Fortinet FCP_FML_AD-7.4 FCP - FortiMail 7.4 Administrator Exam Practice Test
Reter to the exhibits.
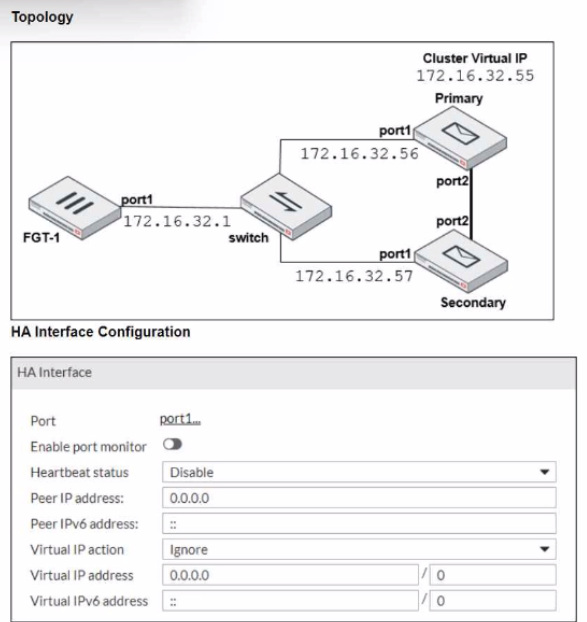
The exhibits display a topology diagram of a FortiMail cluster (Topology) and the primary HA interface configuration of the Primary FortiMail (HA Interface Configuration)
Which three actions are recommended when configuring the primary FortiMail HA interface? (Choose three.)
Answer : B, C, D
Refer to the exhibits, which display a topology diagram (Topology) and two FortiMail device configurations (FML1 Configuration and FML2 Configuration).
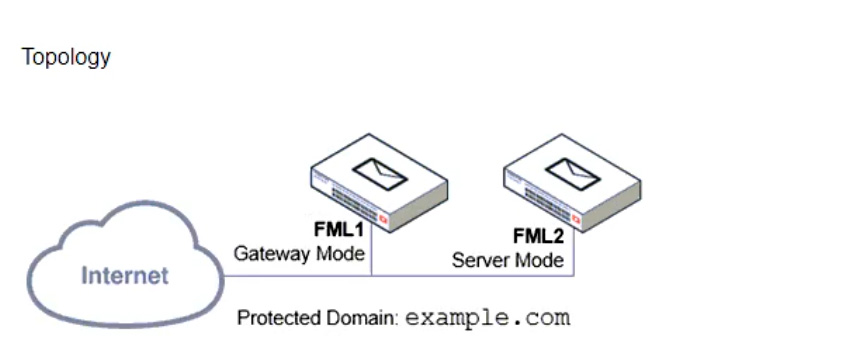
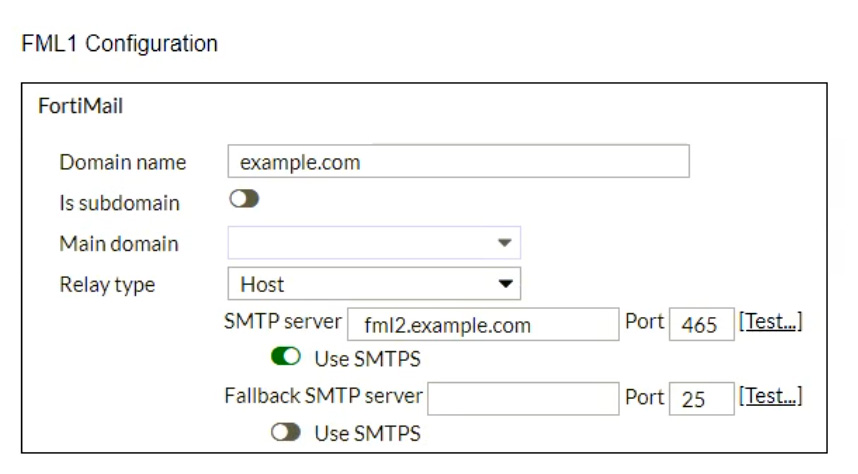

What is the expected outcome of SMTP sessions sourced from FML1 and destined for FML2?
Answer : D
When configuring a FortiMail HA group consisting of different models, which two statements are true? (Choose two.)
Answer : B, C
Refer to the exhibit, which displays a history log entry.
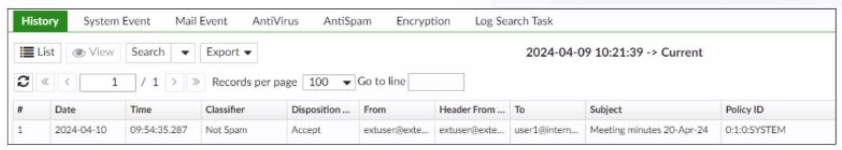
In the Policy ID column, why is the last policy ID value SYSTEM?
Answer : D
A mail user wants the ability to subscribe or publish to and from their FortiMail calendar using Thunderbird as their mail user agent (MUA). What information does this mail user need from their webmail User Preferences section?
Answer : C
Refer to the exhibit, which shows an inbound recipient policy.
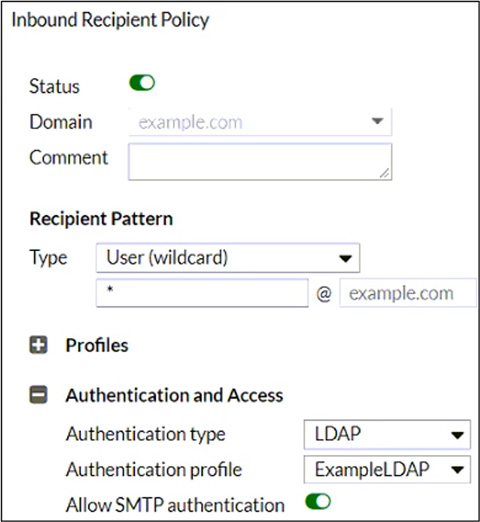
After creating the policy shown in the exhibit, an administrator discovers that clients can send unauthenticated emails using SMTP.
What must the administrator do to enforce authentication?
Answer : D
What are two disadvantages of configuring the dictionary and DLP scan rule aggressiveness too high? (Choose two.)
Answer : B, C