Fortinet FCP_ZCS_AD-7.4 FCP - Azure Cloud Security 7.4 Administrator Exam Practice Test
Your organization is planning to deploy FortiWeb in Azure to provide a web application security solution to its web servers. One of the requirements is to have granular control of the number of vCPUs and memory assigned to this resource.
Which cloud model could meet this requirement?
Answer : D
Infrastructure-as-a-Service (IaaS) allows you to deploy FortiWeb as a virtual machine in Azure, giving you granular control over vCPU and memory allocation. This model provides full flexibility over the compute resources and network configuration, which is essential for deploying and scaling security appliances like FortiWeb.
Refer to the exhibit.

Your organization is planning the implementation of a complex hub-to-spoke solution to meet automated large-scale branch connectivity with multiple regions, offering a diverse range of connectivity options.
Which Azure networking service can deliver a solution?
Answer : B
Azure Virtual WAN is designed for large-scale, automated, and global branch connectivity, supporting hub-and-spoke architectures across multiple regions. It enables centralized routing, hub-to-hub connectivity, and integrates with VPN, ExpressRoute, and SD-WAN solutions, making it ideal for complex, multi-region deployments as shown in the diagram.
Refer to the exhibit.
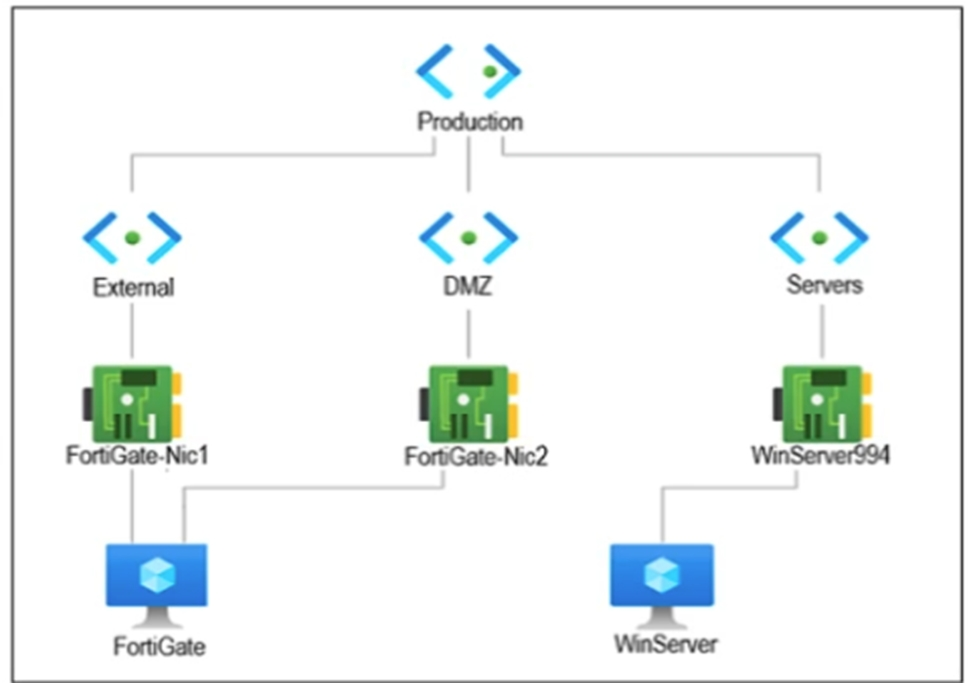
You are troubleshooting a network connectivity issue between two VMs that are deployed in Azure.
One VM is a FortiGate that has one interface in the DMZ subnet, which is in the Production VNet. The other VM is a Windows Server in the Servers subnet, which is also in the Production VNet. You cannot ping the Windows Server from the FortiGate VM.
What is the reason for this?
