Dell EMC D-PST-DY-23 Dell PowerStore Deploy 2023 Exam Practice Test
SIMULATION
create an SMB NAS server in the PowerStore simulator using the provided information.
Here's the information that is given:
NAS and SMB computer name: payrollserver
Network Interface: BaseEnclosure-bond1
IP address: 192.168.2.20
Subnet: /24
Gateway: 192.168.2.254
VLAN: 1504
AD/DNS: 192.168.2.50
Windows domain name: company.com
Domain administrator credentials: (presumably Administrator/password)

Answer : A
1. Navigate to NAS Servers
Go to Compute > NAS Servers.
Click Add NAS Server.
2. Configure NAS Server Settings
NAS Server Name: Enter payrollserver.
Network Interface: Select BaseEnclosure-bond1.
IP Address: Enter 192.168.2.20.
Subnet: Enter /24.
Gateway: Enter 192.168.2.254.
VLAN: Enter 1504.
AD/DNS: Enter 192.168.2.50.
Windows domain name: Enter company.com.
Domain administrator credentials: Enter Administrator for the username and password for the password.
3. Add the NAS Server
Click Add.
Verification
After the NAS server is created, you can verify its configuration on the NAS Servers page. Check that all the settings are correct.
Key Considerations
Network Connectivity: Ensure that the network interface (BaseEnclosure-bond1) is properly configured and connected to the network with the specified VLAN.
Active Directory Integration: The provided domain administrator credentials will be used to join the NAS server to the Active Directory domain. Make sure these credentials are valid.
DNS Resolution: The AD/DNS server IP address (192.168.2.50) should be reachable from the PowerStore appliance for proper name resolution.
By following these steps, you'll successfully create an SMB NAS server with the specified configuration in the PowerStore simulator.
SIMULATION
Use the simulator to create a new 100 GB volume. Use a category of Other. Associate the new volume with a protection policy that includes a rule that takes a snapshot every hour Monday-Friday and retains it for 5 days.
When you have finished continue to the next question.
Answer : A
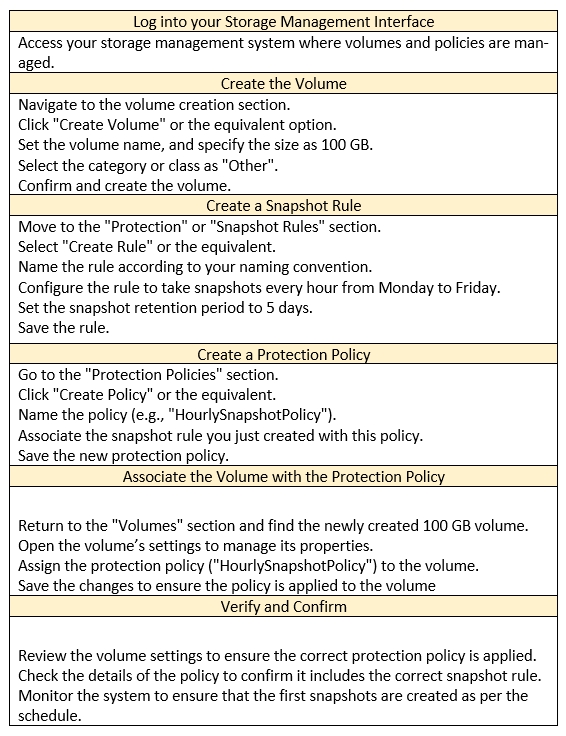
1. Create the Volume
Navigate to Storage > Volumes.
Click + CREATE.
Enter a name for the volume (e.g., 'MyVolume').
Set the volume size to 100 GB.
In the 'Category' dropdown, select Other.
Click Add.
2. Create the Protection Policy
Navigate to Protection > Protection Policies.
Click Add Protection Policy.
Enter a name for the policy (e.g., 'HourlySnapshots').
Click Next.
3. Configure the Snapshot Rule
In the 'Snapshot Rules' section, click Add Rule.
Enter a name for the rule (e.g., 'HourlyRule').
Set the Days to Monday through Friday.
Set the Every field to 1 Hour.
Set Retain to 5 Days.
Click Add.
Click Next.
4. Review and Finish
Review the protection policy summary.
Click Finish.
5. Associate the Protection Policy with the Volume
Navigate back to Storage > Volumes.
Locate the 100 GB volume you created.
Click the More Actions button (three vertical dots) and select Edit.
In the 'Protection Policy' field, select the newly created HourlySnapshots policy from the dropdown list.
Click Save.
Verification
To verify the configuration, go to Protection > Protection Policies.
Select the HourlySnapshots policy.
You should see the configured snapshot rule ('HourlyRule') with the specified settings.
