Fortinet FCP_FGT_AD-7.4 FCP - FortiGate 7.4 Administrator Exam Practice Test
Which two statements about equal-cost multi-path (ECMP) configuration on FortiGate are true? (Choose two.)
Answer : A, D
When SD-WAN is enabled on FortiGate, the load balancing algorithm for Equal-Cost Multi-Path (ECMP) is configured using the load-balance-mode parameter under SD-WAN settings. However, if SD-WAN is disabled, the ECMP load balancing algorithm can be configured under config system settings. This flexibility allows FortiGate to control traffic routing behavior based on the network configuration and requirements.
FortiOS 7.4.1 Administration Guide: ECMP Configuration
Refer to the exhibits, which show the firewall policy and the security profile for Facebook.
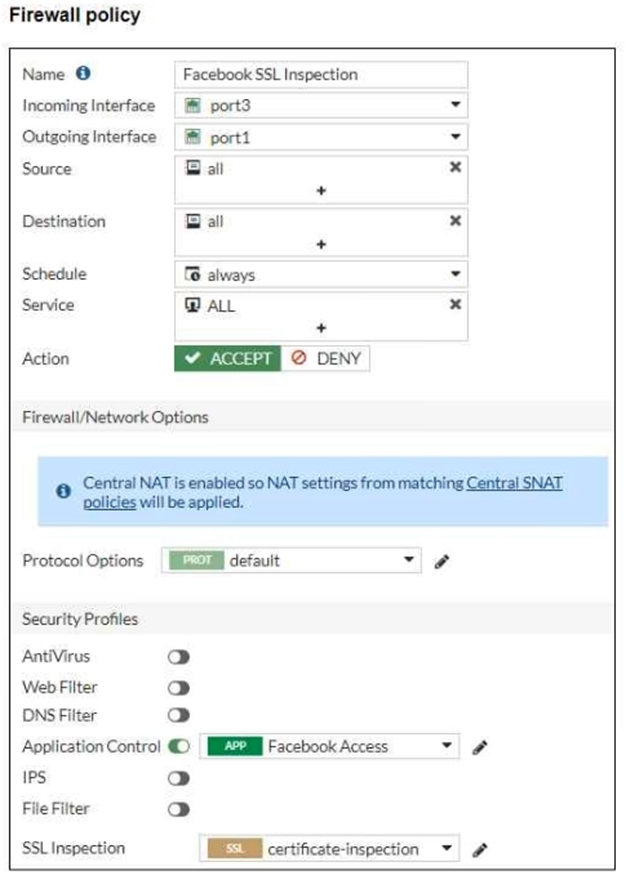
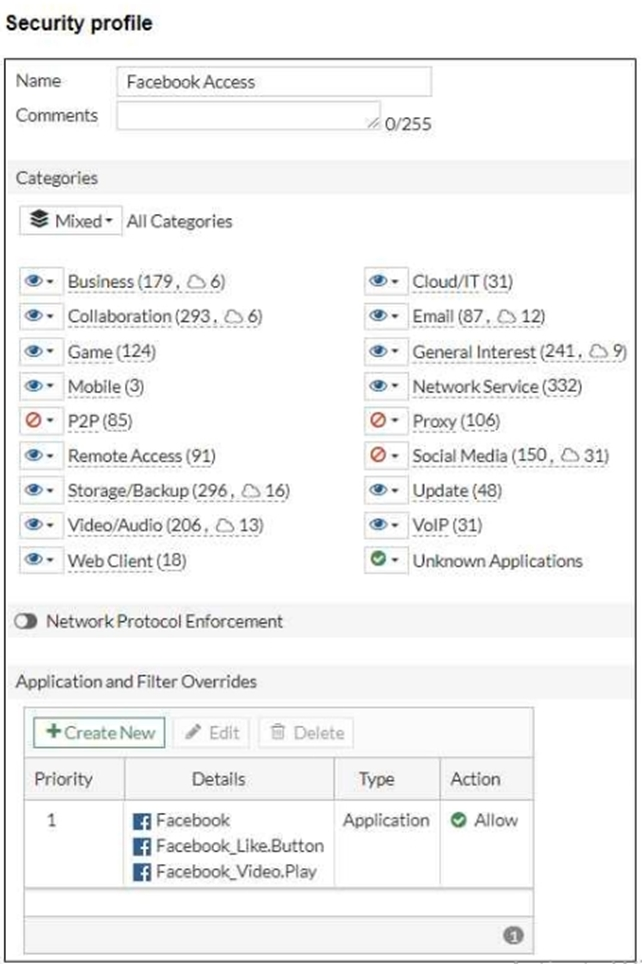
Users are given access to the Facebook web application. They can play video content hosted on Facebook but they are unable to leave reactions on videos or other types of posts.