Answer : C
The FortiGate VM and the Windows Server VM are in different subnets but within the same Production virtual network, which means they can communicate by default unless restricted. Azure allows ICMP between subnets, but Windows VMs have ICMP blocked by default in their firewall settings. Therefore, the likely reason for the ping failure is that the Windows Server's firewall is blocking ICMP (ping) traffic.
Refer to the exhibits.
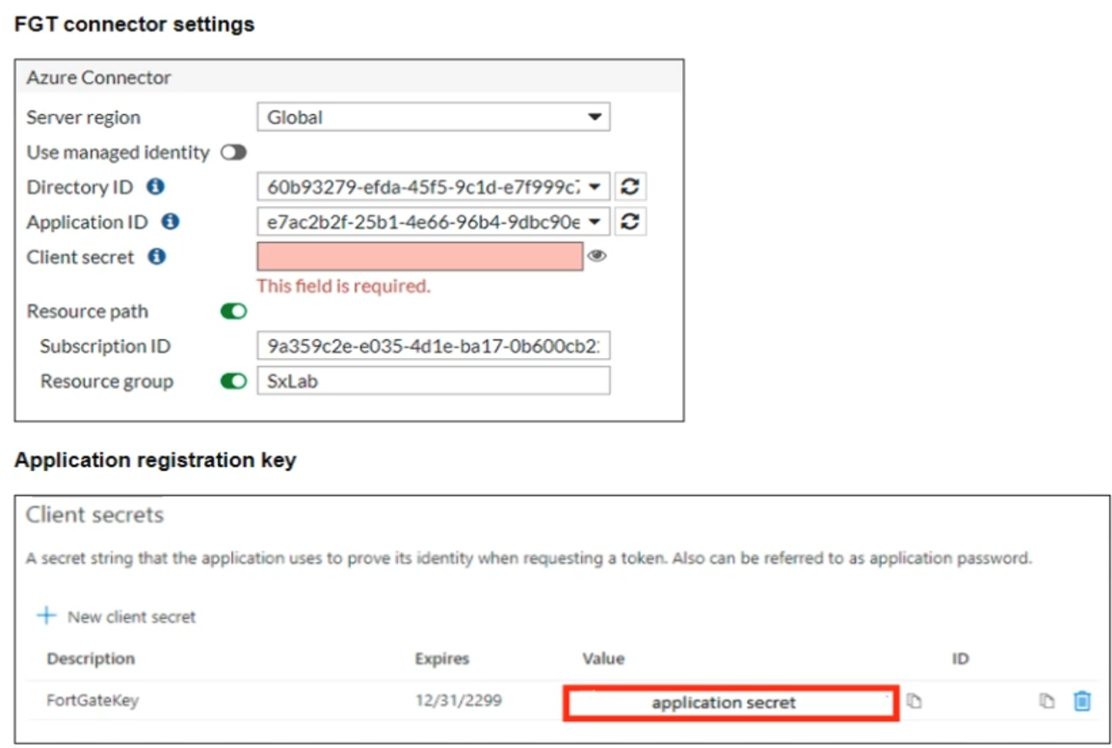
You are configuring an SDN connector for Azure on a FortiGate device You completed all the required steps on the Azure side. While configuring the FortiGate side, you notice that you did not save the client secret used in the Azure App Registration.
What is the quickest way to obtain the value of the client secret?
Answer : B
Azure does not allow you to view an existing client secret's value after creation for security reasons. If you did not save the client secret when it was first generated, the quickest and only option is to create a new client secret under the existing app registration and use the new value in your FortiGate configuration.
What is a limitation of the Network Security Groups (NSGs) in Azure?
Answer : B
A limitation of NSGs is that they are applied only at the subnet level or to network interfaces (vNICs), not directly to other resources like load balancers or application gateways. This means granular application-layer filtering is not supported, and NSGs primarily operate at Layers 3 and 4.
Refer to the exhibit.
