CompTIA CS0-003 CompTIA Cybersecurity Analyst (CySA+) Exam Practice Test
A SOC manager reviews metrics from the last four weeks to investigate a recurring availability issue. The manager finds similar events correlating to the times of the reported issues.
Which of the following methods would the manager most likely use to resolve the issue?
Answer : B
Comprehensive and Detailed
Root Cause Analysis (RCA) is the best approach to identify and resolve the underlying cause of recurring incidents. It involves a systematic investigation of logs, configurations, and operational data to pinpoint the reason behind persistent security issues.
Option A (Vulnerability assessment) helps identify security weaknesses but does not focus on recurring operational issues.
Option C (Recurrence reports) track patterns but do not resolve the root cause.
Option D (Lessons learned) is valuable but is typically a post-mortem discussion rather than an investigative method.
Thus, B is the correct answer, as root cause analysis is the best approach for diagnosing recurring availability issues.
Which of the following best describes the importance of KPIs in an incident response exercise?
Answer : C
Comprehensive and Detailed
Key Performance Indicators (KPIs) in incident response exercises help organizations prioritize improvements by measuring response effectiveness, containment success, and recovery speed. This ensures that resources are focused on the most critical areas for enhancement.
Option A (Personal performance tracking) is more relevant to HR evaluations rather than cybersecurity operations.
Option B (Describing incident resolution) is important but does not define future priorities.
Option D (Identifying tools to use) is useful but not the primary function of KPIs.
Thus, C is the correct answer, as KPIs help teams identify the most urgent areas for improvement.
A security analyst is reviewing a recent vulnerability scan report for a new server infrastructure. The analyst would like to make the best use of time by resolving the most critical vulnerability first. The following information is provided:
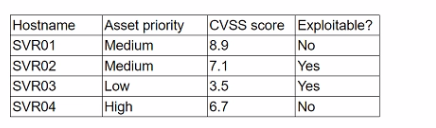
Which of the following should the analyst concentrate remediation efforts on first?
Answer : B
SVR02 has a CVSS score of 7.1 and is exploitable, making it the highest priority for remediation.
SVR01 (CVSS 8.9) is not exploitable, so it is a lower risk.
SVR03 (CVSS 3.5) is exploitable but has a lower severity than SVR02.
SVR04 (CVSS 6.7) is not exploitable, reducing its urgency.
Thus, B (SVR02) is the correct answer, as it presents the highest immediate risk.
Several incidents have occurred with a legacy web application that has had little development work completed. Which of the following is the most likely cause of the incidents?
Answer : C
Outdated libraries in a legacy web application introduce security vulnerabilities, as they lack modern patches and contain known exploits.
Option A (Misconfigured WAF) can contribute to security issues but is not inherent to legacy applications.
Option B (Data integrity failure) is a potential impact but not a direct cause of recurring incidents.
Option D (Insufficient logging) affects detection, but the root cause is insecure, outdated components.
Thus, C (Outdated libraries) is the correct answer, as legacy applications frequently suffer from unpatched vulnerabilities.
An analyst suspects cleartext passwords are being sent over the network. Which of the following tools would best support the analyst's investigation?
Answer : C
Wireshark is a packet capture and analysis tool that allows analysts to inspect network traffic and detect cleartext credentials sent over protocols like HTTP, FTP, and Telnet.
Option A (OpenVAS) is a vulnerability scanner, not a network analysis tool.
Option B (Angry IP Scanner) identifies active hosts, but does not analyze packet contents.
Option D (Maltego) is used for OSINT and network reconnaissance, not packet inspection.
Thus, C (Wireshark) is the correct answer, as it captures and analyzes network packets to identify unencrypted passwords.
Which of the following best explains the importance of utilizing an incident response playbook?
Answer : B
Incident response playbooks provide a structured step-by-step guide for handling security incidents. They define actions to take when specific threat indicators or events occur, ensuring a coordinated and consistent response.
Option A (Prioritizing business-critical assets) relates more to disaster recovery (DR) than incident response.
Option C (Documenting asset management) is part of IT governance, not incident response.
Option D (Defining DR sites) falls under business continuity planning, not real-time incident handling.
Thus, B is the best answer, as playbooks are designed to trigger appropriate responses to incidents.
During a training exercise, a security analyst must determine the vulnerabilities to prioritize. The analyst reviews the following vulnerability scan output:
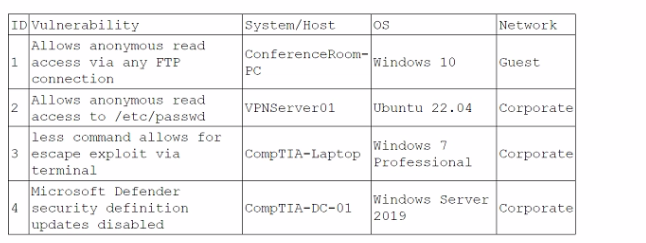
Which of the following issues should the analyst address first?
Answer : A
Allowing anonymous read access to /etc/passwd is a critical vulnerability because it can expose user account details, aiding attackers in password cracking and privilege escalation.
Option B (Anonymous FTP access) is a risk, but /etc/passwd exposure is more critical as it directly affects user authentication.
Option C (Defender updates disabled) is important, but it does not present an immediate attack vector like credential exposure.
Option D (less escape exploit) is significant, but it requires user interaction, making it less immediate than a global credential leak.
Thus, A is the correct answer, as it represents an immediate, high-impact security risk.