CompTIA PT0-002 CompTIA PenTest+ Certification Exam Practice Test
Which of the following legal concepts specifically outlines the scope, deliverables, and timelines of a project or engagement?
Answer : D
A penetration tester is configuring a vulnerability management solution to perform a scan of Linux servers on an enterprise network. The client wants to reduce potential disruptions as much as possible. Which of the following types of accounts should the tester use?
Answer : D
A penetration tester is performing a social engineering penetration test and was able to create a remote session. Which of the following social engineering techniques was most likely successful?
Answer : A
Given the following table:
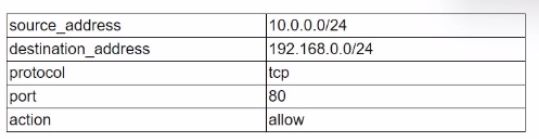
Which of the following data structures would most likely be used to store known-good configurations of firewall rules in a Python script?
Answer : C
During an assessment of a web application, a penetration tester would like to test the application for blind SQL injection. Which of the following techniques should the penetration tester perform next?
Answer : B
During an assessment, a penetration tester was able to access the organization's wireless network from outside of the building using a laptop running Aircrack-ng. Which of the following should be recommended to the client to remediate this issue?
Answer : B
Directional antennas can limit the signal range to reduce unauthorized access from outside the building. Other options, such as WEP, are outdated and insecure, and stopping SSID broadcast does not prevent network access. This aligns with CompTIA Pentest+ objectives under wireless security and hardening techniques.
A penetration tester developed the following script:
bash
Copy code
for ip in $(seq 1 254);
do echo $(echo "192.168.15.$ip ") $(host 192.168.15.$ip dns.company.com | grep "domain name pointer")
done | grep "domain name pointer" | cut -d" " -f1,6
Which of the following best explains the purpose of this script?
Answer : A
The script queries DNS records for hostnames corresponding to IP addresses in the 192.168.15.0/24 subnet. It uses host to resolve domain names and extracts relevant results, aligning with CompTIA Pentest+ objectives on information gathering and network enumeration.