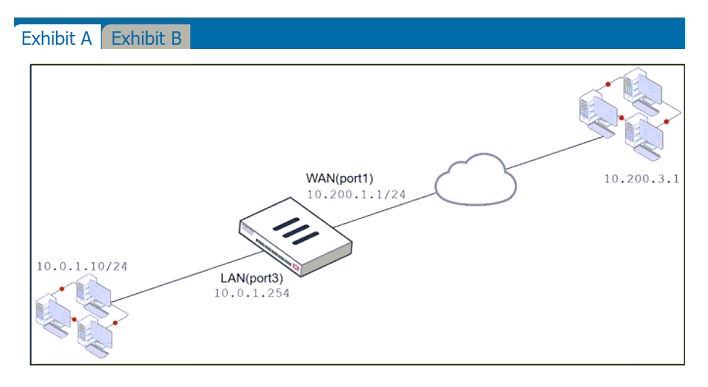

Which IP address will be used to source NAT the traffic, if a user with address 10.0.1.10 connects over SSH to the host with address 10.200.3.1?
Answer : C
Traffic is coming from LAN to WAN, matches policy Full_Access which has NAT enable, so traffic uses source IP address of outgoing interface. Simple SNAT.
What are two characteristics of FortiGate HA cluster virtual IP addresses? (Choose two.)
Answer : A, D
Fortigate Infrastructure 7.2 Study Guide page 301
FortiGate Infrastructure 7.2 Study Guide (p.301):
'FGCP automatically assigns the heartbeat IP addresses based on the serial number of each device. The IP address 169.254.0.1 is assigned to the device with the highest serial number.'
'A change in the heartbeat IP addresses may happen when a FortiGate device joins or leaves the cluster.'
'The HA cluster uses the heartbeat IP addresses to distinguish the cluster members and synchronize data.'
https://networkinterview.com/fortigate-ha-high-availability/
An administrator wants to simplify remote access without asking users to provide user credentials.
Which access control method provides this solution?
Answer : B
FortiGate Infrastructure 7.2 Study Guide (p.165): 'ZTNA access proxy allows users to securely access resources through an SSL-encrypted access proxy. This simplifies remote access by eliminating the use of VPNs.'
What are two functions of ZTNA? (Choose two.)
Answer : C, D
ZTNA (Zero Trust Network Access) is a security architecture that is designed to provide secure access to network resources for users, devices, and applications. It is based on the principle of 'never trust, always verify,' which means that all access to network resources is subject to strict verification and authentication.
Two functions of ZTNA are:
ZTNA provides a security posture check: ZTNA checks the security posture of devices and users that are attempting to access network resources. This can include checks on the device's software and hardware configurations, security settings, and the presence of malware.
ZTNA provides role-based access: ZTNA controls access to network resources based on the role of the user or device. Users and devices are granted access to only those resources that are necessary for their role, and all other access is denied. This helps to prevent unauthorized access and minimize the risk of data breaches.
Refer to exhibit.
An administrator configured the web filtering profile shown in the exhibit to block access to all social networking sites except Twitter. However, when users try to access twitter.com, they are redirected to a FortiGuard web filtering block page.
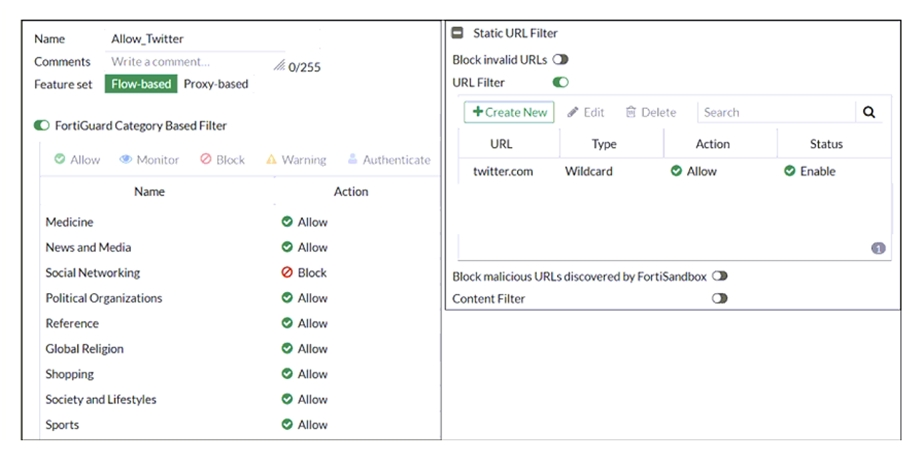
Based on the exhibit, which configuration change can the administrator make to allow Twitter while blocking all other social networking sites?
Answer : C
Based on the exhibit, the administrator has configured the FortiGuard Category Based Filter to block access to all social networking sites, and has also configured a Static URL Filter to block access to twitter.com. As a result, users are being redirected to a block page when they try to access twitter.com. To allow users to access twitter.com while blocking all other social networking sites, the administrator can make the following configuration change: On the Static URL Filter configuration, set Action to Exempt: By setting the Action to Exempt, the administrator can override the block on twitter.com that was specified in the FortiGuard Category Based Filter. This will allow users to access twitter.com, while all other social networking sites will still be blocked.