CheckPoint 156-315.81 Check Point Certified Security Expert - R81.20 Exam Practice Test
How many policy layers do Access Control policy support?
Answer : A
Therefore, the correct answer is A. The Access Control policy supports two policy layers.
1, Policy Layers in R80.x - Check Point CheckMates
2, Access Control policies, layers, and rules | Check Point Firewall ...
3, Chapter 8: Introduction to Policies, Layers, and Rules - Check Point ...
You can access the ThreatCloud Repository from:
Sieve is a Cyber Security Engineer working for Global Bank with a large scale deployment of Check Point Enterprise Appliances Steve's manager. Diana asks him to provide firewall connection table details from one of the firewalls for which he is responsible. Which of these commands may impact performance briefly and should not be used during heavy traffic times of day?
Answer : B
The command that may impact performance briefly and should not be used during heavy traffic times of day is fw tab -t connections. This command displays all the entries in the connections table, which can be very large and consume a lot of CPU resources. The other commands are less intensive and can be used safely. The command fw tab -t connections -s displays only the statistics of the connections table, such as number of entries, peak size, etc. The command fw tab -t connections -c clears all the entries in the connections table. The command fw tab -t connections -f displays only the entries that match a filter expression. Reference: [fw tab Command]
Which of the following is an authentication method used for Identity Awareness?
Answer : C
Captive Portal is one of the authentication methods used for Identity Awareness, which is a feature of Check Point that enables you to identify users and apply security policy rules based on their identity. Captive Portal redirects users to a web page where they can enter their credentials and be authenticated by an external server, such as LDAP or RADIUS. After authentication, users can access the Internet and corporate resources according to the security policy rules that apply to their identity.
The references are:
Machine Authentication & Identity Awareness - Check Point CheckMates
Check Point Certified Security Expert R81.20, slide 13
Check Point R81 Identity Awareness Administration Guide, page 9
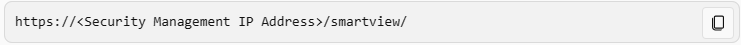
How can SmartView application accessed?
Answer : C
SmartView is a web-based application that allows you to view and analyze logs, reports, and events from multiple Check Point products. You can access SmartView by using the following URL:
What feature allows Remote-access VPN users to access resources across a site-to-site VPN tunnel?
Answer : D
The 'Network Access VPN Domain' feature allows remote-access VPN users to access resources across a site-to-site VPN tunnel. This feature allows remote users to securely access internal network resources as if they were physically connected to the network. This is achieved by adding the remote-access VPN users to a 'VPN Domain' that has access to the internal network resources via a site-to-site VPN tunnel. This VPN Domain is also referred to as a 'Network Access VPN Domain'.
Which of the following is a task of the CPD process?
Answer : B
The task of the CPD process that is listed among the options is transferring messages between Firewall processes. The CPD process is responsible for inter-process communication between various Check Point daemons, such as FWM, FWD, CPD, CPM, etc. It also handles licensing and status report requests from other processes. The other tasks are performed by different processes. The task of invoking and monitoring critical processes and attempting to restart them if they fail is performed by the WatchDog process. The task of log forwarding is performed by the FWD process. The task of processing most traffic on a security gateway is performed by the Firewall kernel module. Reference: [Check Point Processes and Daemons]