Eccouncil 312-39 Certified SOC Analyst Exam Practice Test
Which of the following service provides phishing protection and content filtering to manage the Internet experience on and off your network with the acceptable use or compliance policies?
Answer : C
Which of the following is a correct flow of the stages in an incident handling and response (IH&R) process?
Answer : B
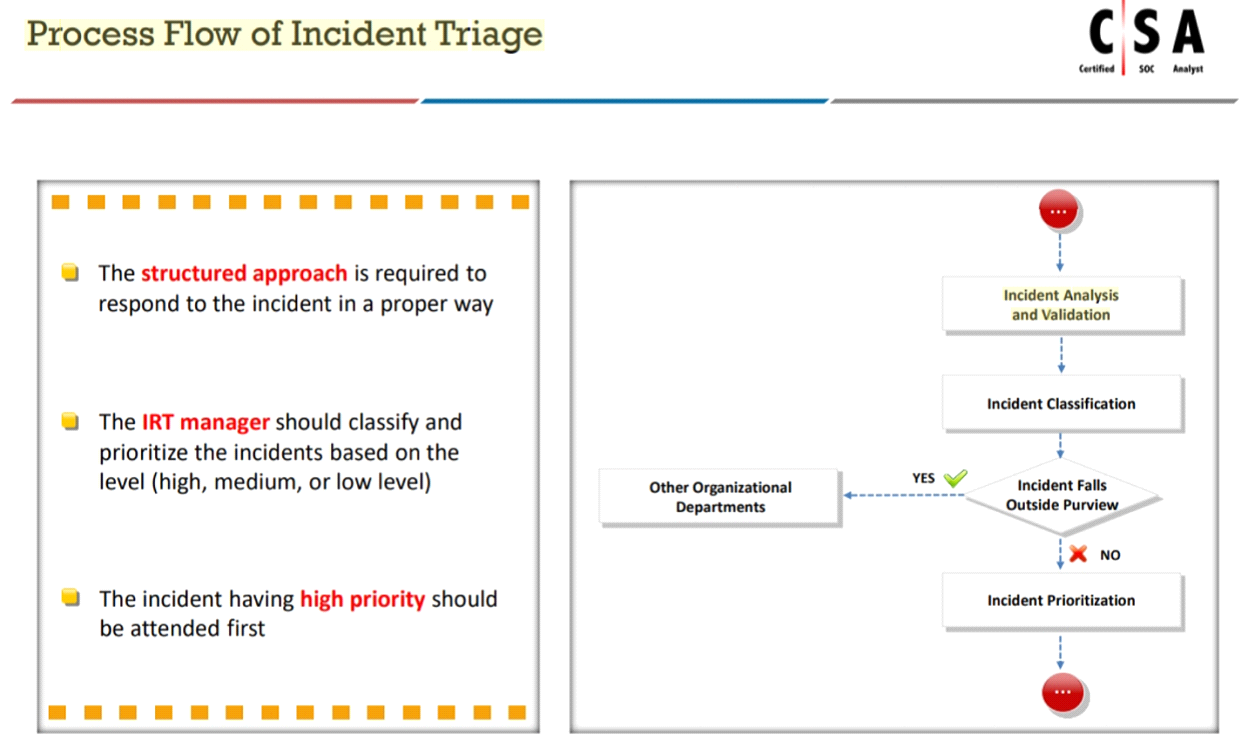
Mike is an incident handler for PNP Infosystems Inc. One day, there was a ticket raised regarding a critical incident and Mike was assigned to handle the incident. During the process of incident handling, at one stage, he has performed incident analysis and validation to check whether the incident is a true incident or a false positive.
Identify the stage in which he is currently in.
Answer : C
What does [-n] in the following checkpoint firewall log syntax represents?
fw log [-f [-t]] [-n] [-l] [-o] [-c action] [-h host] [-s starttime] [-e endtime] [-b starttime endtime] [-u unification_scheme_file] [-m unification_mode(initial|semi|raw)] [-a] [-k (alert name|all)] [-g] [logfile]
Answer : A
What does the Security Log Event ID 4624 of Windows 10 indicate?
Answer : C
Identify the type of attack, an attacker is attempting on www.example.com website.
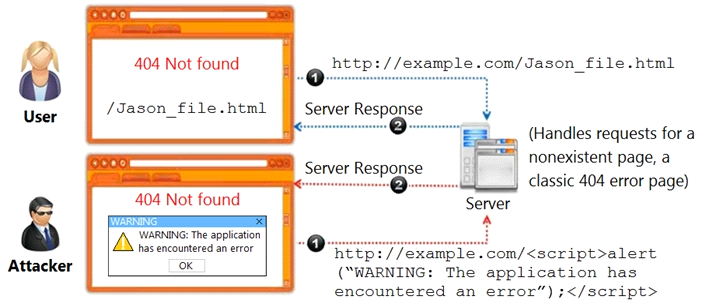
Answer : A
The threat intelligence, which will help you, understand adversary intent and make informed decision to ensure appropriate security in alignment with risk.
What kind of threat intelligence described above?
Answer : B