Which part of the configuration must you change to resolve the issue?
Answer : A
Refer to exhibit.
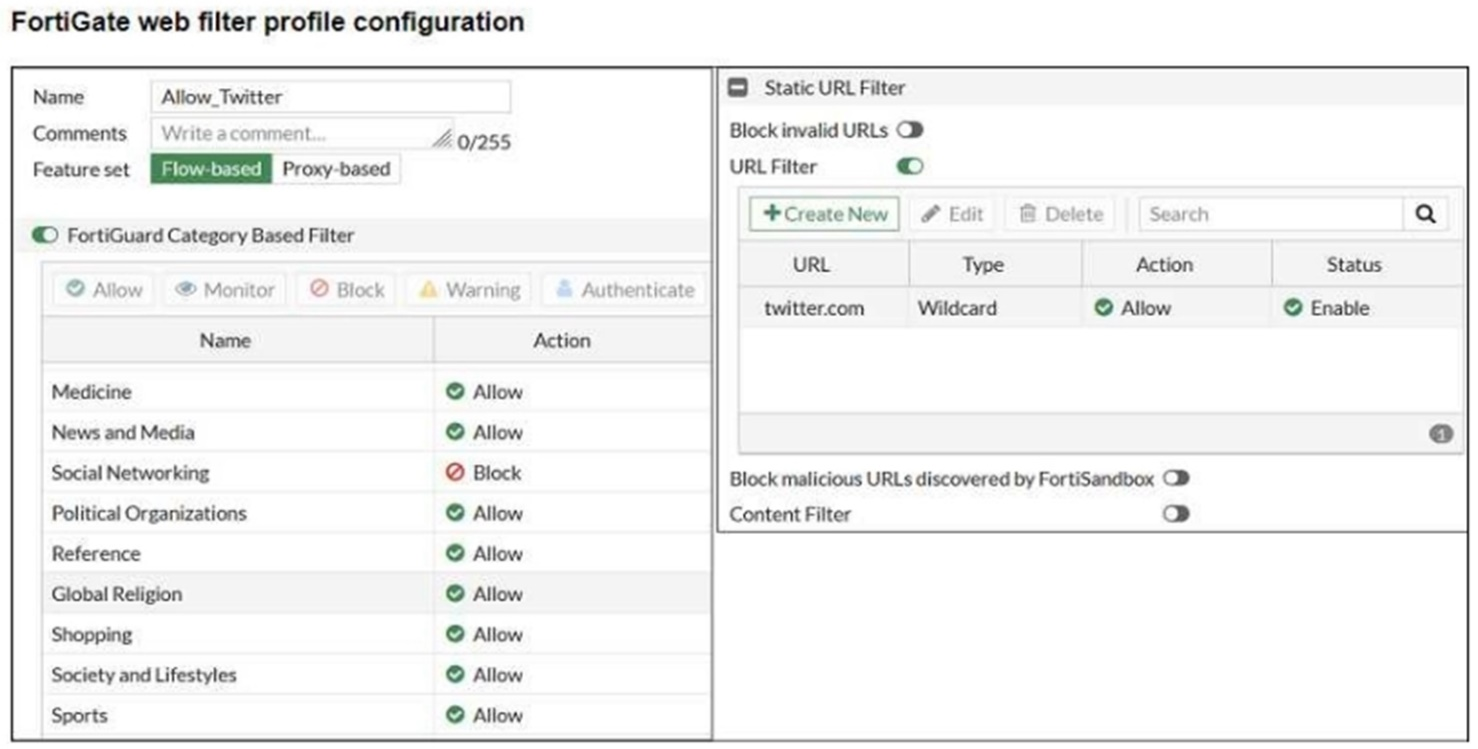
An administrator configured the web filtering profile shown in the exhibit to block access to all social networking sites except Twitter. However, when users try to access twitter.com, they are redirected to a FortiGuard web filtering block page.
