Fortinet FCP_FCT_AD-7.2 FCP - FortiClient EMS 7.2 Administrator Exam Practice Test
Refer to the exhibit.
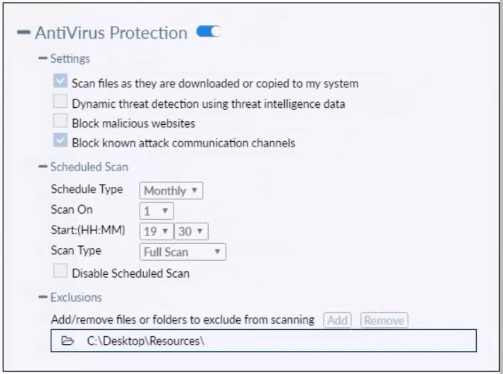
Based on the settings shown in the exhibit which statement about FortiClient behavior is true?
Answer : A
Action On Virus Discovery Warn the User If a Process Attempts to Access Infected Files Quarantine Infected Files. You can use FortiClient to view, restore, or delete the quarantined file, as well as view the virus name, submit the file to FortiGuard, and view logs. Deny Access to Infected Files Ignore Infected Files
Which two statements are true about the ZTNA rule? (Choose two.)
Answer : A, D
Understanding ZTNA Rule Configuration:
The ZTNA rule configuration shown in the exhibit defines how traffic is managed and controlled based on specific tags and conditions.
Evaluating Rule Components:
The rule includes security profiles to protect traffic by applying various security checks (A).
The rule also enforces access control by determining which endpoints can access the specified resources based on the ZTNA tag (D).
Eliminating Incorrect Options:
SNAT (Source Network Address Translation) is not mentioned as part of this ZTNA rule.
The rule does not define the access proxy but uses it to enforce access control.
Conclusion:
The correct statements about the ZTNA rule are that it applies security profiles to protect traffic (A) and enforces access control (D).
ZTNA rule configuration documentation from the study guides.
FortiClient EMS endpoint policies
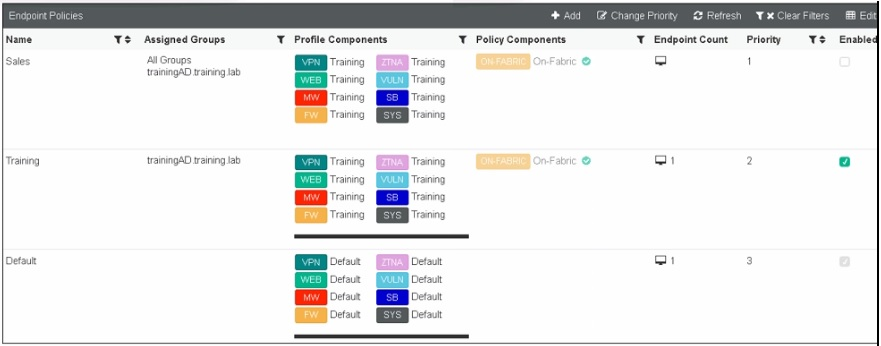
Refer to the exhibit, which shows multiple endpoint policies on FortiClient EMS. Which policy is applied to the endpoint in the AD group trainingAD
Answer : A
Observation of Endpoint Policies:
The exhibit shows multiple endpoint policies with their assigned groups, priority levels, and enabled status.
Evaluating Policy Assignment:
The Training policy is specifically assigned to the 'trainingAD.training.lab' group, with a higher priority than the Default policy.
Conclusion:
The correct policy applied to the endpoint in the AD group 'trainingAD' is the Training policy (A).
FortiClient EMS policy configuration and priority management documentation from the study guides.
Refer to the exhibit.
