Amazon SCS-C02 AWS Certified Security - Specialty Exam Practice Test
An AWS account includes two S3 buckets: bucketl and bucket2. The bucket2 does not have a policy defined, but bucketl has the following bucket policy:
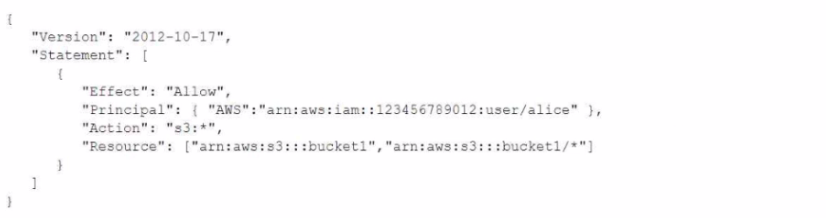
In addition, the same account has an 1AM User named "alice", with the following 1AM policy.
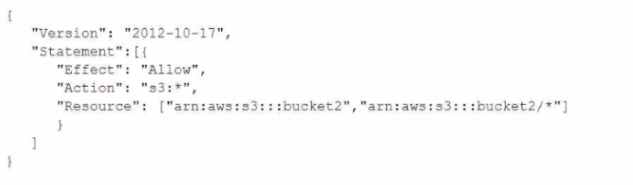
Which buckets can user "alice" access?
Answer : C
A company uses Amazon Cognito for external user authentication for a web application. External users report that they can no longer log in to the application. What is the FIRST step that a security engineer should take to troubleshoot the problem?
Answer : C
A company runs a global ecommerce website that is hosted on AWS. The company uses Amazon CtoudFront to serve content to its user base. The company wants to block inbound traffic from a specific set of countries to comply with recent data regulation policies.
Which solution will meet these requirements MOST cost-eftectively?
Answer : C
A company has configured a gateway VPC endpoint in a VPC. Only Amazon EC2 instances that reside in a single subnet in the VPC can use the endpoint The company has modified the route table for this single subnet to route traffic to Amazon S3 through the gateway VPC endpoint. The VPC provides internet access through an internet gateway.
A security engineer attempts to use instance profile credentials from an EC2 instance to retrieve an object from the S3 bucket, but the attempt fails. The security engineer verifies that the EC2 instance has an 1AM instance profile with the correct permissions to access the S3 bucket and to retrieve objects. The security engineer also verifies that the S3 bucket policy is allowing access properly. Additionally, the security engineer verifies that the EC2 instance's security group and the subnet's network ACLs allow the communication.
What else should the security engineer check to determine why the request from the EC2 instance is failing?
Answer : D
Amazon CtoudWatch Logs agent is successfully delivering logs lo the CloudWatch Logs service. However, logs stop being delivered after the associated log stream has been active for a specific number of hours.
What steps are necessary to identify the cause of this phenomenon? (Select TWO.)
Answer : A, B
A company is running workloads on AWS. The workloads are in separate AWS accounts for development, testing, and production. All the company's developers can access the development account. A subset of the developers can access the testing account and the production account.
The company is spending too much time managing individual credentials for every developer across every environment. A security engineer must implement a more scalable solution that the company can use when a developer needs different access. The solution must allow developers to access resources across multiple accounts. The solution also must minimize credential sharing.
Which solution will meet these requirements?
Answer : C
A security engineer is investigating a malware infection that has spread across a set of Amazon EC2 instances. A key indicator of the compromise is outbound traffic on TCP port 2905 to a set of command and control hosts on the internet.
The security engineer creates a network ACL rule that denies the identified outbound traffic. The security engineer applies the network ACL rule to the subnet of the EC2 instances. The security engineer must identify any EC2 instances that are trying to communtcate on TCP port 2905.
Which solution will identify the affected EC2 instances with the LEAST operational effort?
Answer : B