Docker DCA Docker Certified Associate Exam Practice Test
The Kubernetes yaml shown below describes a networkPolicy.
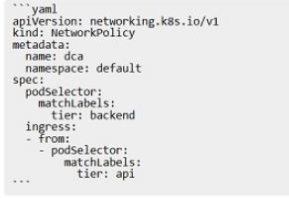
Will the networkPolicy BLOCK this trafftc?
Solution. a request issued from a pod bearing only the tier: frontend label, to a pod bearing the tier: backend label
In Kubernetes, to mount external storage to a filesystem path in a container within a pod, you would use a volume in the pod specification. This volume is populated with a persistentVolumeClaim that is bound to an existing persistentVolume. The persistentVolume is defined and managed by the storageClass which provides dynamic or static provisioning of the volume and determines what type of storage will be provided1. Reference:
* Dynamic Volume Provisioning | Kubernetes
Is this a supported user authentication method for Universal Control Plane?
Solution: Docker ID
Which networking drivers allow you to enable multi-host network connectivity
between containers?
Answer : D
: The networking drivers that allow you to enable multi-host network connectivity between containers are bridge, macvlan, ipvlan, and overlay. These drivers create networks that can span multiple Docker hosts, and therefore enable containers on different hosts to communicate with each other. The other drivers, such as host, user-defined, and none, create networks that are either isolated or limited to a single host. Here is a brief overview of each driver and how it supports multi-host networking:
* bridge: The bridge driver creates a network that connects containers on the same host using a Linux bridge. However, it can also be used to create a network that connects containers across multiple hosts using an external key-value store, such as Consul, Etcd, or ZooKeeper. This feature is deprecated and not recommended, as it requires manual configuration and has some limitations. The preferred driver for multi-host networking is overlay1.
* macvlan: The macvlan driver creates a network that assigns a MAC address to each container, making it appear as a physical device on the network. This allows the containers to communicate with other devices on the same network, regardless of the host they are running on. The macvlan driver can also use 802.1q trunking to create sub-interfaces and isolate traffic between different networks2.
* ipvlan: The ipvlan driver creates a network that assigns an IP address to each container, making it appear as a logical device on the network. This allows the containers to communicate with other devices on the same network, regardless of the host they are running on. The ipvlan driver can also use different modes, such as l2, l3, or l3s, to control the routing and isolation of traffic between different networks3.
* overlay: The overlay driver creates a network that connects multiple Docker daemons together using VXLAN tunnels. This allows the containers to communicate across different hosts, even if they are on different networks. The overlay driver also supports encryption, load balancing, and service discovery. The overlay driver is the default and recommended driver for multi-host networking, especially for Swarm services4.
* Use bridge networks
* Use macvlan networks
* Use ipvlan networks
* Use overlay networks
You are running only Kubernetes workloads on a worker node that requires
maintenance, such as installing patches or an OS upgrade.
Which command must be run on the node to gracefully terminate all pods on
the node, while marking the node as unschedulable?
Answer : C
The command kubectl drain <node name> is the correct one to run on the node to gracefully terminate all pods on the node, while marking the node as unschedulable. This command will safely evict all the pods from the node before you perform maintenance on the node, such as installing patches or an OS upgrade1. It will respect the PodDisruptionBudgets you have specified, if any, and allow the pod's containers to gracefully terminate1. It will also mark the node as unschedulable, so that no new pods can be scheduled on the node until it is ready1.
The other commands are not correct because:
* docker swarm leave will make the node leave the swarm cluster, but it will not affect the Kubernetes workloads on the node2.
* docker node update -availability drain <node name> will change the availability of the node to drain, which means that no new tasks can be assigned to the node, but it will not terminate the existing pods on the node3.
* kubectl cordon <node name> will mark the node as unschedulable, but it will not evict the pods on the node4.
* Safely Drain a Node | Kubernetes
* [docker swarm leave | Docker Docs]
* [docker node update | Docker Docs]
* [kubectl cordon | Kubernetes Docs]
Which docker run` flag lifts cgroup limitations?
Answer : A
The --privileged flag lifts all the cgroup limitations for a container, as well as other security restrictions imposed by the Docker daemon1. This gives the container full access to the host's devices, resources, and capabilities, as if it was running directly on the host2. This can be useful for certain use cases that require elevated privileges, such as running Docker-in-Docker or debugging system issues3. However, using the --privileged flag also poses a security risk, as it exposes the host to potential attacks or damages from the container4. Therefore, it is not recommended to use the --privileged flag unless absolutely necessary, and only with trusted images and containers.
The other options are not correct because they do not lift all the cgroup limitations for a container, but only affect specific aspects of the container's resource allocation or isolation:
* The --cpu-period flag sets the CPU CFS (Completely Fair Scheduler) period for a container, which is the length of a CPU cycle in microseconds. This flag can be used in conjunction with the --cpu-quota flag to limit the CPU time allocated to a container. However, this flag does not affect other cgroup limitations, such as memory, disk, or network.
* The --isolation flag sets the isolation technology for a container, which is the mechanism that separates the container from the host or other containers. This flag is only available on Windows containers, and can be used to choose between process, hyperv, or process-isolated modes. However, this flag does not affect the cgroup limitations for a container, but only the level of isolation from the host or other containers.
* The --cap-drop flag drops one or more Linux capabilities for a container, which are the privileges that a process can use to perform certain actions on the system. This flag can be used to reduce the attack surface of a container by removing unnecessary or dangerous capabilities. However, this flag does not affect the cgroup limitations for a container, but only the capabilities granted to the container by the Docker daemon.
* Runtime privilege and Linux capabilities
* Docker Security: Using Containers Safely in Production
* Docker run reference
* Docker Security: Are Your Containers Tightly Secured to the Ship? SlideShare
* [Secure Engine]
* [Configure a Pod to Use a Limited Amount of CPU]
* [Limit a container's resources]
* [Managing Container Resources]
* [Isolation modes]
* [Windows Container Isolation Modes]
* [Windows Container Version Compatibility]
* [Docker and Linux Containers]
* [Docker Security Cheat Sheet]
* [Docker Security: Using Containers Safely in Production]
Does this command create a swarm service that only listens on port 53 using the UDP protocol?
Solution. 'docker service create -name dns-cache -p 53:53/udp dns-cache"
Answer : B
= The command 'docker service create -name dns-cache -p 53:53/udp dns-cache' is not correct and will not create a swarm service that only listens on port 53 using the UDP protocol. There are two errors in the command:
The correct command should be:
docker service create --name dns-cache --publish-add mode=ingress,target=53,published=53,protocol=udp dns-cache
docker service create | Docker Docs
Does this command create a swarm service that only listens on port 53 using the UDP protocol?
Solution. 'docker service create -name dns-cache -p 53:53 -constraint networking.protocol.udp=true dns-cache"
Answer : B
docker service create --name dns-cache \
--publish published=53,target=53,protocol=udp,mode=host \
--mode global \
--network host \
dns-cache
1: docker service create | Docker Docs