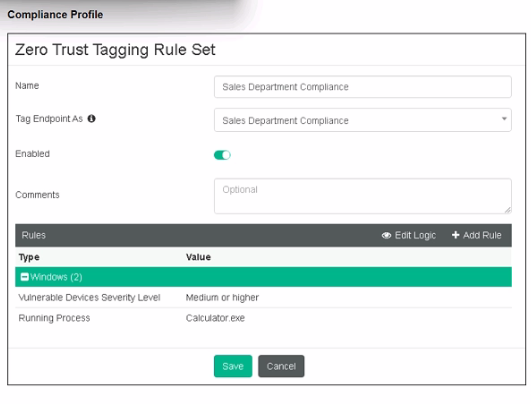
Based on the settings shown in the exhibit, which two actions must the administrator take to make the endpoint compliant? (Choose two.)
Answer : B, D
Observation of Compliance Profile:
The compliance profile shown in the exhibit includes rules for vulnerability severity level and running process (Calculator.exe).
Evaluating Actions for Compliance:
To make the endpoint compliant, the administrator needs to ensure that the vulnerability severity level is medium or higher is patched (D).
Additionally, the Calculator.exe application must be running on the endpoint (B).
Eliminating Incorrect Options:
Enabling the web filter profile (A) is not related to the compliance rules shown.
Integrating FortiSandbox (C) is not a requirement in the given compliance profile.
Conclusion:
The correct actions are to run the Calculator application on the endpoint (B) and patch applications with vulnerabilities rated as high or above (D).
FortiClient EMS compliance profile configuration documentation from the study guides.
What is the function of the quick scan option on FortiClient?
Answer : B
Understanding Quick Scan Function:
The quick scan option on FortiClient is designed to scan certain elements of the system quickly for threats.
Evaluating Scan Scope:
The quick scan specifically targets executable files, DLLs, and drivers that are currently running, providing a rapid assessment of the active components of the system.
Conclusion:
The correct answer is D, as it accurately describes the function of the quick scan option on FortiClient.
FortiClient scanning options documentation from the study guides.
Exhibit.
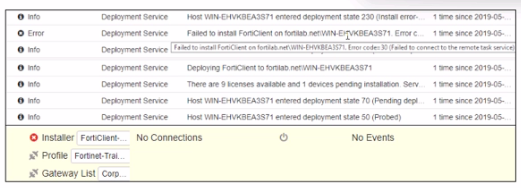
Based on the logs shown in the exhibit, why did FortiClient EMS tail to install FortiClient on the endpoint?
Answer : D
The deployment service error message may be caused by any of the following. Try eliminating them all, one at a time.
1. Wrong username or password in the EMS profile
2. Endpoint is unreachable over the network
3. Task Scheduler service is not running
4. Remote Registry service is not running
5. Windows firewall is blocking connection
Refer to the exhibit, which shows FortiClient EMS deployment, profiles.
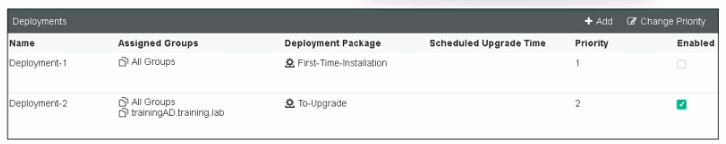
When an administrator creates a deployment profile on FortiClient EMS. which statement about the deployment profile is true?
Answer : A
Deployment Profiles Analysis:
Deployment-1 has the 'First-Time-Installation' package and is assigned to 'All Groups' with a priority of 1 but is not enabled.
Deployment-2 has the 'To-Upgrade' package, is assigned to both 'All Groups' and 'trainingAD.training.lab,' with a priority of 2 and is enabled.
Evaluating Deployment-2:
Deployment-2 will upgrade FortiClient on both 'All Groups' and 'trainingAD.training.lab' since it is enabled and assigned to these groups. This includes both AD (Active Directory) groups and workgroups.
Conclusion:
Since Deployment-2 is set to upgrade FortiClient on all the assigned groups and workgroups, the correct answer is A.
FortiClient EMS deployment and profile documentation from the study guides.