Based on the exhibit, which configuration change can the administrator make to allow Twitter while blocking all other social networking sites?
Answer : D
In the current configuration, although 'twitter.com' is allowed in the Static URL Filter, the category 'Social Networking' is set to 'Block' under the FortiGuard Category Based Filter. To resolve the issue, setting the action to 'Exempt' in the Static URL Filter for 'twitter.com' will bypass the category-based block for this specific URL while still enforcing the block on other social networking sites.
Which method allows management access to the FortiGate CLI without network connectivity?
Answer : C
The serial console method allows management access to the FortiGate CLI without relying on network connectivity. This method involves directly connecting a computer to the FortiGate device using a serial cable (such as a DB-9 to RJ-45 cable or USB to RJ-45 cable) and using terminal emulation software to interact with the FortiGate CLI. This method is essential for situations where network-based access methods (such as SSH or Telnet) are not available or feasible.
FortiOS 7.4.1 Administration Guide: Console connection
Refer to the exhibit.
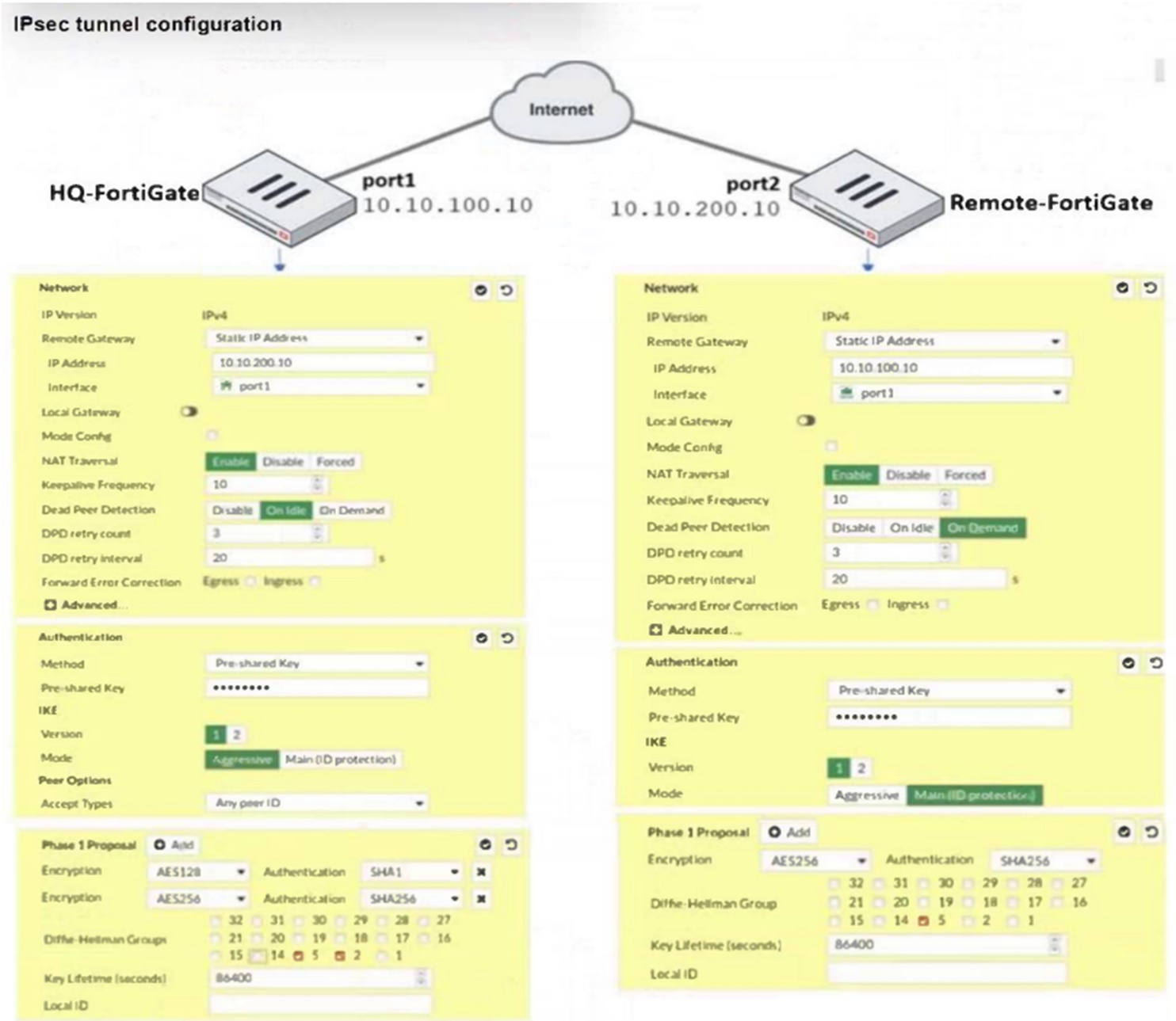
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 failed to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes can the administrator make to bring phase 1 up? (Choose two.)