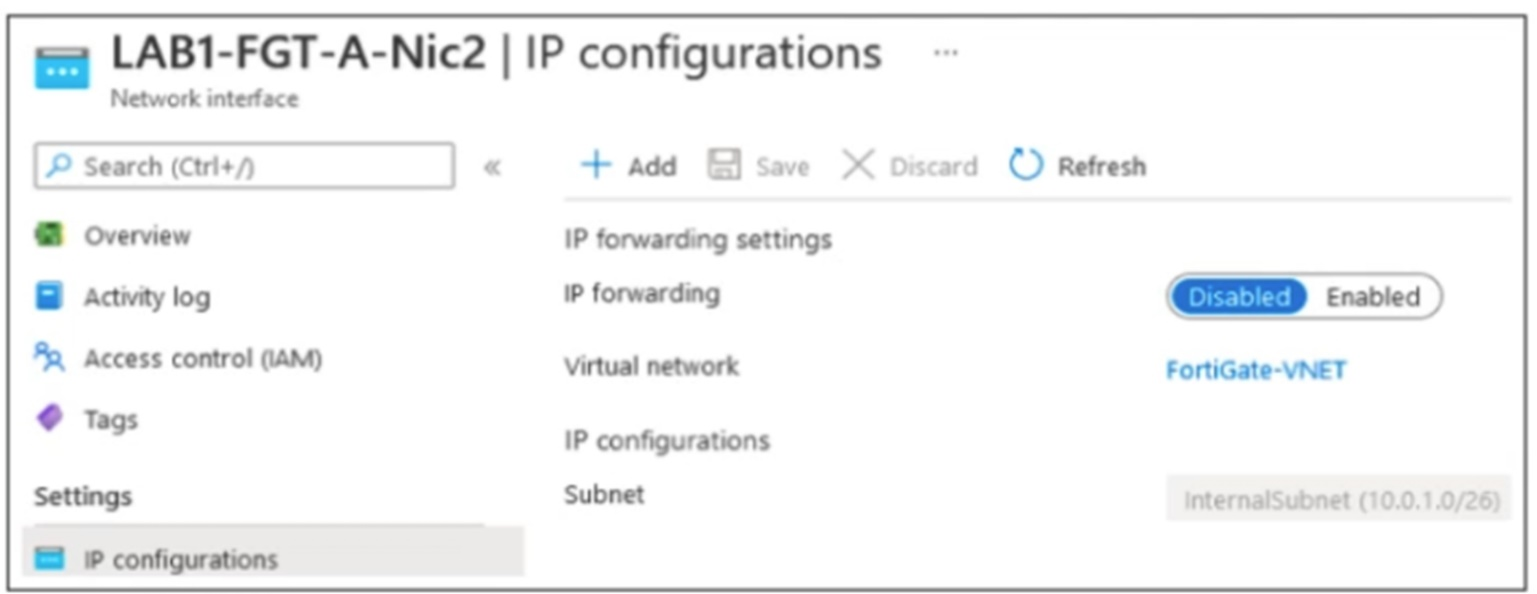
The exhibit shows some of the properties of a virtual NIC that is used by a FortiGate VM deployed in Azure.
The virtual NIC shown is connected to a subnet (10.0.1.0/26) with several VMs that will be accessing the internet through the FortiGate VM.
Which statement is true for this scenario?
Answer : C
For VMs in the 10.0.1.0/26 subnet to access the internet through the FortiGate VM, their default gateway must be changed to the internal IP address of the FortiGate's NIC in that subnet (e.g., LAB1-FGT-A-Nic2). This ensures traffic is routed through FortiGate for inspection and NAT, rather than directly using Azure's default system routes.
How are the configurations synchronized between two FortiGate VMs in an active-passive HA with SDN connector failover deployed from the Azure marketplace?
Answer : A
In an active-passive HA deployment of FortiGate VMs in Azure using the Marketplace template, configuration synchronization is handled via unicast FortiGate Clustering Protocol (FGCP). FGCP allows the primary unit to replicate its configuration and session information to the secondary unit, ensuring seamless failover.