Key Considerations
Snapshot Frequency: The snapshot rule you created will take hourly snapshots of the volume every weekday (Monday to Friday).
Retention Period: The snapshots will be retained for 5 days before being automatically deleted.
Storage Space: Snapshots consume storage space. Ensure you have enough free space to accommodate the snapshots taken based on the frequency and retention period.
By following these steps, you'll successfully create a 100 GB volume, configure a protection policy with the specified snapshot rule, and associate the policy with the volume, fulfilling the requirements of the simulation task.
SIMULATION
A storage admin is setting up a new protection policy with only snapshot rule for a new file system in PowerStore.
The administrator is given the below parameters.
Use the simulator to perform the configuration task.
When you have finished continue to the next question.
Answer : A
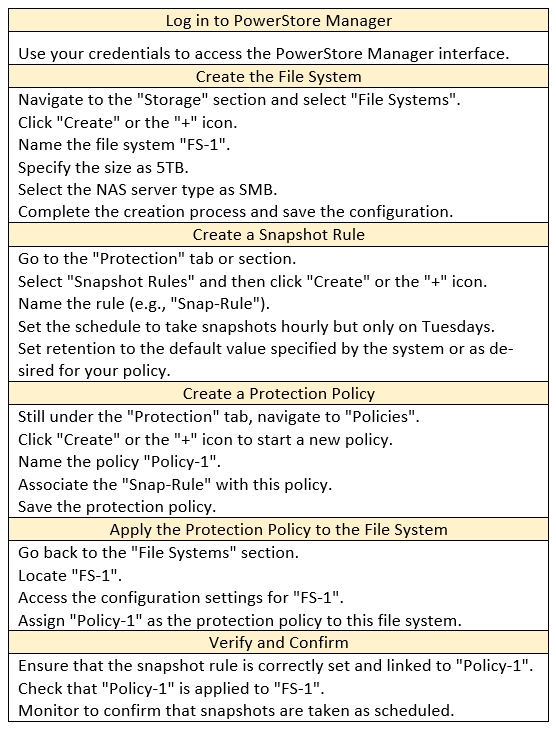
1. Create the File System
Navigate to Storage > File Systems.
Click Add File System.
Enter the file system name: FS-1
Set the file system size to 5 TB.
Select the appropriate NAS Server (SMB-NAS Server in this case).
Click Add.
2. Create the Protection Policy
Navigate to Protection > Protection Policies.
Click Add Protection Policy.
Enter the policy name: Policy-1
Click Next.
3. Configure the Snapshot Rule
In the 'Snapshot Rules' section, click Add Rule.
Enter a name for the rule (e.g., 'Snap-Rule').
Set the Days to Tuesday.
Set the Every field to 1 Hour.
Ensure that Retention is set to the default value.
Click Add.
Click Next.
4. Review and Finish
Review the protection policy summary.
Click Finish.
5. Apply the Protection Policy to the File System
Navigate back to Storage > File Systems.
Locate the FS-1 file system.
Click the More Actions button (three vertical dots) and select Edit.
In the 'Protection Policy' field, select the newly created Policy-1 from the dropdown list.
Click Save.
Verification
To verify the configuration, go to Protection > Protection Policies.
Select Policy-1.
You should see the configured snapshot rule ('Snap-Rule') with the specified settings.
Key Considerations
Default Retention: The default retention for snapshots in PowerStore will vary depending on your system configuration. Ensure that the default retention meets your data protection needs.
Snapshot Schedule: The snapshot rule you created will take hourly snapshots of the file system every Tuesday.
By following these steps, you'll successfully create the protection policy with the specified snapshot rule and apply it to the new file system, meeting all the requirements of the simulation task.
SIMULATION
An administrator received a request to provision a new test dev volume.
Use the simulator to provision a volume of 50 GB for their application team. Use a category of Other. The volume performance must not impact the production I/O when the system is heavily loaded.
When you have finished continue to the next question.
Answer : A

1. Create the Volume
Navigate to Storage > Volumes.
Click + CREATE.
Enter the volume name (e.g., 'TestDevVolume').
Set the volume size to 50 GB.
In the 'Category' dropdown, select Other.
Important: Under 'Advanced Settings,' locate the 'Performance' section and set the Workload Type to Low. This will ensure that the volume's performance has minimal impact on production I/O, especially during periods of heavy system load.
Click Add.
Verification
After creating the volume, you can verify its settings on the Volumes page. Check that the size, category, and workload type are correctly configured.
Key Considerations
Workload Type: The 'Low' workload type setting is crucial in this scenario. It prioritizes production I/O over the test/dev volume, preventing performance contention.
