Eccouncil 312-96 Certified Application Security Engineer (CASE) JAVA Exam Practice Test
Suppose there is a productList.jsp page, which displays the list of products from the database for the requested product category. The product category comes as a request parameter value. Which of the following line of code will you use to strictly validate request parameter value before processing it for execution?
Answer : B
Identify the type of encryption depicted in the following figure.
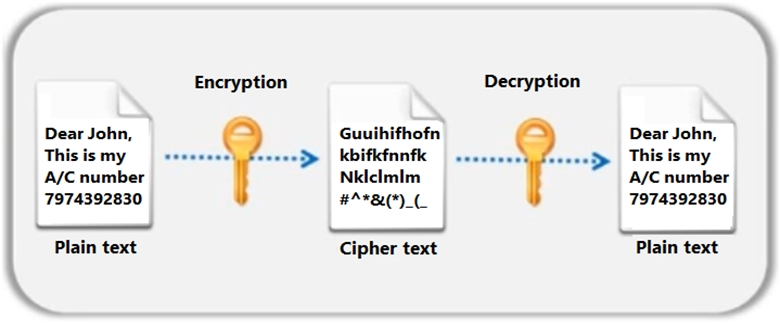
Answer : C
The developer wants to remove the HttpSessionobject and its values from the client' system.
Which of the following method should he use for the above purpose?
Answer : D
During his secure code review, John, an independent application security expert, found that the developer has used Java code as highlighted in the following screenshot. Identify the security mistake committed by the developer?
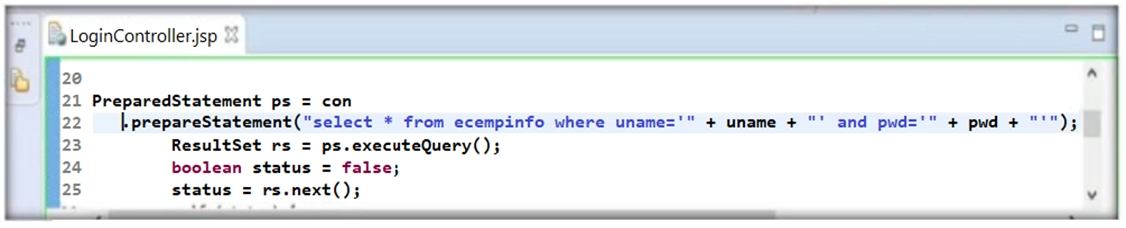
Answer : B
Identify the type of attack depicted in the figure below:
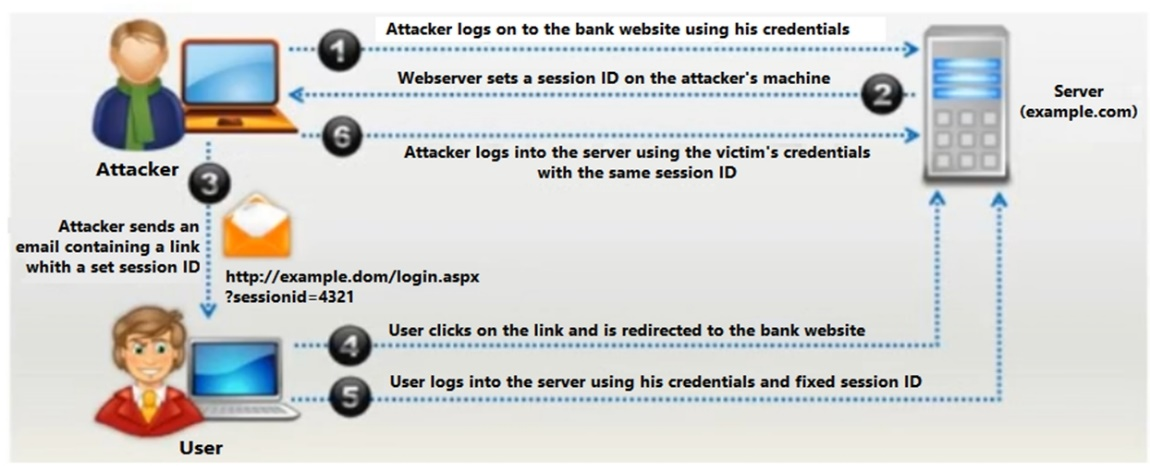
Answer : D
Thomas is not skilled in secure coding. He neither underwent secure coding training nor is aware of the consequences of insecure coding. One day, he wrote code as shown in the following screenshot. He passed 'false' parameter to setHttpOnly() method that may result in the existence of a certain type of vulnerability. Identify the attack that could exploit the vulnerability in the above case.
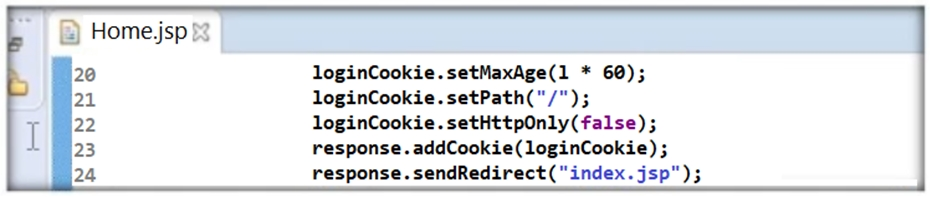
Answer : B
Which of the following method will you use in place of ex.printStackTrace() method to avoid printing stack trace on error?
Answer : C