Answer : B, D
Based on the phase 1 configuration and the diagram shown in the exhibit, the administrator can make the following two configuration changes to bring phase 1 up:
B . On Remote-FortiGate, set port2 as Interface: The diagram indicates that port2 is currently not selected under 'Interface' for Remote-FortiGate. Aligning this setting with HQ-FortiGate, which has port1 set as Interface, might resolve inconsistencies.
D . On HQ-FortiGate, set IKE mode to Main (ID protection): The current setting on HQ-FortiGate is Aggressive for IKE mode, while Remote-FortiGate is set to Main mode. Matching these settings may help in establishing phase 1 of the IPsec tunnel.
Refer to the exhibit.
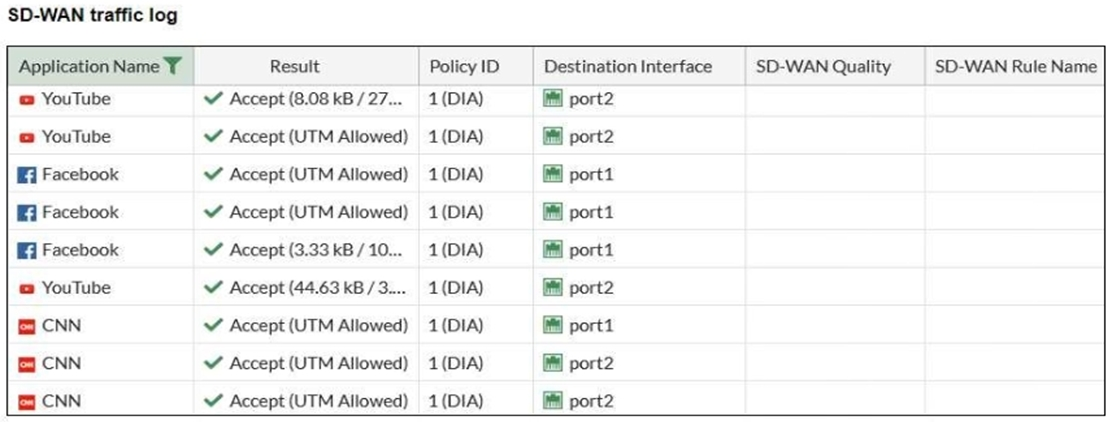
The administrator configured SD-WAN rules and set the FortiGate traffic log page to display SD-WAN-specific columns: SD-WAN Quality and SD-WAN Rule Name.
FortiGate allows the traffic according to policy ID 1. This is the policy that allows SD-WAN traffic.
Despite these settings the traffic logs do not show the name of the SD-WAN rule used to steer those traffic flows.
What can be the reason?
Answer : A
If the SD-WAN traffic logs do not show the specific SD-WAN rule name, it likely means that FortiGate is using the default or implicit SD-WAN rule to balance traffic. The implicit rule comes into effect when no explicit SD-WAN rule is matched, and as a result, the SD-WAN rule name is not displayed in the logs. The default behavior is to load balance the traffic across available interfaces based on SD-WAN strategy.
Which two settings are required for SSL VPN to function between two FortiGate devices? (Choose two.)
Answer : A, B
If fortigate is used as an SSL VPN client, it needs a ssl virtual tunnel interface to connect to the SSL VPN server. This is the client virtual interface that the vpn server will assign the temporary IP address to during the lifetime of an ssl connection. The SSL VPN server also needs a correct CA certificate to authenticate/trust client's certificate.