Performance Monitoring: It's a good practice to monitor the system's performance after provisioning the volume, especially during peak usage, to ensure that the production workloads are not negatively affected.
By following these steps, you'll successfully provision a 50 GB volume for the application team with the appropriate performance settings to avoid impacting production I/O. This meets the requirements of the simulation task.
SIMULATION
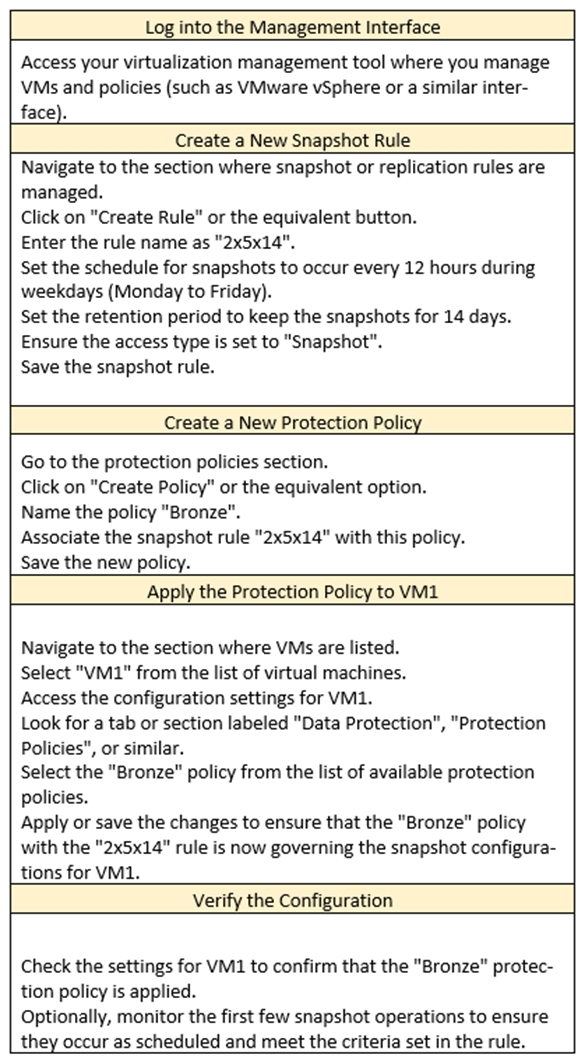
An administrator must configure a new protection policy for an existing VM with the following parameters.
Rule Name: 2x5x14
Days: M-F
Every: 12 Hours
Retention: 14 Days
Access Type: Snapshot
Policy
Name: Bronze
Snap Rule: 2x5x14
Apply the policy to VM1.
When you have finished continue to the next question.
Answer : A
A storage administrator has configured a VNX2 as a remote system.
Which Import External Storage migration architectural components are now established?
Answer : B
A customer must configure two PowerStore clusters with these requirements:
Two PowerStore T appliances in each cluster.
Configure file replication between the clusters.
What is the minimum number of management subnet IPs required in each cluster to complete the configuration on each site?
Answer : D
IP Address Requirements for PowerStore T Appliances
Management IP: Each PowerStore T appliance requires one management IP address for initial configuration and ongoing management.
Cluster IP: Each PowerStore cluster requires one cluster IP address for internal communication between the appliances within the cluster.
File Mobility Network (FMN) IPs: For file replication, each PowerStore cluster needs three FMN IP addresses. These are dedicated IPs used for replication traffic between clusters.
Calculating the Total Number of IPs
Since the scenario involves two PowerStore T appliances in each cluster, let's calculate the IP addresses needed per cluster:
2 appliances x 1 management IP per appliance = 2 management IPs
1 cluster IP
3 FMN IPs
Total: 2 + 1 + 3 = 6 IPs
However, there's a crucial detail:
Additional IP for File Replication: When configuring file replication, an additional IP address is required on the source cluster for the destination cluster to connect to. This is used for the replication relationship and communication.
Therefore, the final count is:
Source Cluster: 6 IPs + 1 additional IP = 7 IPs
Target Cluster: 6 IPs = 6 IPs
Since the question asks for the minimum number of IPs in each cluster to complete the configuration, the answer is 7 IPs.
Dell PowerStore Reference
PowerStore: Networking Guide for Storage Services: This guide provides detailed information about IP address requirements for different PowerStore configurations, including file replication. You can find the latest version on the Dell Support site.
PowerStore: Replication Technologies - Overview and Prerequisites: This document outlines the requirements for configuring replication, including the need for additional IP addresses for the File Mobility Network.
Understanding these IP address requirements is crucial for proper network planning and configuration in PowerStore environments, especially when implementing features like file replication.